Completing Equation Engine Setup
You must set up Equation Engine before using it. This section discusses how to:
Recompile all equations prior to using Equation Engine.
Verify equation security objects.
Adjust equation security.
Create a tree hierarchy.
Set up security authorizations.
|
Page Name |
Definition Name |
Navigation |
Usage |
|---|---|---|---|
|
Run An Equation |
SCC_EQTN_RUN_CNTL |
|
Compile all equations prior to using Equation Engine. |
|
User Profile Types |
PSOPRALIASTYPE |
|
Verify equation security objects. |
|
Tree Definitions and Properties |
PSTREEDEFN |
Click the Tree Definition link on the Tree Manager page. |
Adjusting equation security. |
|
Tree Manager |
PSTREEMGR |
Tree Manager, Tree Manager |
Create a tree hierarchy. |
|
User Profiles |
PSOPRALIAS |
|
Set up security authorizations. |
Access the Run An Equation page ().
Image: Run An Equation page
This example illustrates the fields and controls on the Run An Equation page. You can find definitions for the fields and controls later on this page.
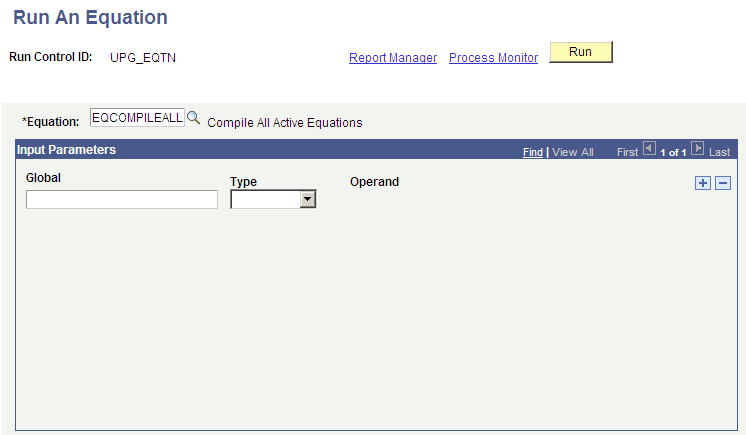
Note: Anyone using Equation Engine in your organization must complete the steps in this section to recompile equations.
To recompile equations:
Enter the equation EQCOMPILEALL.
Leave the Global and Type fields blank.
Click the Run button.
Click the OK button on the Process Scheduler Request page.
Verify that the job ran successfully by checking the Process Monitor.
Access the User Profile Types page for EQD ().
Note: Financial Aid and Student Financials administrators must complete the steps in this section to verify equation security objects.
Image: User Profile Types page (EQD)
This example illustrates the fields and controls on the User Profile Types page (EQD). You can find definitions for the fields and controls later on this page.
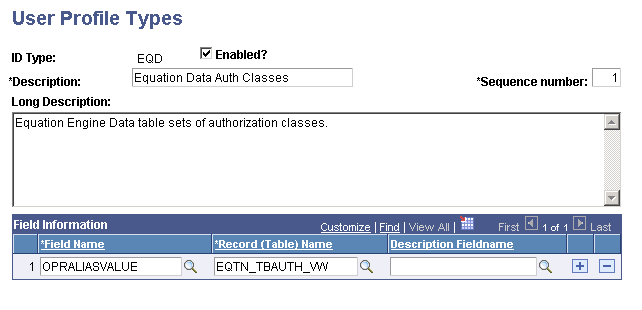
Verify that the information that appears matches the information provided in the preceding page.
Search the following ID types:
EQN
EQS
EQX
Access the User Profile Types page for EQN ().
Image: User Profile Types page (EQN)
This example illustrates the fields and controls on the User Profile Types page (EQN). You can find definitions for the fields and controls later on this page.
