A Roles
This appendix lists out-of-box roles and user access to database targets without SYSDBA privileges.
A.1 Out-of-Box Roles
The following table lists predefined roles that are available out-of-box with Enterprise Manager.
| Roles | Description |
|---|---|
|
EM_ALL_ADMINISTRATOR |
Role has privileges to perform Enterprise Manager administrative operations. It provides Full privileges on all secure resources (including targets) |
|
EM_ALL_DESIGNER |
Role has privileges to design Enterprise Manager operational entities such as Monitoring Templates. |
|
EM_ALL_OPERATOR |
Role has privileges to manage Enterprise Manager operations. |
|
EM_ALL_VIEWER |
Role has privileges to view Enterprise Manager operations. |
|
EM_CBA_ADMIN |
Role has privileges to manage Chargeback Objects. It provides the ability to create and view chargeback plans, chargeback consumers, assign chargeback usage, and view any CaT targets. |
|
EM_CLOUD_ADMINISTRATOR |
Enterprise Manager user for setting up and managing the infrastructure cloud. This role could be responsible for deploying the cloud infrastructure (servers, pools, zones) and infrastructure cloud operations for performance and configuration management. |
|
EM_COMPLIANCE_DESIGNER |
Role has privileges for create, modify and delete compliance entities. |
|
EM_COMPLIANCE_OFFICER |
Role has privileges to view compliance framework definition and results. |
|
EM_CPA_ADMIN |
Role to manage Consolidation Objects. It gives the capability to create and view consolidation plans, consolidation projects and view any CaT targets. |
|
EM_HOST_DISCOVERY_OPERATOR |
Role has privileges to execute host discovery |
|
EM_INFRASTRUCTURE_ADMIN |
Role has privileges to manage the Enterprise Manager infrastructure such as managing plug-in lifecycle or managing self update. |
|
EM_PATCH_ADMINISTRATOR |
Role for creating, editing, deploying, deleting and granting privileges for any patch plan. |
|
EM_PATCH_DESIGNER |
Role for creating and viewing for any patch plan |
|
EM_PATCH_OPERATOR |
Role for deploying patch plans |
|
EM_PLUGIN_AGENT_ADMIN |
Role to support plug-in lifecycle on Management Agent |
|
EM_PLUGIN_OMS_ADMIN |
Role to support plug-in lifecycle on Management Server |
|
EM_PLUGIN_USER |
Role to support view plug-in console |
|
EM_PROVISIONING_DESIGNER |
Role has privileges for provisioning designer |
|
EM_PROVISIONING_OPERATOR |
Role has privileges for provisioning operator |
|
EM_SSA_ADMINISTRATOR |
Enterprise Manager user with privilege to set up the Self Service Portal. This role can define quotas and constraints for self service users and grant them access privileges. |
|
EM_SSA_USER |
This role grants Enterprise Manager user the privilege to access the Self Service Portal. |
|
EM_TARGET_DISCOVERY_OPERATOR |
Role has privileges to execute target discovery. |
|
EM_TC_DESIGNER |
Role has privileges for creating Template Collections |
|
EM_USER |
Role has privilege to access Enterprise Manager Application. |
|
PUBLIC |
PUBLIC role is granted to all administrators. This role can be customized at site level to group privileges that need to be granted to all administrators. |
A.2 User Access to Database Targets without SYSDBA Privileges
A user may need to perform operation on a database target such as:
-
Monitor Performance Page
-
Review and administer AWR
-
Use SQL Access Advisor
-
Use SQL Tuning
In circumstances where a user is required to access database monitoring/management functions in Enterprise Manager but has not been given full SYSDBA access to database targets, you can create an Enterprise Manager administrator and give him the EM_USER and PUBLIC roles as well as, "Connect to any viewable target" privileges to the database targets that you want the administrator to access.
In the following steps we will grant "Connect to any viewable target" to all targets (instead of listing specific target instances). Depending on the type of authentication model being used, the administrator details will be stored in either the Cloud Control Repository or an external store, such as LDAP.
A.2.1 Creating an Administrator
-
From the Setup menu, select Security and then Administrators.
-
Click Create.
