57 Work with SOX Reports
This chapter contains the topic:
57.1 Working with SOX Reports
You use three reports to review and manage the information in your system about SOX definitions and processes. Use the:
-
Process Definitions Report (R007114) to review all process definitions in the system.
-
Process Conflict Definitions Report (R007124) to review all process conflict definitions in the system.
-
Segregation/Duties Conflicts report (R00713) to review all process conflict violations in the system and during a SOX compliance audit.
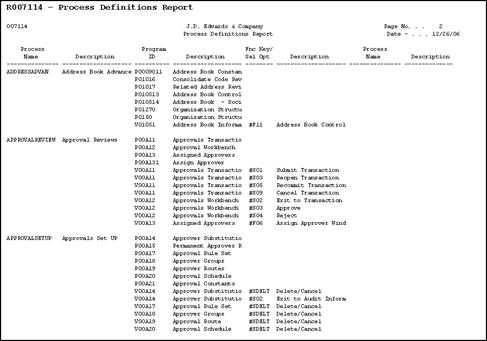
57.1.1 Running the Process Definitions Report
From Master Directory (G), choose Hidden Selection 27
From Advanced & Technical Operations (G9), choose Security & System Admin
From Security and System Administration (G94), choose Security Auditing and Reporting
From Security Auditing and Reporting (G947), choose Process Definitions
You use the Process Definitions report (R007114) to review all of your processes. The system retrieves all processes in the Process Definitions File (F00711).
57.1.2 Running the Process Conflict Definitions Report
From Security Auditing and Reporting (G947), choose Process Conflict Definitions
You use the Process Conflict Definitions report (R007124) to review all possible process conflicts. The system retrieves all process conflicts in the Process Conflict Definitions File (F007121).
Figure 57-2 Process Conflict Definitions Report
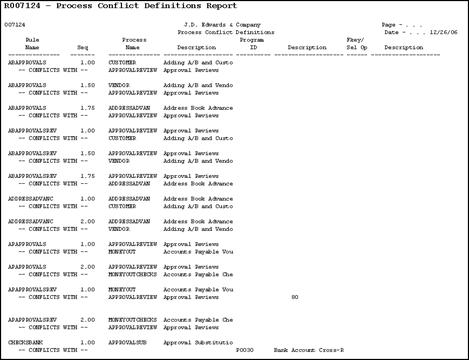
Description of "Figure 57-2 Process Conflict Definitions Report"
57.1.3 Running the Segregation/Duties Conflicts Report
From Security Auditing and Reporting (G947), choose Segregation/ Duties Conflicts
Use the Segregation/Duties Conflict Report (R00713) to review all possible conflict violations. Each time the system locates a conflict violation it enters it on the report and the reason why it is a violation. You can then use the information to adjust your security (action code and function key). Continue to run this report until there are no conflict violations or you are satisfied with the results of the report. You can use this report during a SOX compliance audit.
The system retrieves all of the security information for the processes, programs, and function key/selection options in the Conflicts Definition file (F00712), builds a workfile of all the information, and then uses the information to build the Process Conflict Violations report. The system uses the following information in the following files to build the workfile:
-
Group name for individual User ID from the Library Lists - User file (F0092)
-
User/Group and action code security for every program within a process in the conflicts file from the Action Code Security file (F0003)
-
User/Group and allow usage (Y/N) for every video/function key/selection opt within a process in the conflicts file from the Function Key security file (F9612)
The system also determines if the *PUBLIC record is not set up for a program or function key/selection option. It creates a workfile record with *PUBLIC = Y because without a *PUBLIC record, it assumes that the users have full access. The system also creates all records in the workfile for every process/program/video even if the access is set to N because that can override the *PUBLIC record, if it is set to Y.
57.1.3.2 Data Sequence
Ensure that the Rule Name is set to Seq 001 and the Sequence Number is set to Seq 002. The Option field, in the fold, must be set to N.
