9 Set Up Action Code, Fast Path, Generic Text, and Search Type Security
This chapter contains these topics:
9.1 Setting Up Action Code Security
From Master Directory (G), choose Hidden Selection 27
From Advanced & Technical Operations (G9), choose Security and System Admin
From Security Administration (G94), choose Security Officer
From Security Officer (G9401), choose Action Code
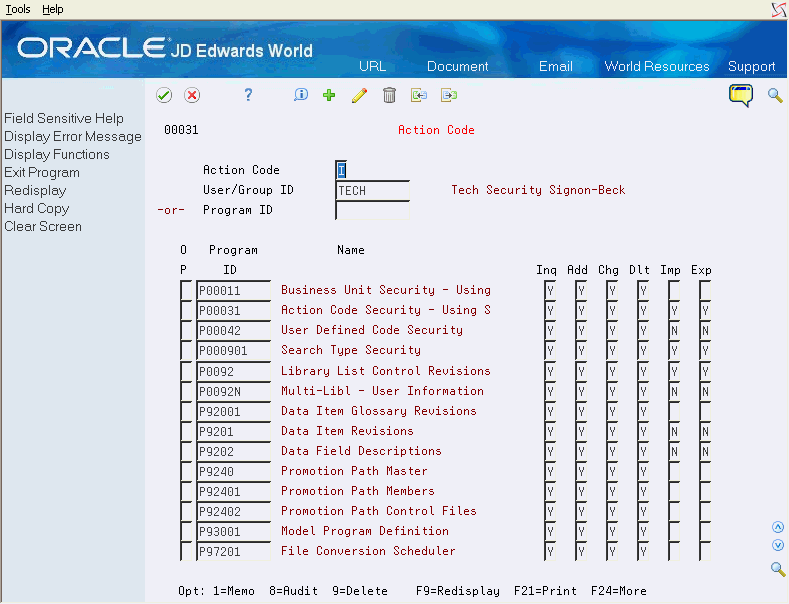
Action Code Security (P00031) allows you to secure any program ID or any JD Edwards User ID from performing certain actions on programs that have action codes. A user/group ID can be an individual user ID, a group profile ID, or *PUBLIC. The program ID may be an individual program ID or *ALL.
Interactive programs, whether they have an action code or not, may be secured using the Inquiry Action Code field. An 'N' in the Inquiry Action Code field will prevent a user from any access to an interactive program.
Action code security accommodates role-based security. In addition to user and group level security, Users may be assigned to a security role. When users sign on with a security role, all the groups tied to that security role will be considered when determining authorization to action codes.
|
Important: The Action Code Security program by default denies access if you have not set up records with the action code types (Inquire, Add, Change, Delete) with the value 'Y'. To allow access to action code security, you must set up records for individual users, groups, or *PUBLIC with the appropriate authorization. |
To set up action code security
-
Complete the ID field.
-
In the Action Codes fields, enter Y to allow access, or an N to restrict access.
In the top half of the screen, you may enter either user or group ID or program ID. When you press Enter, the subfile displays all programs associated with a particular user or group profile, or all profiles associated with a particular program.
The following fields are available on the screen:
-
Option 1 - Memo: Use this option to enter free-form text with any notes, comments or explanations about the security record. If a memo exists for a record, the selection option field will display in reverse image.
-
Option 8 - Audit Information Window: Use this option to retrieve audit information for a security record.
-
Option 9 - Delete Line: Use this option to delete a security record. Alternatively, a record can be deleted by blanking out all the fields on the subfile line.
Press F9 to display an inquiry again after an update.
After you set up a 'model' profile, you may use that model to add new profiles. Use the following steps to add profiles based on a model profile:
-
Inquire on the model
-
Roll to the end of the subfile to be sure all records are included.
-
Enter 'A' in the Action Code field, enter the new profile, and press Enter.
-
Inquire on the new profile that you just added to verify the additions.
Use the same approach for programs.
To add new lines to an existing profile or program, inquire first. You may then enter 'C' in the Action Code field and enter new information on either the first available blank space or over an existing profile. If you enter 'C' in the Action Code field and enter information in the first available blank space, the system adds the record. If there is a 'C' in the Action Code field and you type over an existing record, that record's information is changed, including the key.
