D Configuring Security Certificates
Oracle supplies self-generated security certificates to be used with HTTPS/SSL ports. During installation, STA uses the Java keytool to generate a certificate on the STA server, using the server hostname. You can optionally replace the Oracle certificate with your own approved certificate from a selected certificate authority (for example, VeriSign).
This chapter includes the following section:
Security Certificate Configuration Tasks
If you want to use a different security certificate than the default, perform these procedures in the order listed.
Note:
These procedures use Mozilla Firefox running on a Windows platform.Establish the Initial HTTPS/SSL Connection
-
Start a supported Web browser on your computer and enter the HTTPS/SSL version of the URL for the STA application.
https://STA_host_name:port_number/STA/
Where:
-
host_name is the hostname of the STA server.
-
port_number is the STA port number you specified during installation. The default HTTP port is 7021; the default HTTPS port is 7022.
-
STA must be uppercase.
For example:
https://staserver.example.com:7022/STA/
The Connection is Untrusted screen appears.
-
-
Select I Understand the Risks, and then click Add Exception.
The Add Security Exception screen appears.
-
Click View.
The Certificate Viewer screen appears. The certificate is not shown as verified because it is not from a certificate authority.
-
To examine the certificate, click the Details tab.
-
In the Certificate Fields panel, select issuer. Following is a sample display. CN indicates the server name on which the certificate was generated.
CN = staserver.example.com OU = Tape Systems O = Oracle America Inc L = Redwood City ST = California C = USA
-
Click Close to return to the Add Security Certificate screen.
-
Select Confirm Security Exception.
The certificate is added to the STA server, and you can now use HTTPS with the certificate.
Reconfigure WebLogic to use a Different Security Certificate
-
Start a supported Web browser on your computer.
-
In the Location Bar or Address field, enter the URL of the WebLogic Administrator console. The URL uses one of the following formats:
http://local_host_name:port_number/console
https://local_host_name:port_number/console
where local_host_name and port_number are the name and port number of the WebLogic Administrator console defined during STA installation. The default HTTP port number is 7019, and the default HTTPS port number is 7020. For example:
https://sta_server:7020/console -
On the Welcome screen, enter the WebLogic Administration console username and password defined during STA installation, and then click Login.

Description of the illustration ''wl_login.png''
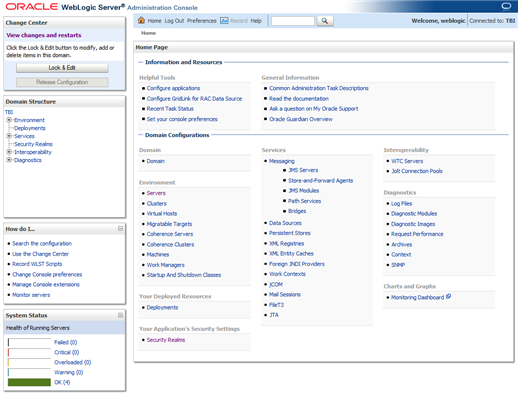
The WebLogic Server Administration Console Home page appears.
Description of the illustration ''wl_home.png''
-
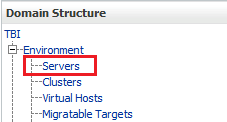
In the Domain Structure section, select Environment, and then select Servers.
Description of the illustration ''cert_servers.png''
-
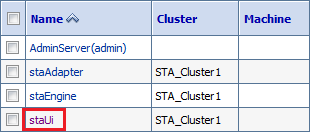
In the Servers table, select the staUi active link (select the name itself, not the check box).
Description of the illustration ''cert_staui.png''
-
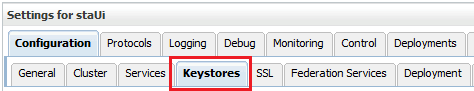
Select the Keystores tab.
Description of the illustration ''cert_keystores.png''
-
In the Change Center section, click Lock & Edit.
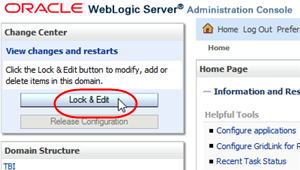
Description of the illustration ''wl_lockedit.png''
-
In the Keystores section, click Change.
