| Oracle® Retail Process Orchestration and Monitoring Security Guide Release 22.0 F52345-01 |
|
 Previous |
 Next |
| Oracle® Retail Process Orchestration and Monitoring Security Guide Release 22.0 F52345-01 |
|
 Previous |
 Next |
Process Orchestration and Monitoring (POM) Cloud Service is a Java based application deployed on Oracle's Global Business Unit Cloud Services 3.x Platform Services. It is used by other retail cloud services to set up, administer, execute and monitor their batch schedules. The applications are deployed in a highly available, high performance, horizontally scalable architecture. As of release 19.0.001, POM Cloud Services uses either Oracle Identity Cloud Service (IDCS) or Oracle Cloud Infrastructure Identity and Access Management (OCI IAM) as its identity provider (IDP). Information about logical, physical and data architecture in this document focuses on how the architecture supports security.
|
Note: Some Oracle Retail Process Orchestration and Monitoring Cloud Service deployments currently on versions 19.0 and lower use an instance of Oracle Identity Management (IDM) Suite as an identity provider. As these deployments are upgraded to 19.0.001 and transitioned to GBUCS3, their respective customers' authentication will be transitioned to use IDCS or OCI IAM. Oracle Retail will move any user and group information currently on IDM suite to the customer's IDCS or OCI IAM tenancy. |
This section does not explain the complete architecture of the Process Orchestration and Monitoring Cloud Service, but instead focuses on the high-level aspects that relate to security.
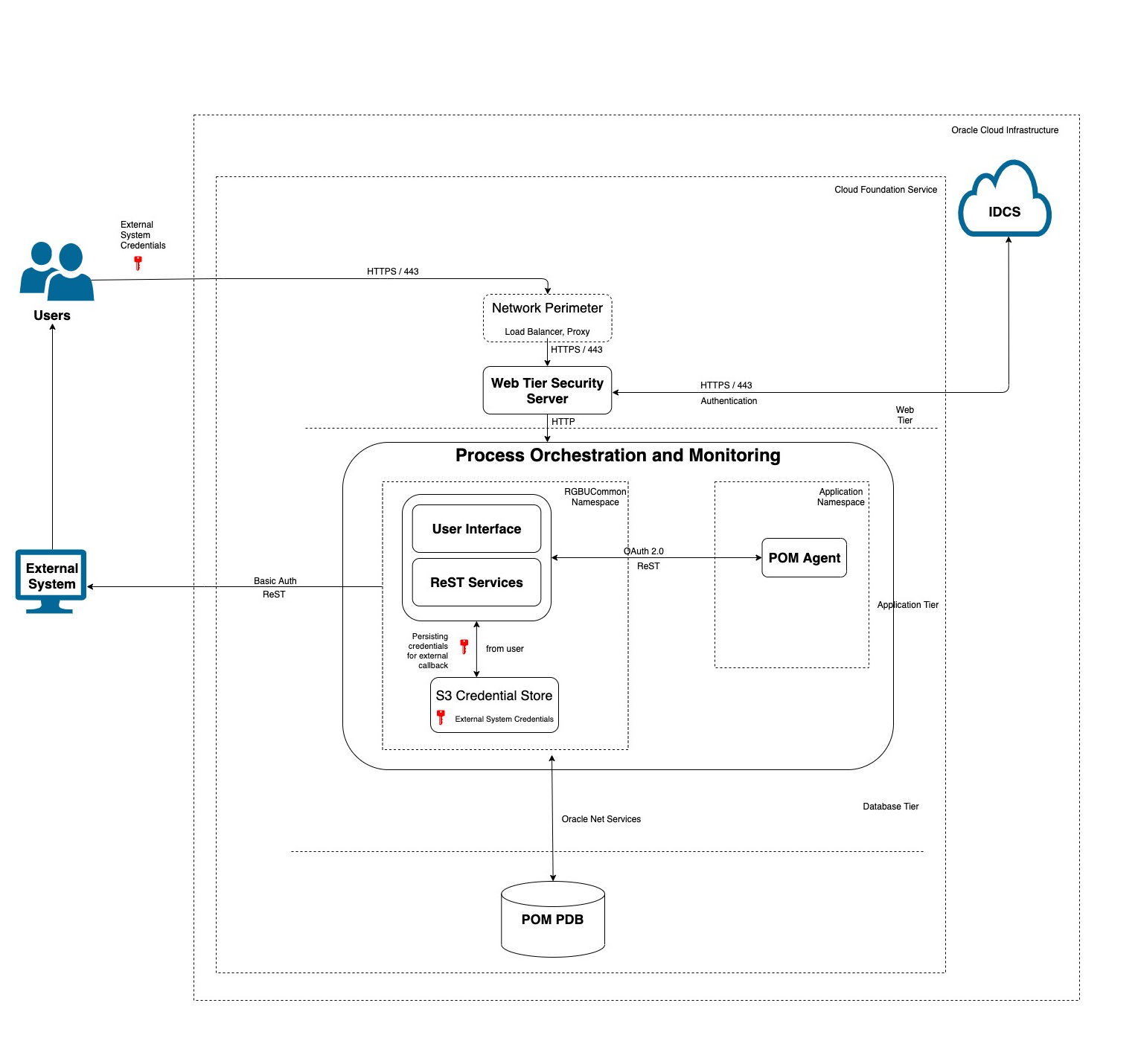
Most customer access to the Process Orchestration and Monitoring (POM) Cloud Service is through the web tier. The web tier contains the perimeter network services that protect the Process Orchestration and Monitoring application and associated applications from the internet at large. All traffic from the web tier continues to the Web Tier Security Server (WTSS), which in turn uses the customer's Oracle Identity Cloud Service (IDCS) or Oracle Cloud Infrastructure Identity and Access Management (OCI IAM) tenancy to perform authentication. More information about authentication through IDCS or OCI IAM is provided later in this document.
The underlying container DBaaS includes one pluggable database (PDB). Applications are able to access the POM schema on the POM PDB using Oracle Net Services aka SQL*Net. Transparent data encryption (TDE) is set during provisioning.
POM Cloud Service authenticates native rest services using OAUTH2.0 through IDCS or OCI IAM. As a common authentication pattern is used, web service users are subject to the same strong controls as application users. All rest service calls are logged in the application logs.
To reduce attack surface, access to the POM Cloud Service from the open internet is very limited. As described in the Architecture section of this document, Business Users (on a web browser) and also any other external web service endpoints access application over https/443.Network Perimeter blocks requests from certain blacklisted IPs as configured. Firewall and load balancer pass traffic to the WTSS server which in turn to requests authentication (through outbound proxy) from the customer's Identity Cloud Service (IDCS) or Oracle Cloud Infrastructure Identity and Access Management (OCI IAM) tenancy.
Actual batch job processing is managed by a component called POM Agent which is provided by the POM team to the corresponding Application teams.This component is packaged as part of the Application and it communicates with POM through ReST endpoints.
Process Orchestration and Monitoring Cloud Service provides a callback feature which sends a batch job's status to the customer's system. Additionally, POM provides a facility for the customer to create or modify the URL and credentials for that system which are stored in the S3 store.
Readers should refer to the following links for additional information about Oracle Cloud delivery and IDCS or OCI IAM.
https://www.oracle.com/assets/ocloud-hosting-delivery-policies-3089853.pdf