Use the 'D' action code cautiously. If you enter 'D' in the Action Code field after you have inquired into a profile or program, the system deletes all records in the subfile. To delete just one record in the subfile, enter 'C' in the Action Code field, scroll down and clear the ID in the line that has to be deleted, and press Enter. You can also delete a record by entering 9 in the subfile selection field of the line that has to be deleted.
If you want to restrict a user profile from performing any specific action in all programs, you can use '*ALL' in the program ID for that profile. You cannot secure a CL program. You must use the RPG program, for example, P01051, P00201.
9.1.1 General Guidelines
If a user does not have a role or group, the Action Code Security program checks for security in the following sequence:
-
User Profile ID and Program ID
-
User Profile ID and Program ID = *ALL
-
*PUBLIC and Program ID
-
*PUBLIC and Program ID = *ALL
When the system locates an appropriate record, the application stops checking and uses the authority on the record it has found.
If you want to secure a profile from performing any specific action in all programs, use '*ALL' in the Program ID field for that profile. The system checks the *ALL record after checking for the specific program. This allows for an override to the general rule.
If a user logs on without selecting a role and belongs to a group (specified on the JD Edwards User Profile record in F0092), the system checks the security file in the following order:
-
User Profile ID and Program ID
-
User Profile ID and Program ID = *ALL
-
Group Profile ID (if any) and Program ID
-
Group Profile ID (if any) and Program ID = *ALL
-
*PUBLIC and Program ID
-
*PUBLIC and Program ID = *ALL
When the system locates an appropriate record, the application stops checking and uses the authority on the record it has found.
If you do not use role based security, the system uses the group profile, if any, from the JD Edwards User Profile.
If you use role- based security, a user signed on using a role has access to the authority for multiple groups. In this case, the checks for group profile check all active groups for the role, and if any group has authority, the role is granted authority. When a user is signed on using a role, the user profile's group, if any, is not checked.
Each action code has a Y/N flag which determines whether the user/group or *PUBLIC has authority to that particular action for a program or *ALL.
If you want to secure a profile from any access to an interactive program, enter 'N' in the Inquiry Action Code field. All other fields must be set to 'N'. This completely locks the profile from the program or *ALL.
To determine which programs action code security affects, you can use the Software Versions Repository program (P9801). To locate all programs, you must locate each of the following objects:
-
C0001
-
C0001A
-
C0001T (A91)
-
C0001L (ILE)
-
C0001TL (ILE)
For each object, use Where Used Cross Reference (F15) and enter / in the Type field and P in the To Display field to display the programs that use action codes.
9.2 Setting Up Fast Path Security
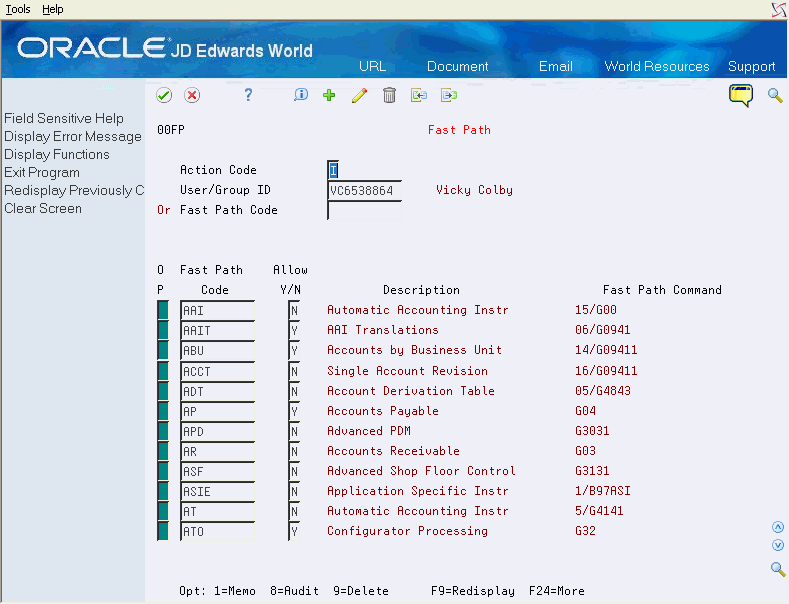
You use the Fast Path program to enter and maintain security records for use with fast path security. Fast path security allows security administrators to grant or deny access to *ALL or individual fast path commands by user, groups and *PUBLIC. Fast path security also accommodates role-based log-ins, giving users who log in using a role access to the fast path commands available for all groups currently attached to that role.