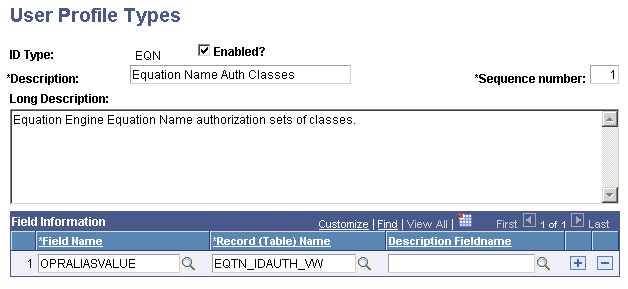
Verify that the information that appears matches the information provided in the preceding page.
Access the User Profile Types page for EQS ().
Image: User Profile Types page (EQS)
This example illustrates the fields and controls on the User Profile Types page (EQS). You can find definitions for the fields and controls later on this page.
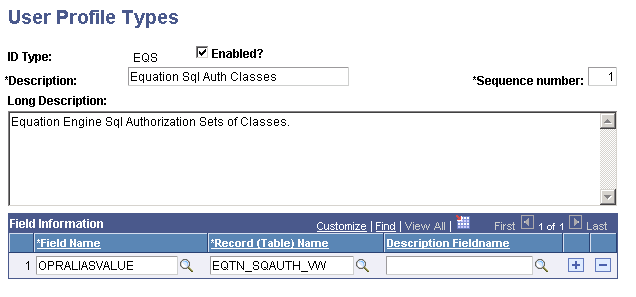
Verify that the information that appears matches the information provided in the preceding page.
Access the User Profile Types page for EQX ().
Image: User Profile Types page (EQX)
This example illustrates the fields and controls on the User Profile Types page (EQX). You can find definitions for the fields and controls later on this page.
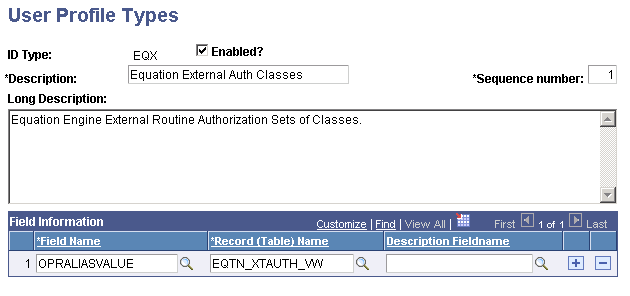
Verify that the information that appears matches the information provided in the preceding page.
Note: Do not use the EQA ID type at this time.
Access the Tree Definitions and Properties page for EQTN_IDAUTH_TREE ( and click theTree Definition link on the Tree Manager page).
Note: Financial Aid and Student Financials administrators must complete the steps in this section to adjust equation security.
Image: Tree Definitions and Properties page (EQTN_IDAUTH_TREE)
This example illustrates the fields and controls on the Tree Definitions and Properties page (EQTN_IDAUTH_TREE). You can find definitions for the fields and controls later on this page.
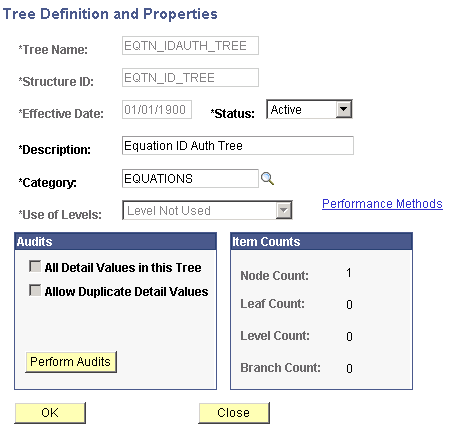
Verify that the information that appears matches the information provided in the preceding page.
Search for the following tree names:
EQTN_SQAUTH_TREE
EQTN_TBAUTH_TREE
EQTN_XAUTH_TREE
If you need to create any of these trees, also use the following page elements :
|
Field or Control |
Definition |
|---|---|
| SetID |
(blank) |
| Set control value |
(blank) |
| Tree branch |
(blank) |
| Valid tree |
Valid tree. |
| Tree root node |
PUBLIC |
Access the Tree Definitions and Properties page for EQTN_SQAUTH_TREE ( and click the Tree Definition link on the Tree Manager page).