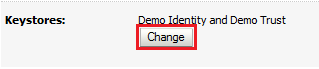
Description of the illustration ''cert_change.png''
-
In the Keystores menu, select Custom Identity and Java Standard Trust.
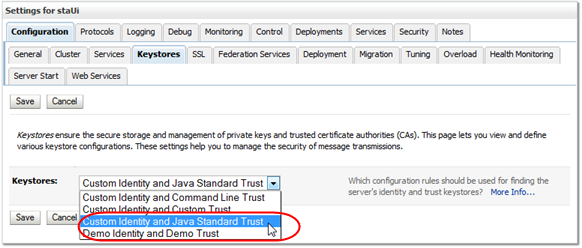
Description of the illustration ''cert_keystoresmenu.png''
-
Click Save.
-
Complete the Keystores screen as follows:
-
Custom Identity Keystore—Path and file of the private key file.
-
Custom Identity Keystore Type—Keystore type. If configuring for RACF authentication, enter PKCS12.
-
Custom Identity Keystore Passphrase—Password supplied by the MVS system administrator.
-
Java Standard Trust Keystore Passphrase—New password for the Java Standard Trust Keystore file.
Caution:
If you forget these passwords, you must re-install STA.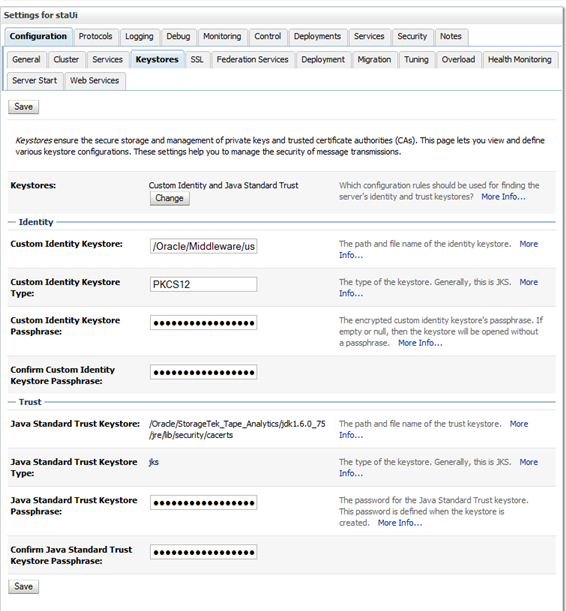
Description of the illustration ''cert_keystoresentries.png''
-
-
Click Save.
-
Select the SSL tab.
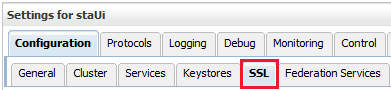
Description of the illustration ''cert_ssl.png''
-
Enter the Private Key Alias and Private Key Passphrase supplied by the MVS system programmer.
Note:
To determine the Private Key Alias, use the keytool command at the system command line. For example:# keytool -list -keystore CLTBI.PKCS12DR.D080411 -storetype PKCS12 Enter keystore password: (password from the MVS sysadmin) Keystore type: PKCS12 Keystore provider: SunJSSE Your keystore contains 1 entry tbiclient, Aug 17, 2011, PrivateKeyEntry, Certificate fingerprint (MD5): 9A:F7:D1:13:AE:9E:9C:47:55:83:75:3F:11:0C:BB:46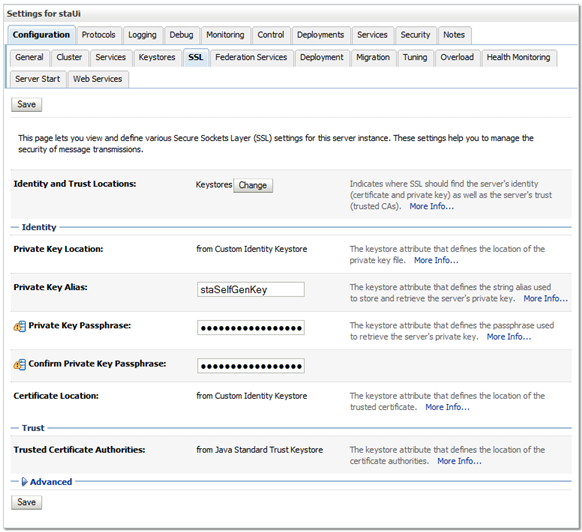
Description of the illustration ''cert_sslentries.png''
-
Click Save.