From Security Officer (G9401), choose Fast Path
Use fast path security to set up records for use with fast path authorization. You can set up fast path security at any time.
|
Note: During your A9.3 upgrade, you executed the Fast Path Conversion program in the Special Application Jobs section. This conversion program created records in the new Fast Path file (F00FP) for all your users, with *ALL fast paths, and either Y=Allow Fast Path or N=Do Not Allow Fast Path, as well as a record for *PUBLIC (if you selected the option to do so). You may add or change existing records using fast path securityThe Fast Path Allowed Flag is retained on the JD Edwards user profile record for compatibility with prior World releases. However, as of release A9.3, it is no longer in effect. |
The following options are available on the screen:
-
Option 1 - Exit to Generic Text: Use this option to enter free-form text with any notes, comments or explanations about the security record. If a memo exists for a record, the selection option field displays in reverse image.
-
Option 8 - Audit Information: Use this option to retrieve audit information for a security record.
-
Option 9 - Delete User/Fast Path Code: Use this option to delete a security record. Alternatively, a record can be deleted by blanking out both the Fast Path Code or User/Group ID and Allow Y/N fields.
If you specify a 'D' in the Action Code field to delete all records currently displayed in a subfile, the program displays the Delete Warning Window (V00DWW). When you press F6, the selected records are deleted.
It is recommended that you use the Database Audit Manager Tools to set up the Fast Path Security file, F00FP to track details on deleted records.
When the Action Code is 'C' and you type over the fast path code or user/group ID value in the subfile, the record that you typed over is deleted and the new data information will be added to the Fast Path Security file, F00FP.
When the Action Code is 'A' and you type over the fast path code or user/group ID value in the subfile, the new data information is added to file F00FP, but the record data that you typed over are retained. Press F9 to display an inquiry again after an update.
9.3 Setting Up Generic Text Security
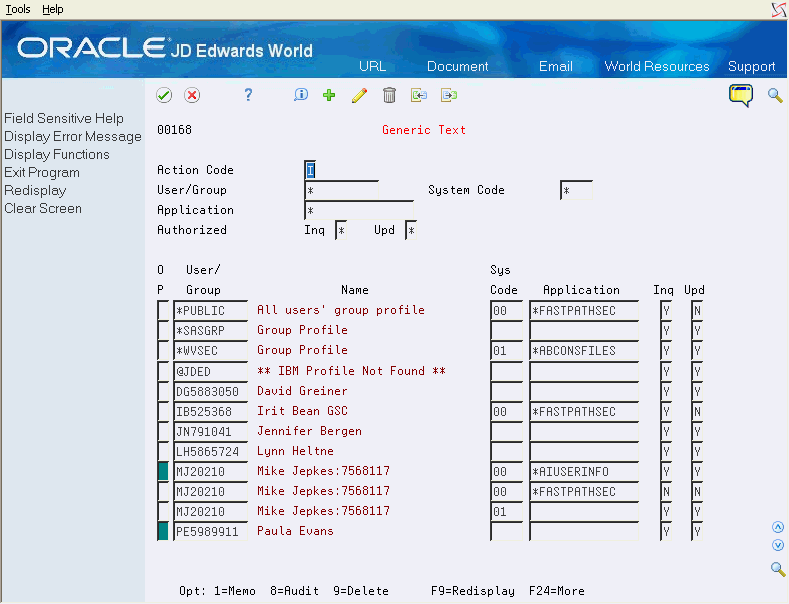
The Generic Text Security program allows entry and maintenance of security records for use with generic text security. Generic text security allows security administrators to grant or deny users, groups, and *PUBLIC the rights for inquiring on or updating specific generic text applications. Generic text security also accommodates role-based log-ins. When a user chooses a role upon log in, all the groups tied to the specific role will have access to the generic text applications.
