Equation Engine Security
This section discusses the components of PeopleSoft Equation Engine security and how to implement them at your site.
The following topics describe the components involved in Equation Engine security and how to implement Equation Engine security at your site.
Security Features
Equation Engine security features:
Provide different levels of access (authorizations) to the equation objects based indirectly on the user identification (user ID). The three levels of access are:
Execute.
Read (contains Execute).
Write (contains Execute and Read).
Provide a hierarchy (tree) of classes (user profile values) that are associated with the user ID.
Associate different authorizations with different user profile values.
Maintain the authorizations using the equation security trees.
User IDs and User Profiles
A user signs on to the database with a user ID. The ID is associated with zero or more user profile types, each of which is associated with exactly one user profile value. The types are:
|
Profile Type |
Description |
Controls Access To |
|---|---|---|
|
EQD |
Equation Data Auth Class |
Table and View Data |
|
EQN |
Equation Name Auth Class |
Equations |
|
EQS |
Equation SQL Auth Class |
Callable SQL |
|
EQX |
Equation External Subroutine Auth Class |
External Subroutines |
Each user profile type has a controlling tree that determines the hierarchy of user profile values. For example, the highest root access would be PUBLIC, under which could be FIN AID ADMINS. User ID PS could be associated with FIN AID ADMINS under user profile type EQN.
Another user ID might be associated with PUBLIC. The hierarchy for EQN does not have to be the same as the hierarchy for EQS, EQD, or EQX. Each hierarchy can be different.
You might add a DEVELOPER class for EQN under FIN AID ADMINS in which only one FIN AID ADMINS user is included. You can set this user's access to WRITE, whereas all other FIN AID ADMINS have READ access to equations. Note that read-only access to an equation means that it cannot be viewed or modified from the Equation Engine component. Instead, it can be viewed only from the Equation View component.
You should not modify the user profile types. However, you must modify the user profile values using the tree structures and assign those values to various user IDs as appropriate.
User Profile Values
Just as each user ID in the system is associated with a Permission List (for example, ALLPANLS), each user profile type for each user can have one value associated with it (for example, PUBLIC). Initially, one is provided: PUBLIC. However, you are strongly encouraged to create your own new user profile values using the equation security trees. If a user ID does not have a user profile type and value set for it, then Equation Engine assumes a user profile value of PUBLIC by default.
Equation Security Trees
Use Tree Manager to maintain the equation security trees.
Select The following page shows the Tree Name in Tree Manager.
Image: Tree Manager, Tree Names example
This example illustrates the fields and controls on the Tree Manager, Tree Names example. You can find definitions for the fields and controls later on this page.
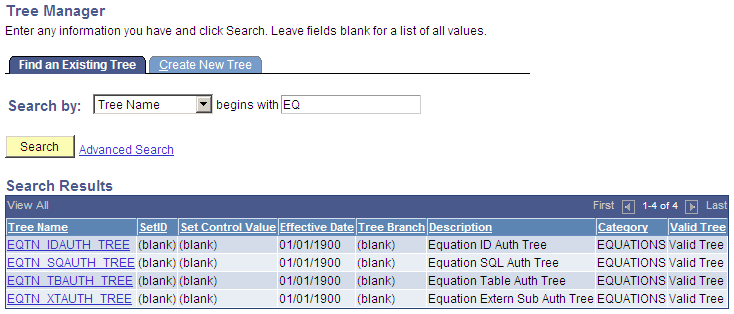
The following page is an example of a view of Public Access in the equation security tree.
Image: Tree Manager page, PUBLIC Access Example
This example illustrates the fields and controls on the Tree Manager page, PUBLIC Access Example. You can find definitions for the fields and controls later on this page.
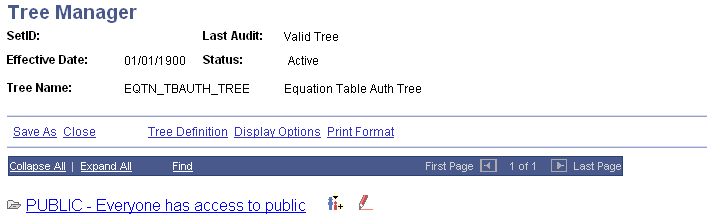
If you click the Insert Child Node icon to the right of PUBLIC and add a new node underneath it, this is the result:
Image: Insert Child Node page
This example illustrates the fields and controls on the Insert Child Node page. You can find definitions for the fields and controls later on this page.