-
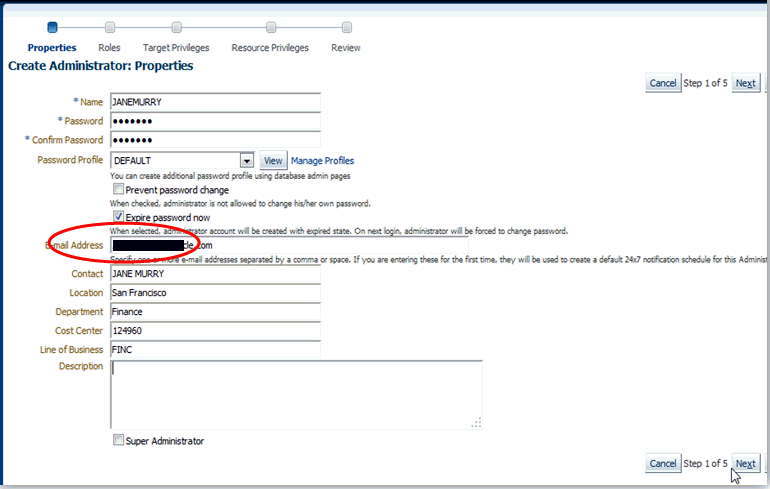
From the Create Administrator: Properties page, enter all necessary information, including the password profile as enforced by your security team. In the graphic shown below,"Expire password now", has been selected so that when this user logs in with the temporary password, they will be forced to reset their password.
Once you have entered the requisite information, click Next.
-
From the Create Administrator: Roles Page, choose the default roles and click Next.
-
From the Create Administrator: Target Privilege page, Select the Connect to any viewable target privilege. This enables the administrator to connect to all targets viewable in his console.
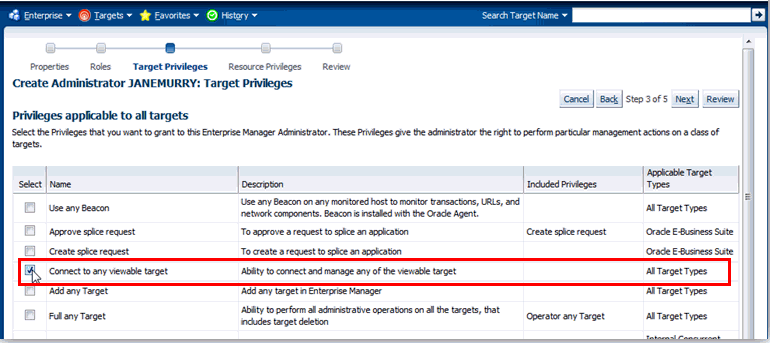
Click Next.
-
From the Resource page, click Next. This accepts the default settings.
-
Review your settings on the Review page. Click Finish.
Valid users must reside on the target instances.
A.2.2 Users Requiring Access to the Database Performance Page
-
On the DB Target host, log in as sysdba and create a <dbmonitor_admin> user and grant appropriate privileges:
SQL> create user <dbmonitor_admin> identified by <password>; SQL> grant select any dictionary to <dbmonitor_admin>; SQL> grant create session to <dbmonitor_admin>;
-
Log in to the Cloud Control console as <gc_user> user, which is JANEMURRY in the example:
TARGETS > DATABASE > ORADB > PERFORMANCE
Enter login and password for <dbmonitor_admin> user.
The Performance page should now appear. The following user will now be able to access all pages under the section of Additional Monitoring Links.
A.2.3 User Requiring Accessing AWR/ADDM
-
On a DB Target host log in as sysdba and create an <awr_admin> user and grant appropriate privileges:
SQL> create user <awr_admin> identified by <password>; SQL> grant select any dictionary to <awr_admin>; SQL> grant create session to <awr_admin>; SQL> grant execute on dbms_workload_repository to <awr_admin>;
-
Log in to the Cloud Control console as <gc_user> user, which is JANEMURRY in our example:
TARGETS > DATABASE > ORADB > Related Links: Advisor Central
Enter login and password for the <awr_admin> user.
-
Then to generate the AWR/ADDM report:
ADDM > OK
A.2.4 User Requiring Access to SQL Access Advisor
-
On the DB Target host log in as sysdba and create a <sqlaccess_admin> user and grant the appropriate privileges:
SQL> create user <sqlaccess_admin> identified by <password>; SQL> grant select any dictionary to <sqlaccess_admin>; SQL> grant create session to <sqlaccess_admin>; SQL> grant oem_advisor to <sqlaccess_admin>;
-
Log in to the Cloud Control console as <gc_user> user, which is JANEMURRY in our example:
TARGETS > DATABASE > ORADB > Related Links: Advisor Central >SQL Access Advisor Enter login and password for <sqlaccess_admin> user.
-
To perform SQL Access tasks, complete steps in the wizard
A.2.5 User Requiring Access to SQL Tuning Advisor
-
On the DB Target host, log in as sysdba and create a <sqltune_admin> user and grant appropriate privileges:
SQL> create user <sqltune_admin> identified by <password>; SQL> grant select any dictionary to <sqltune_admin>; SQL> grant create session to <sqltune_admin>; SQL> grant oem_advisor to <sqltune_admin>;
-
Log in to the Cloud Control console as <gc_user> user, which is JANEMURRY in our example:
TARGETS > DATABASE > ORADB > Related Links: Advisor Central > SQL Tuning AdvisorEnter login and password for <sqltune_admin> user.
-
You may now perform SQL Tuning tasks. For example, click on TOP ACTIVITY > Run ASH reports.