Image: Tree Definitions and Properties page (EQTN_SQAUTH_TREE)
This example illustrates the fields and controls on the Tree Definitions and Properties page (EQTN_SQAUTH_TREE). You can find definitions for the fields and controls later on this page.
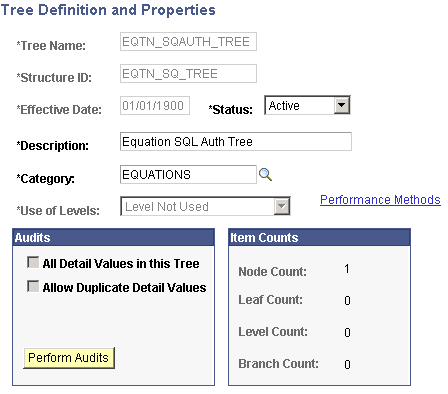
Verify that the information that appears matches the information provided in the preceding page.
Access the Tree Definitions and Properties page for EQTN_TBAUTH_TREE ( and click the Tree Definition link on the Tree Manager page).
Image: Tree Definitions and Properties page (EQTN_TBAUTH_TREE)
This example illustrates the fields and controls on the Tree Definitions and Properties page (EQTN_TBAUTH_TREE). You can find definitions for the fields and controls later on this page.
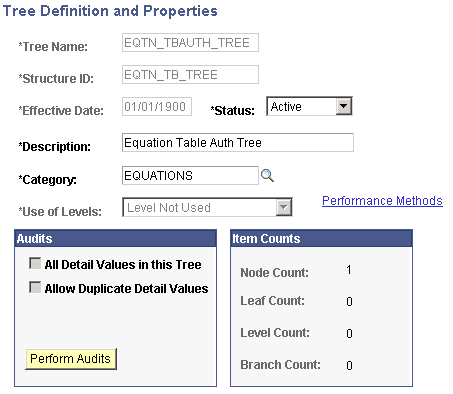
Verify that the information that appears matches the information provided in the preceding page.
Access the Tree Definitions and Properties page for EQTN_XTAUTH_TREE ( and click the Tree Definition link on the Tree Manager page).
Image: Tree Definitions and Properties page (EQTN_XTAUTH_TREE)
This example illustrates the fields and controls on the Tree Definitions and Properties page (EQTN_XTAUTH_TREE). You can find definitions for the fields and controls later on this page.
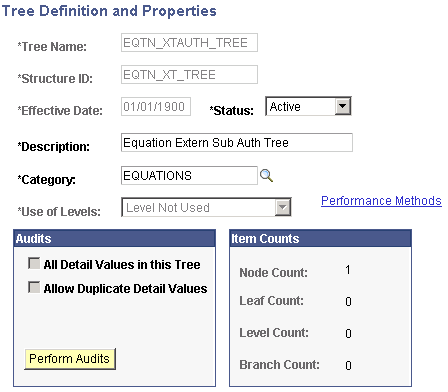
Verify that the information that appears matches the information provided in the preceding page.
Access the Tree Manager page ().
Image: Tree Manager page
This example illustrates the fields and controls on the Tree Manager page. You can find definitions for the fields and controls later on this page.
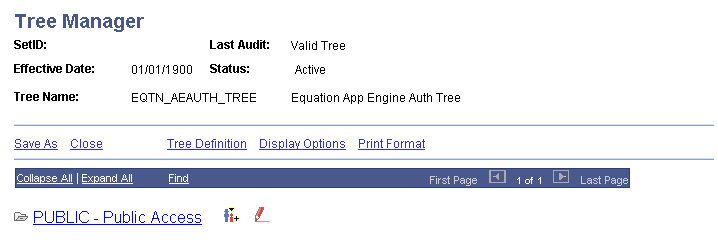
Create a tree hierarchy from the PUBLIC node if one does not already exist for each of the trees. The tree hierarchy should contain a separate node for Financial Aid administrators and a separate node for Student Financials administrators. You can break this down further if you want to limit who can run equations versus who can edit an equation within the groups.