When you use generic text security to grant users access to generic text applications, the system checks the Generic Text Security file for a record with access flags for Inquiry and Update. If a record is found and the requested access flag is set to 'Y', the user has access to the generic text application information.
|
Important!: The Generic Text security programs automatically lock out all users from accessing all Generic Text Applications. In order to allow access to inquire on and/or update Generic Text Applications, you need to set up records for *PUBLIC, groups, and/or individual users with the appropriate authorization. |
From Master Directory (G), choose Hidden Selection 27
From Advanced & Technical Operations (G9), choose Security and System Admin
From Security Administration (G94), choose Security Officer
From Security Officer (G9401), choose Generic Text
| Field | Explanation |
|---|---|
| User/Group | The User/Group field is used to enter generic text security records for a particular user, group, or *PUBLIC. This is the only mandatory field. |
| System Code | The System Code field is used to enter the generic text application system code the security record applies to. This field is optional.
You may enter a system code and leave the Application field blank. The security authorization will then apply to all generic text applications with that reporting system code. If you leave the System Code field blank and enter a generic text application, the program will automatically fill in the reporting system code defined in the Generic Text Window Definition File (F00161). |
| Application | The Application field is used to enter the generic text application this security record applies to. This field is optional.
NOTE: A security record entered without a system code or generic text application will apply to all generic text applications. The Inquiry Access Flag field is used to tell the system if the user, group, or *PUBLIC has authority to view messages on the specified generic text application. |
| Inquiry Access Flag | If you leave the Inquiry Access Flag field blank, the program will automatically fill in 'Y'. |
| Update Access Flag | The Update Access Flag field is used to tell the system if the user, group, or *PUBLIC has authority to update messages on the specified generic text application.
If you leave the Update Access Flag blank, the program will automatically fill in 'Y'. |
Use the fields in the header portion of the screen to search for existing records in the Generic Text Security file (F00168). Use the header fields to filter the subfile inquiry or position the subfile to a specific point. These fields are enabled for use with wildcard search characters. See Section 9.3.3, "Wildcard Search" for further instructions on how to use these fields to select records.
The following fields are available on the screen:
-
Option 1 - Memo: Use this option to enter free-form text with any notes, comments or explanations about the security record. If a memo exists for a record, the selection option field will display in reverse image.
-
Option 8 - Audit Information Window: Use this option to retrieve audit information for a security record.
-
Option 9 - Delete Line: Use this option to delete a security record. Alternatively, a record can be deleted by blanking out the User/Group, System Code, Application, Inquiry and Update fields.
If you specify a 'D' in the Action Code field to delete all records currently displayed in a subfile, the program displays the Delete Warning Window (V00DWW). When you press F6, the selected records are deleted.
It is recommended that you use the Database Audit Manager Tools to set up the Generic Text Security file, F00168, to track details on deleted records.
When the Action Code is 'C' and you type over the value in the User/Group field in the subfile, the typed-over record is deleted and the new data information is added to file F00168.
When the Action Code is 'A' and you type over the value in the User/Group field in the subfile, the new data information is added to file F00168, but the typed-over record data is retained. Press F9 to display an inquiry again after an update.
9.3.1 Setup Guidelines
The system checks security using a hierarchical approach, validating the most specific authorities first and moving to more general authorities. The validation stops once a record is found and grants access to the generic text application based on the Inquire and Update access flags.
9.3.1.1 No Role or Group Setup
If users do not have a role or individual group attached to their user ID, the system checks the Generic Text Security file in the following order:
-
Current User, Application System Code, Application
-
Current User, Application System Code
-
Current User
-
*PUBLIC, Application System Code, Application
-
*PUBLIC, Application System Code
-
*PUBLIC
9.3.1.2 No Role Setup, User Belongs to a Group
If users do not have a role attached, but have an individual group attached to their user ID, the system checks the Generic Text Security file in the following order:
-
Current User, Application System Code, Application
-
Current User, Application System Code
-
Current User
-
Group, Application System Code, Application
-
Group, Application System Code
-
Group
-
*PUBLIC, Application System Code, Application
-
*PUBLIC, Application System Code
-
*PUBLIC
In this scenario the group being validated is the group specified in the user's JD Edwards user profile (F0092).
