1 Overview
This section gives an overview of VLE and explains the general principles of application security.
Note:
This Guide applies to all versions of VLE.Product Overview
Oracle's Virtual Library Extension (VLE) is packaged as an engineered system built on existing Oracle server and storage platforms. The servers, disk storage and standard rack mount enclosure are delivered as a packaged system.The VLE includes pre-installed pre-configured software for VLE functionality so that limited site-level configuration is required to integrate the product into the customer's managed tape environment. The VLE is designed to preclude the need for customer administration of the system.
Note:
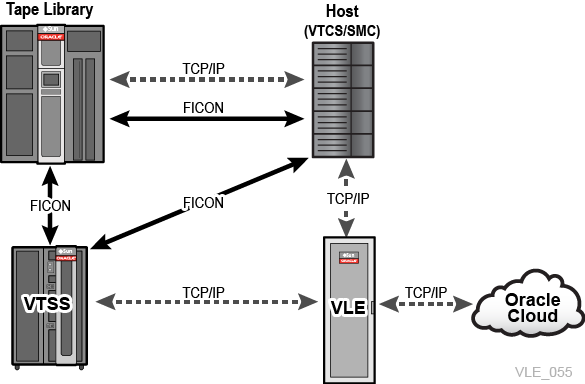
Only qualified Oracle personnel are permitted to maintain the system and administer any configuration changes.As shown in Figure 1-1, VLE is just one component of Oracle's StorageTek Virtual Storage Manager (VSM) system.
Major subsystems include:
- VTSS hardware and software
-
The Oracle VTSS supports emulated tape connectivity over FICON interfaces to IBM MVS, VM and zLinux hosts and also FICON attachment to Real Tape Drives (RTDs) and TCP/IP attachment to other VTSSs and VLEs. FICON is an IBM-driven standard for channel protocol between CPU (zOS) and devices.
- Enterprise Library Software (ELS), which includes Virtual Tape Control Software (VTCS)
-
ELS is the consolidated suite of StorageTek mainframe software that enables and manages the VTSS. The ELS base software consists of Host Software Component (HSC), Storage Management Component (SMC), HTTP Server and Virtual Tape Control Software (VTCS).
VTCS is the ELS component that controls virtual tape creation, deletion, replication, migration and recall of virtual tape images on the VTSS subsystem, and also captures reporting information from the VTSS subsystem.
- Virtual Library Extension (VLE) hardware and software
-
The VLE subsystem functions as a migrate and recall target for VTSS Virtual Tape Volumes (VTVs). The VLE is IP-attached to the VTSS. VLE is optionally attached to Oracle Cloud through TCP/IP for storing customer VTV data in the cloud.
Critical Security Principles
The following principles are fundamental to maintaining system security.
Keep Software Up To Date
Patches and system updates will be installed by qualified Oracle personnel.
Restrict Network Access to Critical Services
VLE should be installed in secure physical locations with access limited to authorized customer employees/agents and Oracle service personnel. The system should be networked behind a firewall. Only Oracle service personnel are permitted to administer the system.
Authentication
Ensure that only authorized personnel can access system. Passwords should be changed when deployed at the customer site.
Follow the Principle of Least Privilege
No additional user accounts are permitted. Only pre-existing accounts are used for system maintenance and administration.