3 Installation Overview
This chapter outlines the planning process for a secure installation and describes several recommended deployment topologies for the systems.
This chapter contains these topics:
3.1 Understand Your Environment
To better understand your security needs, answer the following questions:
Which resources am I protecting?
You can protect many resources in the production environment. The most critical is your JD Edwards World database on the IBM i, which contains information that is both sensitive and critical to the performance of your business. The database information also represents a substantial investment in time and resources to build and maintain. You also must keep your production software secure and reliable. Computing hardware is also a substantial investment, as well as a critical operating resource. Finally, the reputation of your business may rest on the integrity and performance of your computing resources. Consider the resources you want to protect when deciding the level of security you must provide.
From whom am I protecting the resources?
You must protect most of your computing resources from unauthorized access, manipulation, or destruction from both internal and external parties. Employees may represent a security vulnerability as important as an outside hacker. For Web Enablement or Service Enablement, you must protect resources from unauthorized access via the Internet. But should you protect the Web site from the employees on the intranet in your enterprise? Access to highly confidential data or strategic resources should be available to only a few trusted users or system administrators. System administrators may not need access to confidential data. Power users may not need access to some system resources.
What will happen if the protections on strategic resources fail?
In some cases, a fault in your security scheme is easily detected and considered nothing more than an inconvenience. In other cases, a fault might lead to great damage to database information, systems, or resources. Understanding the security ramifications of each resource will help you protect it properly.
What is my overall security approach?
Before starting the process of setting up a specific security configuration, you should make an overall plan of your security environment. How does the IBM i fit into the overall corporate computing environment? How does JD Edwards security work within the IBM i security environment? In each area, the security policy should be upheld with a tactical action plan, and each area should complement the security features of the other, creating a synergistic ”defense in depth”.
3.2 Common Deployment Topologies
The JD Edwards World system runs only on a centralized IBM i server. The Web Enablement feature, however, brings Internet browser-based access to the World system, so some deployment options must be considered. This section describes common architectures for deploying Oracle JD Edwards World products to secure Internet access.
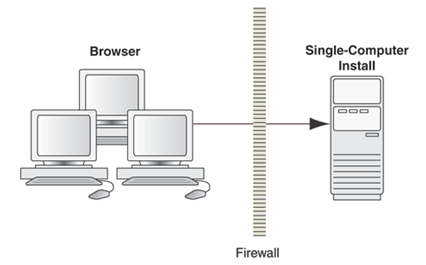
3.2.1 Single-Server Deployment
The following graphic shows one simple deployment architecture that includes browser-based access. In this scenario, users access JD Edwards World via a browser using World Web Enablement, and the Web Enablement (Seagull LegaSuite GUI) server resides on the same server as the World system. The IBM i server is located behind the corporate firewall.
Figure 3-1 Single-Computer Deployment Architecture
Description of ''Figure 3-1 Single-Computer Deployment Architecture''
|
Note: Users may also have access to the IBM i, and thus the World system, using workstation-based software such as 5250 terminal emulation software, communicating to the IBM i via the corporate network (intranet). Some older installations could also have actual 5250 terminals communicating to the IBM i via hard-wired local networks. |
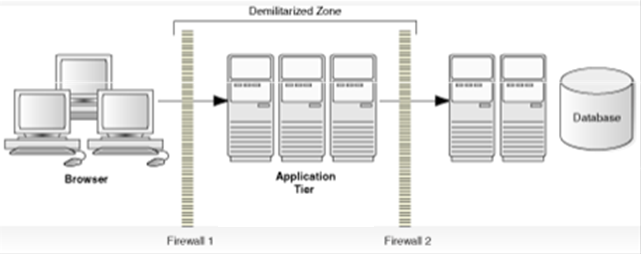
3.2.2 Deployment Using DMZ
Another deployment architecture that includes browser-based access is shown in the following graphic. In this scenario, users again access JD Edwards World via a browser using World Web Enablement, but the Web Enablement server resides on a server in the DMZ and communicates to the IBM i server residing behind a second firewall.
|
Note: The term demilitarized zone (DMZ) refers to a server that is isolated by firewalls from both the Internet and the intranet, thus forming a buffer between the two. |
Firewalls separating DMZ zones provide two essential functions:
-
Block any traffic types that are known to be illegal.
-
Provide intrusion containment should successful intrusions take over processes or processors.