9.3.1.3 User Signs on with a Security Role
If a user logs on selecting a role, the system checks the Generic Text Security file in the following order:
-
Current User, Application System Code, Application
-
Current User, Application System Code
-
Current User
-
Group(s), Application System Code, Application
-
Group(s), Application System Code
-
Group(s)
-
*PUBLIC, Application System Code, Application
-
*PUBLIC, Application System Code
-
*PUBLIC
In this scenario the validation is performed for the group or groups actively associated with the user's log-in role. The authority allowed to any one group is valid for the user's log-in role.
9.3.2 Security Setup Examples
The following examples illustrate security setup scenarios:
9.3.2.1 Example 1
This table illustrates generic text security setup.
| User/Group | System Code/Application | Inquiry | Update |
|---|---|---|---|
| ACN001122 | 00 | Y | Y |
| ACN001122 | 00 FASTPATHSEC | N | N |
| ACN001122 | 01 *ABCONS | Y | Y |
| ACN001122 | 01 *ADDNOTE | Y | Y |
| ACN001122 | 09 *P0901 | Y | N |
| *GROUP1 | 00 | Y | Y |
| *GROUP1 | 00 FASTPATHSEC | Y | Y |
| *GROUP1 | 43 | Y | Y |
| *PUBLIC | N | N |
In this example, user ACN001122 is in group *GROUP1. The system starts by looking for records at the user (ACN001122) level, group level, then *PUBLIC. Records at the user level supersede records at the group level. Records at the group level supersede records at the *PUBLIC level. User ACN001122 Generic Text Application access can be described as follows:
-
Access allowed to all Generic Text applications in system code 00 except for *FASTPATHSEC - Fast Path Security Maintenance
-
All access for *ADDNOTE - Additional Address Book Notes in system code 01
-
Access denied for all Generic Text applications in system code 01 except *ABCONS and *ADDNOTE
-
Access allowed for all Generic Text applications in system code 43.
-
Update access denied, but inquiry access is allowed for *P0901 - Accounts by Business Unit in system code 09
-
Access denied to the remaining Generic Text applications
9.3.2.2 Example 2
| User/Group | System Code/Application | Inquiry | Update |
|---|---|---|---|
| ACN001122 | 01 *EMAILURL | N | N |
| ACN001122 | 04 | Y | Y |
| *GROUP1 | 00 | Y | N |
| *GROUP1 | 00 *FASTPATHSEC | Y | Y |
| *GROUP1 | 43 | N | N |
| *GROUP2 | 00 *FASTPATHSEC | N | N |
| *GROUP2 | 01 | Y | Y |
| *GROUP2 | 42 | Y | Y |
| *GROUP3 | 00 *FASTPATHSEC | Y | Y |
| *GROUP3 | 01 | Y | N |
| *GROUP3 | 43 | Y | Y |
| *PUBLIC | N | N |
In this example, user ACN001122 logs on selecting a role containing groups *GROUP2 and *GROUP3. The system reads through all group records searching for a record allowing access to the generic text application. For example, *GROUP2 restricts access to the generic text application *FASTPATHSEC, but *GROUP3 allows full access. The record allowing access supersedes the access denied record, and thus ACN001122 is granted full access to *FASTPATHSEC. User ACN001122 Generic Text Application access can be described as follows:
-
Access allowed to all Generic Text applications in system code 04
-
All access allowed to all Generic Text applications in system code 01 except *EMAILURL Address - Email / URL
-
All access allowed for *FASTPATHSEC in system code 00
-
Access denied for all other Generic Text applications in system code 00
-
All access allowed for Generic Text applications in system codes 42 and 43
-
Access denied to remaining Generic Text applications
9.3.3 Wildcard Search
Wildcard search characters can substitute for one or more characters when searching for data in the subfield. Use Configuration Master Setup (P00CFG) on menu G944 option 19, to set up wildcard characters. For more information, see Chapter 18, "Work with Configuration Master Records" in this guide.
