Depending on your configured web application server, see the following sections. Alternatively, you can see your web application server-specific administration guide for additional details.
Topics:
· Enable HTTPS Configuration for OFSAA
· Configure Security for Tomcat
· Configure Security for WebSphere
· Configure Security for WebLogic
HTTPS is recommended during OFSAA installation, by default. This configuration creates an encrypted environment and functions as a secure environment for client-server communication.
TIP:
See the HTTPS Protocol section in the relevant version of the OFS Analytical Applications Infrastructure Administration Guides on the OHC.
- To enable HTTPS post-installation.
- To view configurations related to SSLv3 and TLS1.2.
To set Security Configurations for Tomcat, follow these steps:
1. Add the preferred cipher list to Tomcat and update the value of sslProtocol to TLS 1.2 in the SSL Connector tag of the $CATALINA_HOME/conf/server.xml file.
2. Add Ciphers attribute to the Connector tag in the server.xml file as shown in the following example.
TIP:
Multiple Cipher Suites must be comma-separated.
For example,
ciphers="TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384”
For more details on TLS1.2 supported Ciphers and Recommendations, see the following links:
§ https://www.owasp.org/index.php/Securing_tomcat
3. Add the following session attributes under the ‘Context’ tag of the $CATALINA_HOME/conf/server.xml file.
sessionCookiePath= “<context>”
sessionCookieDomain= “<domain>”
NOTE:
<context> is OFS AAI context and <domain> is the domain name of the server that must receive the cookie. For example, if you access the application through the URL app.mysite.com, then it should be set to app.mysite.com and not mysite.com.
4. Configure for secure and HttpOnly using the following procedure:
a. In the $CATALINA_HOME/conf/context.xml file, add the ‘useHttpOnly=true’ attribute to ‘Context’ tag.
b. Add the secure="true" attribute to the ‘Connector’ tag section of the $CATALINA_HOME/conf/server.xml file.
c. Add the following tags to the Session-Config Section of the $CATALINA_HOME/conf/web.xml file.
<cookie-config>
<http-only>true</http-only>
<secure>true</secure>
</cookie-config>
5. Open the $CATALINA_HOME/conf/server.xml file and add a tag as shown in the following:
a. Search for the ”<Host name=” parameter in the file.
b. Add the following tag:
<Valve className="org.apache.catalina.valves.ErrorReportValve" showReport="false" showServerInfo="false" />
6. Disable the directory listing in the $CATALINA_HOME/conf/web.xml file.
Add the following lines to the Servlet Section:
<init-param>
<param-name>listings</param-name>
<param-value>false</param-value>
</init-param>
7. Restart the Tomcat Service.
In the WebSphere Admin console, restrict cookies to HTTPS sessions in Sessions Management Configuration, specify the JSESSIONID variable in the Web Container Settings, set TLS configuration, and configure the application security. The subsections describe the procedures in detail.
In Session Management Configuration, restrict cookies to HTTPS Sessions.
To set the session management configuration, follow these steps:
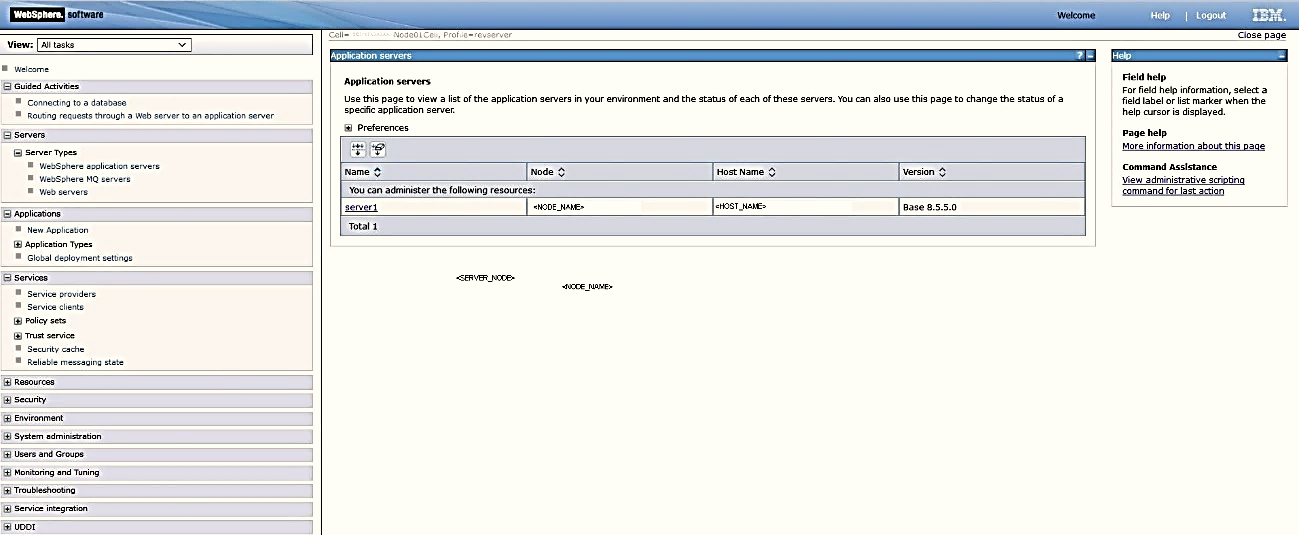
1. Navigate to the WebSphere Admin console and in the Navigation Tree, select Server, select Server Types and then select WebSphere application servers.
2. Select the configured Application Server from the list by clicking on the Server Name.
Figure 1: WebSphere Application Window