-
In the Trusted Certificate Authorities section, click Advanced.
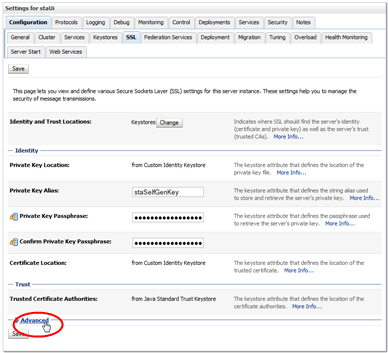
Description of the illustration ''cert_advanced.png''
-
Complete the Advanced section of the SSL screen as follows:
-
Use Server Certs—Select the check box.
-
Two Way Client Cert Behavior—Select Client Certs Requested But Not Enforced.
-
Inbound Certification Validation—Select Builtin SSL Validation Only.
-
Outbound Certificate Validation—Select Builtin SSL Validation Only.
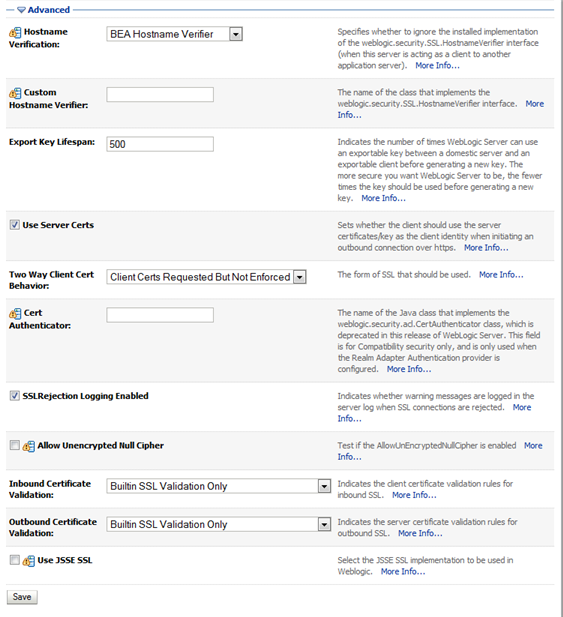
Description of the illustration ''cert_advancedentries.png''
-
-
Click Save.
-
In the Change Center section, click Activate Changes.
Description of the illustration ''wl_activate.png''
-
Log out of WebLogic.
-
Stop all STA services. See the STA Administration Guide for command usage details.
# STA stop all Stopping the staui service...... Successfully stopped the staui service Stopping the staadapter service...... Successfully stopped the staadapter service Stopping the staengine service...... Successfully stopped the staengine service Stopping the staweblogic service...... Successfully stopped the staweblogic service Stopping the staservd Service... Successfully stopped staservd service Stopping the mysql service..... Successfully stopped mysql service # -
Start all STA services.
# STA start all Starting mysql Service.. mysql service was successfully started Starting staservd Service. staservd service was successfully started Starting staweblogic service...... staweblogic service was successfully started Starting staengine Service......... staengine service was successfully started Starting staadapter Service.......... staadapter service was successfully started Starting staui Service.......... staui service was successfully started #
Replace the Oracle Certificate
-
Start a supported Web browser on your computer and enter the HTTPS/SSL version of the URL for the STA application.
https://STA_host_name:port_number/STA/
Where:
-
host_name is the hostname of the STA server.
-
port_number is the STA port number you specified during installation. The default HTTP port is 7021; the default HTTPS port is 7022.
-
STA must be uppercase.
For example:
https://staserver.example.com:7022/STA/ -
-
Select I Understand the Risks on the This Connection is Untrusted screen.
-
Click Add Exception.
-
To specify a certificate for your organization, click Get Certificate on the Add Security Certificate screen and select the appropriate file.
-
Click Confirm Security Exception.