Implementing Web Server SSL/TLS Encryption
This section provides an overview of web server SSL/TLS encryption and discusses how to:
Configure web server SSL/TLS encryption.
Implement web server SSL/TLS encryption.
This section discusses:
Outbound web server SSL/TLS encryption.
Inbound web server SSL/TLS encryption.
Outbound Web Server SSL/TLS Encryption
This section discussed outbound web server SSL/TLS encryption.
Before the integration starts, your integration partner generates a key pair that consists of a private key and a public key. The private key is placed in its web server keystore. The public key is placed in a digital certificate.
You contact the integration partner's site using a secured URL that begins with HTTPS. The integration partner's site responds by sending you its web server digital certificate, which contains the public key of the key pair it generated prior to initiating the integration.
Image: Outbound Web Server SSL/TLS Encryption Processing
This diagram shows the processing that occurs on outbound transactions when web server SSL/TLS encryption is implemented. The diagram shows all possible security processing for an outbound integration to show where in the processing flow SSL/TLS encryption occurs. However, the SSL/TLS encryption steps are highlighted.
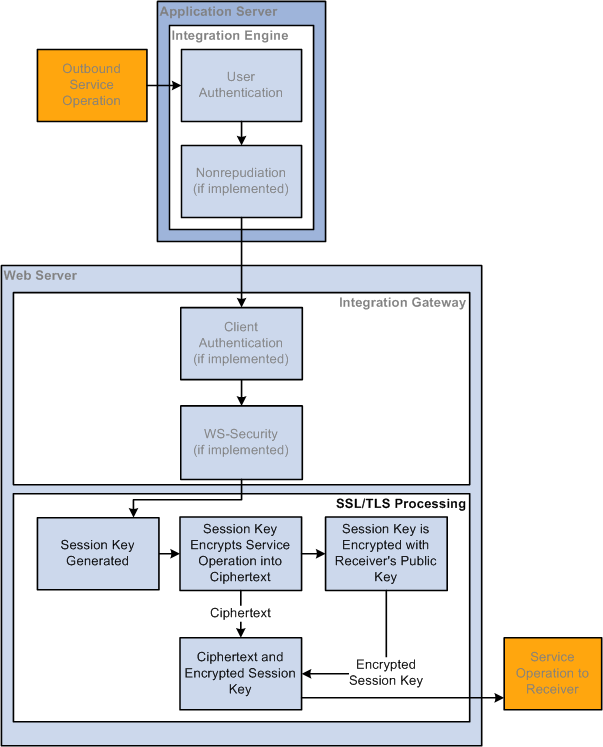
Your web server generates a session key to encrypt the plain text outbound request contents into ciphertext. Then the web server encrypts the ciphertext and session key using your integration partner's public key that was sent to you in the digital certificate.
The session is now secure and all communication is encrypted and can only be decrypted by you and your integration partner.
When the request arrives at your integration partner's web server, the integration partner's web server uses its private key to decrypt the ciphertext and session key. It then uses the session key to decrypt the ciphertext and extract the service operation contents in plain text.
Inbound Web Server SSL/TLS Encryption
This section discusses inbound web server SSL/TLS encryption.
Before the integration starts, you generate a key pair that consists of a private key and a public key. You place the private key in your web server keystore and the public key gets placed in a digital certificate.
For inbound web server SSL/TLS encryption processing, your integration partner contacts you using a secured HTTPS URL. Your web server responds by sending the integration partner a web server digital certificate that contains your public key. The integration partner's web server goes through the outbound processing described in the previous section.
Image: Inbound Web Server SSL/TLS Encryption Processing
This diagram illustrates the processing that occurs on inbound transactions when web server SSL/TLS encryption is implemented. The diagram shows all possible security processing for an inbound integration to show where in the processing flow SSL/TLS encryption occurs, with SSL/TLS encryption processing highlighted in the foreground.
The SSL/TLS encryption processing steps highlighted in the diagram are the receipt of the ciphertext and encrypted session key, the system’s descryption of the session key and receiver’s private key, and the decryption of the ciphertext with the session key.
After this SSL/TLS encryption processing, the service operation passes to the application server for additional processing.
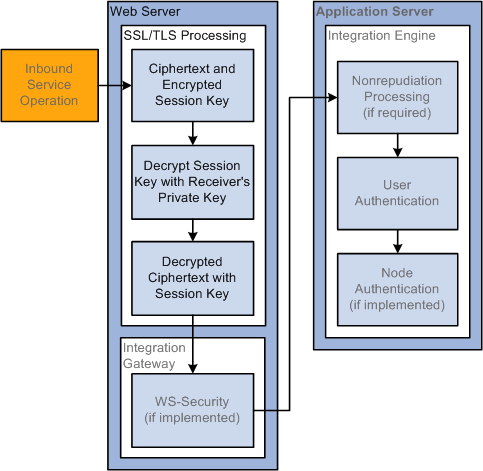
When the service operation arrives on your web server, it is one package that contains the ciphertext (encrypted service operation contents) and the encrypted session key that decrypts the ciphertext.
Your web server uses its private key to decrypt the ciphertext and session key. It then uses the session key to decrypt the ciphertext into a plain text service operation.
You must set up web server-based digital certificates to implement web server SSL/TLS encryption.
Configuring web server SSL/TLS encryption involves the following tasks:
Supply the digital certificates containing the public and private keys required for encrypted transactions. You install these certificates in the web server keystore. You configure the web server to recognize and use its installed certificates for SSL/TLS transactions.
Edit the Integration Gateway Certificates section of the integrationGateway.properties file to convey parameters for the web server certificates that you installed in the gateway keystore.
Integration Gateway Properties File Parameter
Description
ig.certificateAlias
Certificate alias.
ig.certificatePassword
Certificate alias password.
For outbound transactions you must change the value of the HTTP target connector's PRIMARYURL;URL property to start with https:// instead of http://. You can apply this setting on a node-by-node basis, or apply it to the gateway as a whole, which will use it as the default setting for all nodes. The HTTP target connector makes the necessary SSL/TLS connection at runtime.
Receipt of HTTPS requests is nearly automatic. When the integration gateway's HTTP listening connector receives an HTTPS request, it is forwarded to the default local node for authentication.