2 Overview of Oracle Identity and Access Management Lifecycle Tools for Patching
This chapter introduces the patching tools that are part of the Oracle Identity and Access Management Lifecycle Tools. It also describes the concepts and terminology related to these tools.
This chapter contains the following sections:
2.1 Introduction to Patching Oracle Identity and Access Management Using Lifecycle Tools
The Oracle Identity and Access Management Lifecycle Tools can be used to patch an Oracle Identity and Access Management environment in an automated and orchestrated manner. The tools perform the following functions:
-
Determine where and when, in an environment, each patch needs to be applied during a patch session.
-
Generate a patch plan that lists in detail the steps of the session.
-
Verify patch prerequisites against all hosts while servers are running.
-
Stop servers to apply patches, apply the required patches, and restart the servers.
-
Apply configuration or other artifact changes automatically for those patches that include these changes.
The following tools are used for automated patching of an Oracle Identity and Access Management environment:
-
Patch Manager
The Oracle Identity and Access Management Patch Manager generates the patch plan, and controls and provides the status of the resulting patch session.
-
Patcher
The Oracle Identity and Access Management Patcher executes the steps in a patch session, as listed in the patch plan.
Figure 2-1 shows the process of patching an Oracle Identity and Access Management environment using the Lifecycle Tools.
Figure 2-1 Patching Oracle Identity and Access Management Using Lifecycle Tools
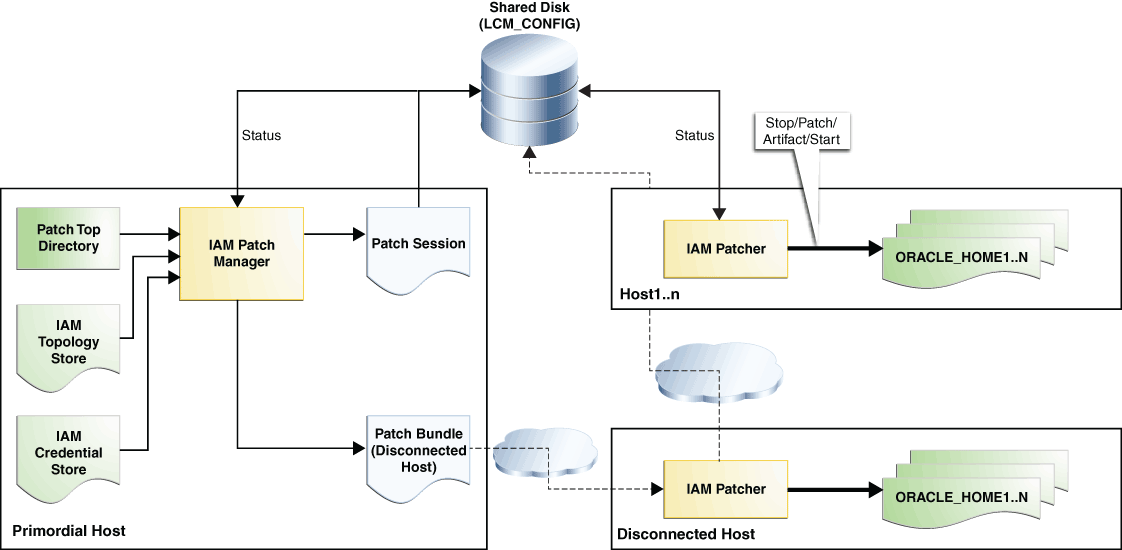
Description of "Figure 2-1 Patching Oracle Identity and Access Management Using Lifecycle Tools"
2.1.1 Products Supported
The Oracle Identity and Access Management Patcher patches all of the products that are supported by the Oracle Identity and Access Management Deployment Tool.
For the complete list of supported products, see the Oracle Fusion Middleware Deployment Guide for Oracle Identity and Access Management.
2.2 Terminology
The following terms are used in the document:
A patch is a small collection of files that are applied over an existing installation. Patches are associated with particular versions of Oracle products. When applied to the correct version of an installed product, patches result in a slightly modified version of the product.
Interim patches make bug fixes available to customers, in response to specific bugs. They require a particular base release or patch set to be installed before you can apply them. These patches are not versioned, and the bug fixes they contain are made generally available in a future patch set as well as the next product release.
For patching an environment, an Identity and Access Management deployment is split into discrete stacks, each containing certain products, Oracle WebLogic Server domains, and server instances.