3. Select Configuration and then select Session Management from Container Settings.
Figure 2: Configuration tab

4. In General Properties, select Enable Cookies.
Figure 3: Session Management Configuration

5. Enter the following details:
Cookie Name - JSESSIONID
Cookie domain - <domain>
Cookie Path - /<context>/
NOTE:
<context> is OFS AAI context and <domain> is the domain name of the server that receives the cookie. For example, if you access the application through the URL app.mysite.com, then set it to app.mysite.com and not mysite.com.
Figure 4: Session Management Configuration

6. Ensure the following checkboxes are selected:
§ Restrict Cookies to HTTPS Sessions
§ Set session cookies to HTTPOnly to prevent cross-site scripting attacks
7. Click Apply and save changes.
8. Restart the Application Server through the console.
To configure the TLS protocol in WebSphere, follow these steps:
1. Log in to the console (http://host:adminport/ibm/console).
2. In the Security menu, select SSL certificate and key management, select SSL configurations, select NodeDefaultSSLSettings, and then select Quality of protection (QoP) settings.
3. Change the Protocol value to TLSv1.2.
The preceding configuration ensures that the WebSphere server accepts only TLSv1.2 connections. That is, when the web server acts as a server (inbound) or as a client (outbound), the SSL connections are established through the TLSv1.2 protocol. When testing from a browser, ensure to check that the browser settings are set to initiate only TLS handshakes.
For more information, see Configuring WebSphere Application Server to support TLS 1.2.
For cipher suite configuration, see https://www.ibm.com/support/knowledgecenter/en/linuxonibm/liaag/wascrypt/l0wscry00_wasciphersuite.htm
For more details about strong cipher configuration, see https://www.owasp.org/index.php/Transport_Layer_Protection_Cheat_Sheet#Rule_-_Only_Support_Strong_Cryptographic_Ciphers.
Enable Application security to secure your server from unauthorized users and allow access only to authenticated users. This prevents unauthorized access to configuration files in directories.
To enable Application security, follow these steps:
1. Log in to WebSphere with administrator credentials.
2. Select Security from the tree and then select Global security to display the Global security window.
3. Select Enable administrative security and Enable application security.
Figure 5: Global Security window

4. Click Apply and save the configuration.
The Directory Listing is disabled by default. In other words, directoryBrowsingEnabled is set to false.
For detailed information, see the IBM WebSphere User Documentation.
In the WebLogic Server, though the Auth Cookie Enabled option is selected by default, the cookies are not secure. To ensure this, you must toggle the “Auth Cookie Enabled” option in the WebLogic console by disabling it first and then re-enabling it for secure cookies. After that, create a weblogic.xml file in the $FIC_HOME/ficweb directory and the deploy .ear file in your WebLogic server.
To configure security for WebLogic, follow these steps:
1. Log in to WebLogic Server Administrative Console.
2. Select Domain Structure and then select Domain from the tree.
3. Select Configurations (selected by default), and then select the Web Application.
Figure 6: Oracle WebLogic Server Administration Console

4. Scroll through the configurations options within the page and locate the Auth Cookie Enabled option. By default, the checkbox is selected.
5. Unselect the Auth Cookie Enabled checkbox and click Save.
6. Select the Auth Cookie Enabled checkbox and click Save.
7. Configure session Secure and HttpOnly.
For OFS AAI versions 8.1.0.0.0 and higher, modify the weblogic.xml file in the $FIC_HOME/ficweb directory and add the following tag under the root element:
<session-descriptor>
<cookie-name>JSESSIONID</cookie-name>
<cookie-domain><domain></cookie-domain>
<cookie-path>/<context></cookie-path>
<cookie-http-only>true</cookie-http-only>
<cookie-secure>true</cookie-secure>
</session-descriptor>
NOTE:
<context> is OFS AAI context and <domain> is the domain name of the server that must receive the cookie. For example, if the application is accessed through the URL app.mysite.com, then it should be set to app.mysite.com and not mysite.com.
8. Configure TLS protocol for WebLogic using the following steps:
a. Add the following parameters in setDomainEnv.sh present under /domains/<DomainName>/bin as arguments for JAVA_OPTIONS: -Dweblogic.security.disableNullCipher=true -Dweblogic.security.SSL.protocolVersion=TLS1.2
b. Add the preferred cipher suite to the config.xml file as shown in the following example. Use only strong cryptographic ciphers recommended for TLS 1.2.
Example:
<ssl>
<name><servername></name>
<enabled>true</enabled>
<ciphersuite> TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384</ciphersuite>
...
</ssl>
For more information, see https://docs.oracle.com/middleware/1213/wls/SECMG/standards.htm#SECMG743
For more details about strong cipher configuration, see https://www.owasp.org/index.php/Transport_Layer_Protection_Cheat_Sheet#Rule_-_Only_Support_Strong_Cryptographic_Ciphers.
9. Disable directory listing. Add the following tag under <container-descriptor> in $FIC_HOME/ficweb/weblogic.xml:
<index-directory-enabled>false</index-directory-enabled>
10. Enable REST API authorization by OFSAA. Follow these steps:
a. Open the config.xml file located in the domain where OFSAA is deployed, that is, <domain_home>/config/config.xml.
b. Add the following in the security-configuration tag:
<enforce-valid-basic-auth-credentials>false</enforce-valid-basic-auth-credentials>
11. Build the .ear file and deploy it onto the WebLogic server.
12. Restart the services.