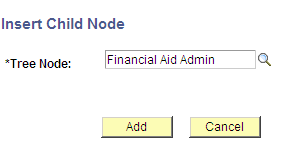
Image: Equation Table Authorization page
This example illustrates the fields and controls on the Equation Table Authorization page. You can find definitions for the fields and controls later on this page.
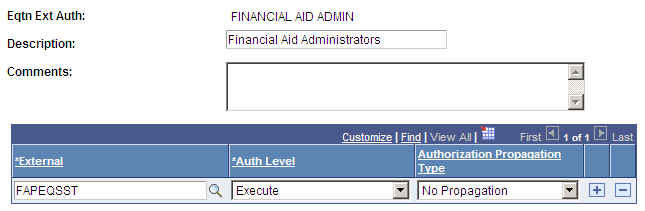
Image: Tree Manager page, Child Node Example
This example illustrates the fields and controls on the Tree Manager page, Child Node Example. You can find definitions for the fields and controls later on this page.
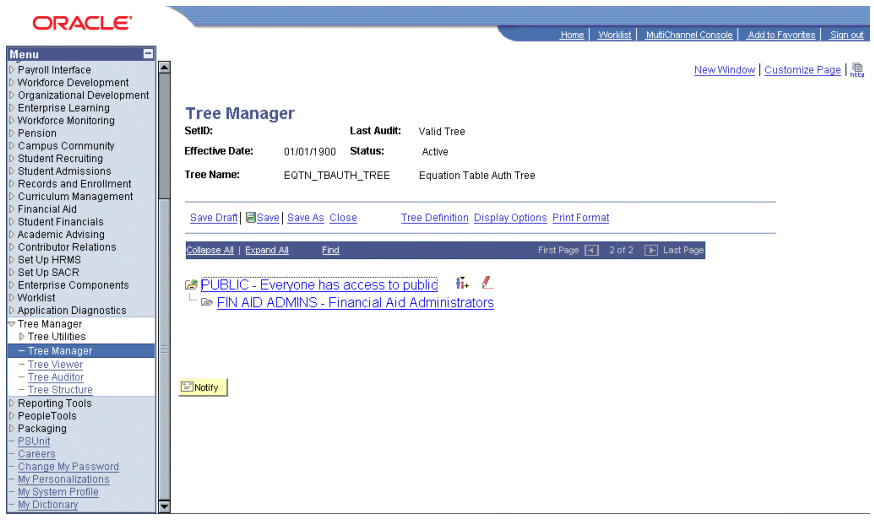
You click a tree node to select it, and then you click the red pencil icon (Edit Data) to view or modify the access settings for the selected tree node.
If you add new nodes here, then these new node names within the tree are added to the list of valid values that can be selectable as user profile type values for the user profile type associated with the tree structure being modified. Design your security tree structure to reflect the security needs within your organization based upon who needs what kind of access to which kinds of equation objects. Only the security administrator should have update access to edit these equation security tree structures and their associated lists of equation objects.
Image: Equation Table Authorization page, Authorization examples
This example illustrates the fields and controls on the Equation Table Authorization page, Authorization examples. You can find definitions for the fields and controls later on this page.
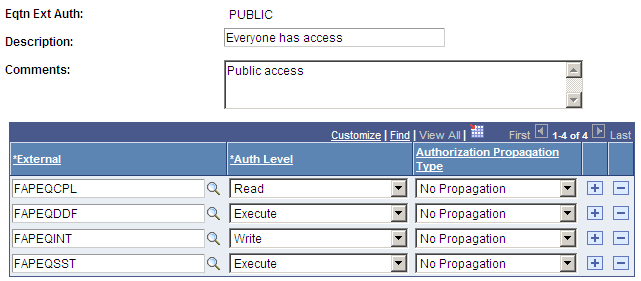
If a table has read authorization, then it can be used in FIND statements and table field references in expressions. If a table has write authorization, then it can also be referenced in the DELETE, INSERT, and UPDATE mass action statements.
To simplify access maintenance, select an Authorization Propagation type from the Authorization Propagation Type drop-down list box.
This table describes the Authorization Propagation Type values:
|
Value |
Description |
|---|---|
|
Append Auth To All Child Nodes |
When you click the Save button, the authorization of the equation object is added to all child nodes of the current node that do not already have an access type assigned. |
|
Delete Auth In All Child Nodes |
When you click the Save button, the authorization of the equation object is removed from all child nodes, regardless of the previous access assigned. |
|
Replace Auth In All Child Nodes |
When you click the Save button, the authorization of the equation object is set within all child nodes, regardless of the previous access assigned. |
If you delete or rename an equation node from the tree manager, the underlying authorizations should be deleted automatically. If they are not, complete these steps to correct the error and to begin an analysis of the problem.