Figure 57-3 Process Conflict Violations Report
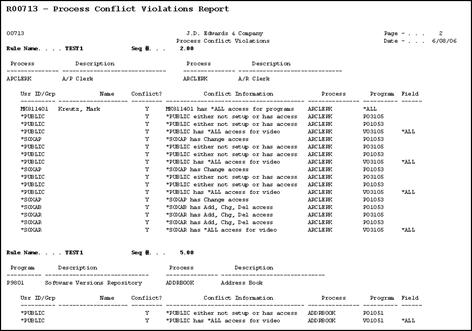
Description of "Figure 57-3 Process Conflict Violations Report"
Figure 57-4 Segregation/Duties Conflict Report
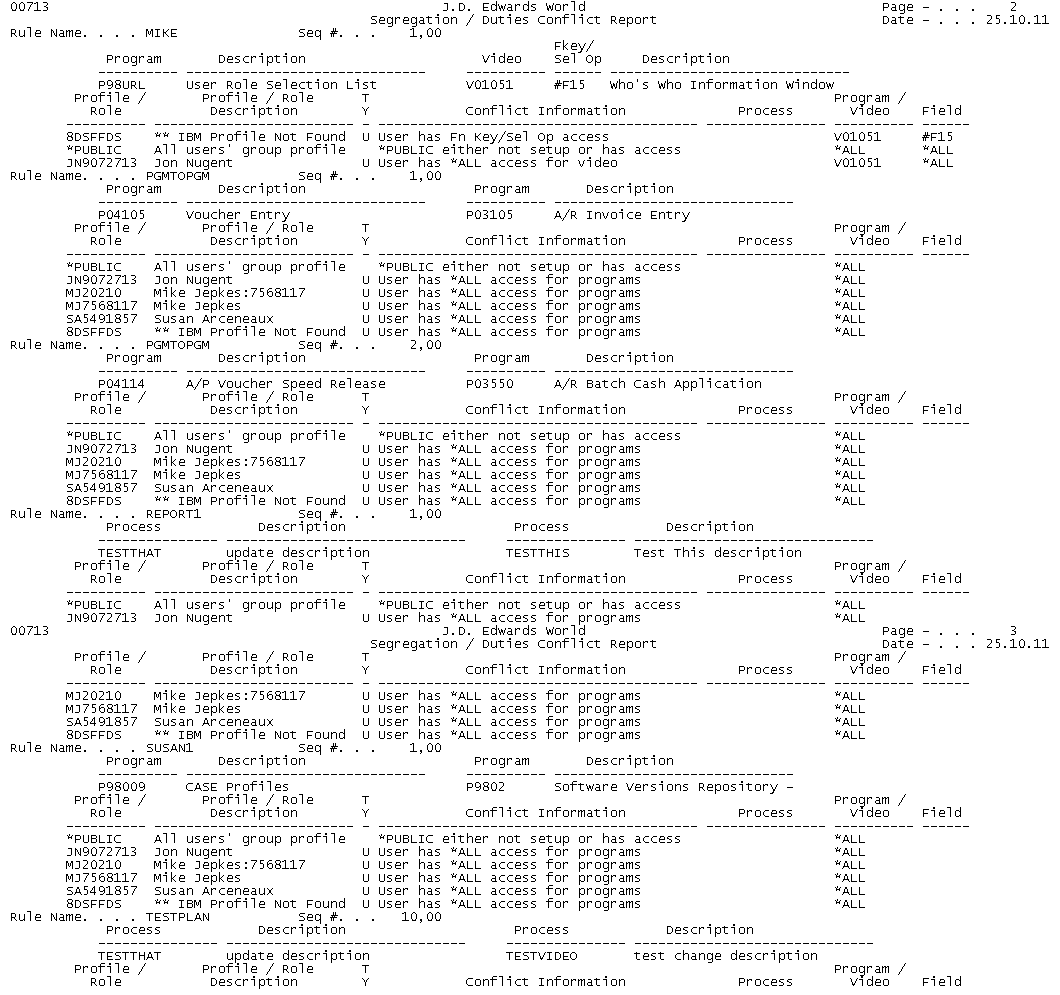
Description of "Figure 57-4 Segregation/Duties Conflict Report"