|
Tree Name |
Description |
|---|---|
|
EQTN_IDAUTH_TREE |
Authorizations for editing, viewing, or running equations. |
|
EQTN_SQAUTH_TREE |
Authorizations for editing or running equation SQL. |
|
EQTN_TBAUTH_TREE |
Authorizations for reading tables and view from an equation. |
|
EQTN_XTAUTH_TREE |
Authorizations for running external COBOL routines from an equation. |
Note: Do not use EQTN_AEAUTH_TREE at this time.
Access the Edit Data page (click the Edit Data icon on the Tree Manager page).
Image: Edit Data page
This example illustrates the fields and controls on the Edit Data page. You can find definitions for the fields and controls later on this page.
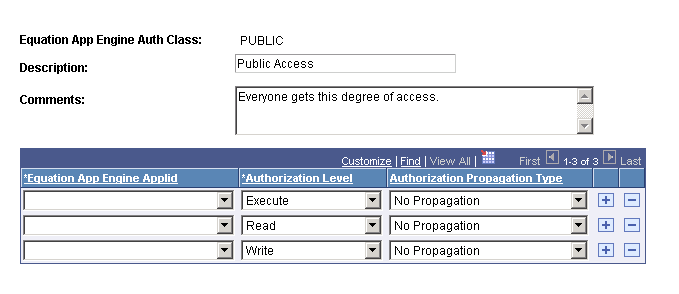
Under each node, add or edit the list of objects and indicate what level of security should be applied to the node.
To do this, click the Edit Data icon (pencil icon) and then insert rows of equation object names and grant appropriate authorization levels.
|
Field or Control |
Definition |
|---|---|
| Execute |
Select the Execute value if the user has the security clearance only to run equations. |
| Read |
Select the Read value if the user has the security clearance to read and run equations. |
| Write |
Select the Write value if the user has the security to write, read, and run equations. |
All tables and views should have only Read access at this time. Equations should have a mix of authorizations depending on the position of the person accessing them. External routines and SQL should have only Execute access.
Note: You should create the node hierarchy and save the tree structure before adding equation object names so that authority propagation can take place.
Objects newly placed within the PUBLIC node should have their access propagated to Append Auth to All Child Nodes.
Save any changes you made to the trees.
Access the User Profiles page ().
Image: User Profiles page: ID tab
This example illustrates the fields and controls on the User Profiles page: ID tab. You can find definitions for the fields and controls later on this page.
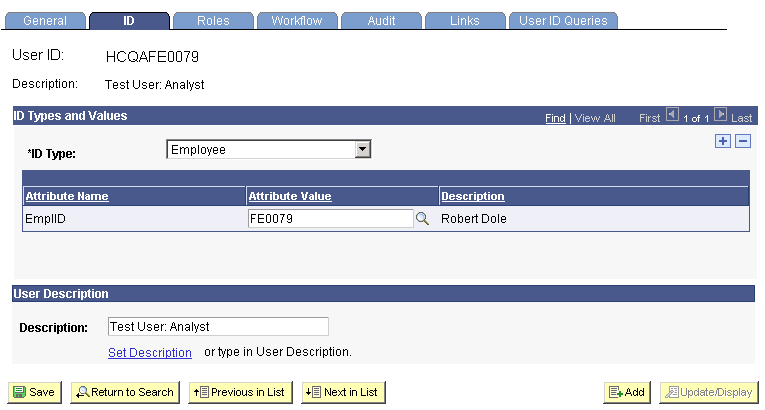
For each person in a department who needs security authorization other than PUBLIC, you must follow these steps:
Enter the person's ID number and access the ID tab.
Enter each of the four EQ ID types in the ID Type and Values fields.
Enter the appropriate Equation Security Tree node name for each of these ID types.
Save the user profile.
See PeopleTools: Security Administration