Using wildcards in a search tells the system to search for characters relative to their position in the field. Using wildcard characters will result in an exclusive search as opposed to a subfile reposition.
Wildcard search options include:
-
* = default wildcard search character for zero or many characters
-
_ = default wildcard search character for one and only one character
-
| = default escape wildcard search character. Use the escape wildcard search character to override the wildcard search character to the literal character value.
9.3.3.1 Wildcard Search Examples
These examples illustrates wildcard search options and the records they return:
-
User/Group = *A: This entry will return all users beginning with A.
-
Using 'AN' subfile in the User/Group field repositions the User/Group in alphabetical order starting with AN.
-
Using 'AN*' subfile in the User/Group field returns only the User/Group values with A in the first position, N in the second position, then any number of characters.
-
User/Group = *8: This entry will return all users ending with 8.
-
User/Group = *88: This entry will return all users ending with 88.
-
User/Group = *8*: This entry will return all user records containing an 8 anywhere in the user ID.
-
User/Group = T__1: This entry will return all users beginning with T, then any two characters, then 1.
-
User/Group = I__253*: This entry will return all users beginning with I, then any two characters, then 253, then any number of characters.
-
User/Group = _N*: This entry will return all users beginning with any single character, then N, then any number of characters.
-
User/Group = |*AN: This entry will reposition the subfile to all users greater than *AN.
-
User/Group = PO|_ENTRY: This entry will reposition the subfile to all users greater than PO_ENTRY.
9.4 Setting Up Search Type Security
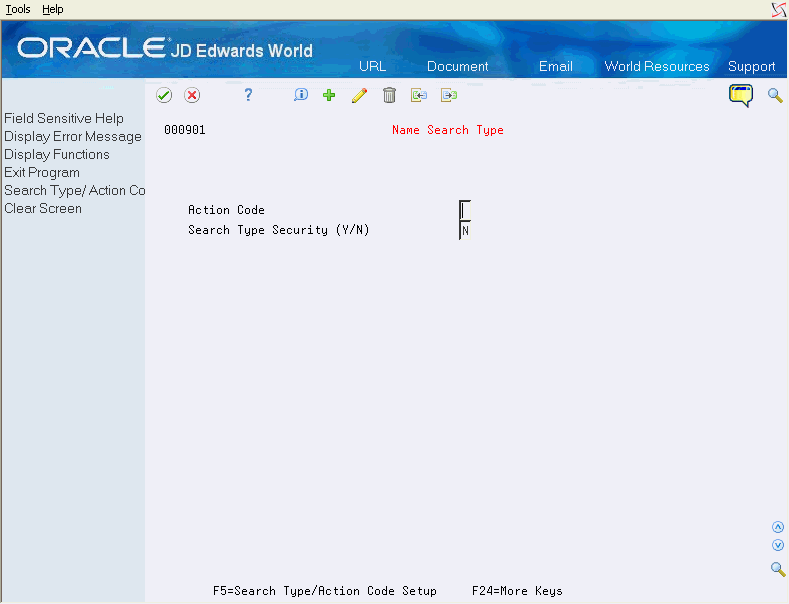
Use the Action Code/ Search Type Security program to enforce action code/search type security. If you activate security, then address book or related information associated with particular search types is restricted by search type and action code. You must set up users with appropriate authority to inquire on, add, change or delete records.
Action code/search type security accommodates role-based security. In addition to user and group-level security, you can assign users to a security role. When users sign on with a security role, all the groups tied to that security role are considered when determining authorization to search types.
|
Important!: If you activate search type security, the default setting for the Search Type Security program is No Access if you have not set up records with action code types (Inquire, Add, Change, Delete) of 'Y'. To allow access to search types, you must set up records for individual users, groups, or *PUBLIC with the appropriate authorization to allow update access. |
9.4.1 Activating Search Type Security
From Master Directory (G), choose Hidden Selection 27
From Advanced & Technical Operations (G9), choose Security & System Admin
From Security & System Administration (G94), choose Security Officer
From Security Officer (G9401), choose Name Search Type
Use the Name Search Type video (V000901)to activate or deactivate action code/search type security. Enter a 'Y' here to activate this security in programs that access address book records or information related to search types.