To correct the error, run the Application Engine process named SCC_EQAUTPUR.
Navigate to PeopleTools > Application Engine > Request AE.
Add a run control for SCC_EQAUTPUR, select process frequency Always, and click RUN.
Select your process server, select the process named SCC_EQAUTPUR, and click the OK button.
Navigate to the process monitor and verify that the process ran successfully.
This process purges the authorizations that are no longer associated with any tree nodes.
To analyze the cause of the problem, navigate to PeopleTools > Integration Broker > Service Operations Monitor > Monitoring > Asynchronous Services and complete these steps:
Look in the TREE_MAINT queue.
Verify that all the transactions in the TREE_MAINT queue are at Done status.
Select the Subscription Contracts tab.
Change the Node Name value to the default local node.
Change the Service Operation value to TREE_CHANGE.
Change the Queue Name value to TREE_MAINT.
Select the Done status.
Click the Refresh button.
Click the Details link of the most recent transaction.
The Asynchronous Details page for that transaction appears. The Action Name value should be Equation_Auth_Change_Handler and the status should be Done.
If so, then the orphan equation authorization node leaves should have been automatically purged when the equation authorization node was deleted or renamed in tree manager. If the status of the transaction is not Done, then correct your Application Messaging environment.
Authorization Levels
EQN (user profile type) authorizations of type WRITE permit a user to update an equation. Therefore, the authorization class is used in the search record for the Equations page.
Select Set Up SACR, Common Definitions, Equation Engine, Equation Editor.
Image: Equation Editor Search Results page
This example illustrates the fields and controls on the Equation Editor Search Results page. You can find definitions for the fields and controls later on this page.
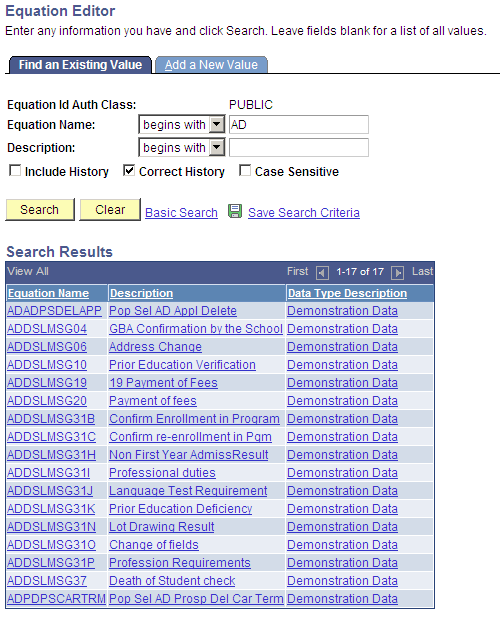
The authorization class pertaining to equation names for the logged-in user ID (in this case, PUBLIC) is already supplied on the search page. When you click the Search button, the system displays a list of equations and equation descriptions that any user with PUBLIC access can update.
Select Set Up SACR, Common Definitions, Equation Engine, Review Equations.
Image: Equation View page
This example illustrates the fields and controls on the Equation View page. You can find definitions for the fields and controls later on this page.
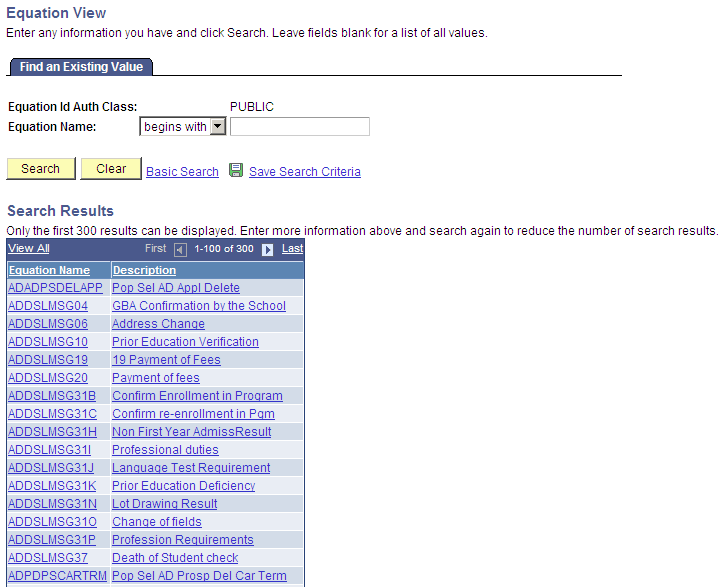
In the Equation View search page, only equations that the user ID has write or read access appear.