These stacks include:
-
Directory
-
Access
-
Identity
-
Web
During the generation of a patch plan, the patches provided are mapped to one or more stacks. Most products belong to a single stack, but there might be exceptions. For instance, Oracle WebLogic Server patches are applied across both the Access and Identity stacks, while common patches are applied across all stacks.
The topology store is an XML file that is generated by the Deployment Tool when the environment is created. It contains extensive physical and logical details about the environment, and is used by the Lifecycle Tools in applying patches.
The IAM_TOP directory contains the binary product installations. This directory is either located on a mounted network share or on a local disk, depending on how the Oracle Identity and Access Management environment is created. For information about creating an environment, see Oracle Fusion Middleware Deployment Guide for Oracle Identity and Access Management.
The IAM_LCM_TOP directory contains the installation of the Oracle Identity and Access Management Lifecycle Tools, including the Patch Manager and Patcher executables, and various configuration files that drive the behavior of the tools.
The LCM_CONFIG directory contains additional configuration files, including the topology store, runtime data, and log information for the Oracle Identity and Access Management Lifecycle Tools. This includes the patch session and the plan files that are human-readable.
A patch top directory (PATCH_TOP) contains unzipped patches that are sorted by product. The Patch Manager scans information in the PATCH_TOP directory to read the patches, validate the files, and after validating, include these patches in the patch plan generated.
2.3 Oracle Identity and Access Management Patch Manager
The Oracle Identity and Access Management Patch Manager is as administrative tool that generates a patch plan and controls the patch session. You can run the Patch Manager only from the primordial host of the deployment. The Patch Manager does not execute any actions such as stopping or starting servers, and so on. All actions affecting a deployment are executed by the Patcher.
2.3.1 Patch Session
All automated patching occurs within a patch session. You can create a patch session to apply one or more patches, or to rollback patches that are already applied to a product.
Note:
You can stop a patch session that is in progress, by executing theabort command.The Patch Manager maintains a session file in the location LCM_CONFIG/patch/session/ to track the patch process coordination with the Patcher. The session file contains the current status of the patch session. For more information about the status of a patch session, see Table 4-5.
At any given time, only one active patch session can exist in the deployment.
2.3.2 Patch Plan
A patch plan, which is created by the Patch Manager, consists of a set of comprehensive steps to patch the deployment.
2.3.2.1 Phases of a Patch Plan
A patch plan consists of the following three phases:
-
Patch Apply Prerequisite Phase (all services running)
The prerequisite checks are executed, but no changes are made to the deployment. This phase can be executed before you plan your system downtime, and apply patches. If any issue is found, it can be addressed immediately. This enables you to apply the patches smoothly during downtime.
-
Patch Pre-Apply Phase (all services down)
All servers that need to be shut down to apply patches are stopped. This action is deployment-aware. For example, if the patch top consists solely of an Oracle Access Manager patch, you need not stop every server instance. Only Oracle HTTP Server and Oracle Identity Manager, which depend on Oracle Access Manager, and Oracle Access Manager itself, are stopped. Oracle Unified Directory remains up during the execution of the plan. This ensures that the required downtime is minimized.
-
Patch Apply Phase (limited services available)
Patches are applied, any artifact changes related to the patches are executed, and servers are started.
2.3.2.2 Generating a Patch Plan
The Patch Manager generates the patch plan as follows:
-
A patch top directory containing patches, classified by each product subdirectory, is provided to the tool. Ensure that all downloaded patches have been unzipped, and that any zip files for those have been moved out of the patch top directory.
-
The patch top directory is scanned and initial validations are performed.
-
The deployment topology is read and analyzed.
-
The information obtained in Step 2 and Step 3 is combined, and a patch plan is generated using the
OPlanutility. The patch plan is generated in HTML, plain-text and binary format, which is used for execution. -
The log messages of the Patch Manager are written to the
logdirectory inLCM_CONFIG:
The administrator needs to manually run the Patch Manager to begin a patching session. For information about how to run the Patch Manager, see Section 4.2.
2.4 Oracle Identity and Access Management Patcher
The Oracle Identity and Access Management Patcher is an execution engine that completes the steps in a patch session as listed in the patch plan, on each host in the deployment. The Patcher executes only those steps that are applicable to a specific host in a deployment. After completing the steps on a specific host, the Patcher displays a message indicating the next host on which the Patcher needs to be executed, and exits.
You need to execute the Patcher multiple times on a specific host, if required, during the execution of a patch plan, as different phases of the patch plan are executed.