From this first screen, you can use function keys to the Action Code/Search Type Security video, where you authorize users or groups of users to specific actions on search types.
If you activate search type security, you must also set up authority to search types in the Action Code/Search Type Security file to grant access to address book records or other records with information associated with search types. Enter 'Y' in the Search Type Security field to activate search type security. Enter 'N' to deactivate search type security.
|
Note: Ensure you have set up appropriate authorizations for action code/search type security before activating this security. |
To set up action code/search type security
-
From the Name Search Type screen, select Search Type/Action Code Setup (F5).
-
On the Action Code/Search Type Security screen, complete one the following fields:
-
User/Group ID
-
Search Type
Figure 9-5 Action Code/Search Type Security screen
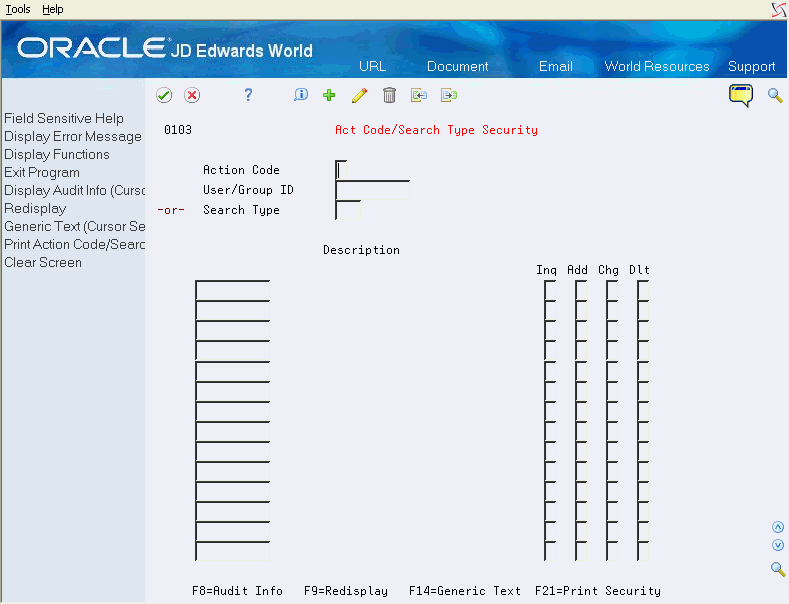
Description of ''Figure 9-5 Action Code/Search Type Security screen''
-
-
Complete the following fields and click Add.
-
User ID # or Search Type
-
Action Code
-
| Field | Explanation |
|---|---|
| User/Group ID # or Search Type | Enter the name of the user or search type to secure. If you entered a user or group in the top half of the screen, enter a search type to secure for that user. If you entered a search type in the top half of the screen, enter a user or group name to secure for that search type.
Note. The system does not display a column label until you inquire and press Enter. |
| Action Code | Enter 'Y' to allow access, or 'N' to restrict access. |
In the top half of the screen, you can enter either user or group ID or search type. When you press Enter, the subfile displays all search types associated with a particular user or group profile, or all profiles associated with a particular search type.
-
F14 - Generic Text: Use this option to enter free-form text with any notes, comments or explanations about the security record. If a memo exists for a record, the subfile values in the Search Type column will highlight and See Memo will display above the Search Type column. The cursor must be on a subfile record in order to use this option.
-
F8 - Display Audit Info: Use this option to retrieve audit information for a security record. The cursor must be on a subfile record in order to use this option.
-
F21 - Print Action Code/Search Type Security: Use this option to print the security records.
Press F9 to display an inquiry again after an update.
If you want to include all users with access to a particular search type, use *PUBLIC to indicate all users. You can also specify group access to search types by entering the group profile name in the User/Group ID field. To allow a user access to all search types, the special value 'Z9' may be used to indicate all search types.