In a similar way, the EQD user profile type provides a control point for access to tables and views that you are allowed to read when you create an equation. The EQS user profile type provides controls for determining which callable SQL you can invoke, and the EQX user profile type establishes a control point for determining which external subroutines you can call when you create an equation.
User Profiles
Equation Security is based on the user profile tools construct that comes with tools.
You will probably not modify the user profile type because it is tied to a program logic. However, you are required to change the profile type values within each type, assigning a value for each type for each user ID. The valid type values are the names of the tree nodes associated with the type.
User Profile Types
Each user profile type represents an entire set of user profile values; each user profile type is used for a particular application purpose. Normally, when a user signs on, he or she is assigned to roles and permissions lists, which determine the user's menu access. To assign users to different user profile values that do not necessarily correspond to roles and permission lists, you must use user profile types.
Select PeopleTools, Security, Security Objects, User Profile Types.
Image: User Profile Types page (1 of 2)
This example illustrates the fields and controls on the User Profile Types page (1 of 2). You can find definitions for the fields and controls later on this page.
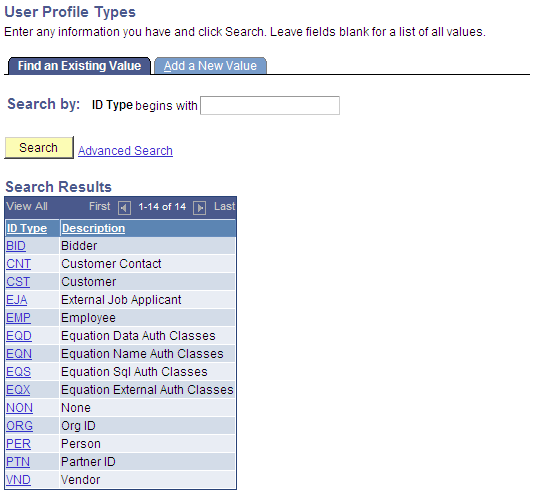
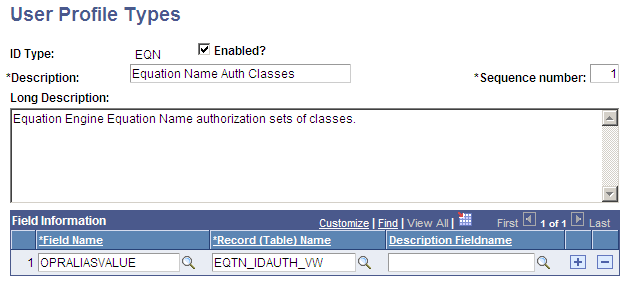
Although you would not change the user profile types, this page shows the profile types for Equation Engine:
Image: User Profile Types page (2 of 2)
This example illustrates the fields and controls on the User Profile Types page (2 of 2). You can find definitions for the fields and controls later on this page.
Access the User Profiles, ID tab ().
Image: User Profile page, ID tab
This example illustrates the fields and controls on the User Profile page, ID tab. You can find definitions for the fields and controls later on this page.
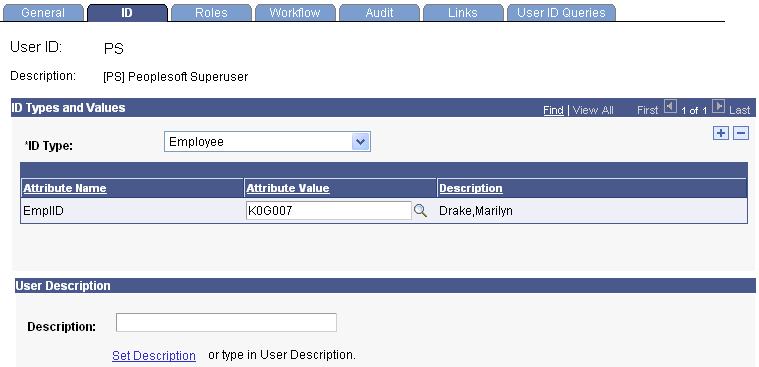
When you select the User Profile ID, the system displays the descriptions shown on the previous page.
On this page, you can add equation user profile types and select a user profile value for each one that you add.