9.4.2 General Guidelines
After you set up a profile, you can use the profile as model to add new profiles. Use the following steps to add profiles based on a model profile:
-
Inquire on the model profile and press Enter.
-
Roll to the end of the subfile to be sure all records are included.
-
Enter 'A' in the Action Code field, enter the new profile, and press Enter.
-
Inquire on the new profile that you just added to verify the additions.
To add new lines to an existing user profile or search type, inquire first. You can then enter 'C' in the Action Code field and enter new information on either the first available blank space or over an existing ID. If you enter 'C' in the Action Code field and enter information in the first available blank space, the system adds the record. Regardless whether you enter a 'C' or an 'A' in the Action Code field, the record is changed if you type over an existing record.
Use the 'D' action code cautiously. If you enter 'D' in the Action Code field after you have inquired into a search type, all security records for this profile or search type is deleted. To delete just one record in the subfile, enter 'C' in the Action Code field, scroll down and clear the search type or user/group ID in the line that has to be deleted, and press Enter.
9.4.3 Check Sequence for Action Type and Search Type Security
If the user logs on with no role and is not part of a group, when checking Action Code/Search Type Security, the application checks for security records in the following order:
-
User Profile ID and Search Type
-
User Profile ID and Search Type = Z9 (all Search Types)
-
*PUBLIC and Search Type
-
*PUBLIC and Search Type = Z9
If the user logs on without selecting a role and belongs to a group (specified on the JD Edwards User Profile record in the F0092 file), the system checks the security file in the following order:
-
User Profile ID and Search Type
-
User Profile ID and Search Type = Z9 (all search types)
-
Group Profile ID (if any) and Search Type
-
Group Profile ID (if any) and Search Type = Z9
-
*PUBLIC and Search Type
-
*PUBLIC and Search Type = Z9
In either scenario described, the application stops checking after encountering an appropriate record and uses the authority on the record it has found.
If you are not using role-based security, the system uses the group profile, if any, from the JD Edwards User Profile.
If you are using role-based security, users who sign on using a role may have access to the authority for multiple groups. In this case, the system checks all active groups for the role. If any group has authority, the role is granted authority. When a user signs on using a role, the system does not check the user profile's group, if any.
9.4.3.1 Examples
The following examples illustrate how the system checks security records.
In the first example, JANEDOE is restricted from other search types at the individual user level. Restrictions might also have been define at the group or *PUBLIC level.
| User ID | Search Type | Inquire | Add | Change | Delete |
|---|---|---|---|---|---|
| JANEDOE | C | Y | N | N | N |
| JANEDOE | Z9 | N | N | N | N |
In the second example, group '*ABENTRY' may add and update customer and supplier search types but may only delete suppliers. Users belonging to group *ABENTRY may inquire on all other search types. Users belonging to group *ABENTRY are allowed inquiry access to all search types. Users belonging to other groups or to no group do not have access to any search types.
| User ID | Search Type | Inquire | Add | Change | Delete |
|---|---|---|---|---|---|
| *ABENTRY | C | Y | Y | Y | N |
| *ABENTRY | S | Y | Y | Y | Y |
| *ABENTRY | Z9 | Y | N | N | N |
In the third example, user "BOBJONES" is associated with role ACCOUNTING. This role is associated with groups *AP, *AR and *GL. BOBJONES has authority to inquire, add, change and delete customer, supplier, facilities and jobs search types.
| User ID | Search Type | Inquire | Add | Change | Delete |
|---|---|---|---|---|---|
| *AP | S | Y | Y | Y | Y |
| *AR | C | Y | Y | Y | Y |
| *AR | Z9 | N | N | N | N |
| *GL | F | Y | Y | Y | Y |
| *GL | J | Y | Y | Y | Y |
| *PUBLIC | Z9 | Y | N | N | N |
Since BOBJONES belongs to role ACCOUNTING, he has access to the authority from any group associated with the role. Note that group *AR has access to the customer search type only, while others have access to inquiry on all search types based on the *PUBLIC entry.
It is important to exercise caution when setting up records using global authorities such as groups, *PUBLIC, and 'Z9', and to understand the search hierarchy. Otherwise, you may allow or deny access to users that you did not intend.