ROLE TRANSACTION MAPPING
Authorization Workflow
Authorization is unified user role management system which entitles user a particular authority known as ‘Role’ against a targeted ‘Resource’ of an application. Authorization allows an organization to protect its resources by defining and managing policies that control access to, and usage of, these resources.
Access privileges are defined in a policy by specifying who can do what to which resource. Current Authorization supports the creation of Role Based Authorization Policies. This mapping allows users in external groups to access resources as specified by the Application Roles.
Authorization consists of multiple policy domains for logical separation of policies. Each Policy Domain holds multiple policies for that policy domain. Policy determines access permissions on different resources specific to each entity. The policy consists of relation between one or more resources/ entitlements and roles.
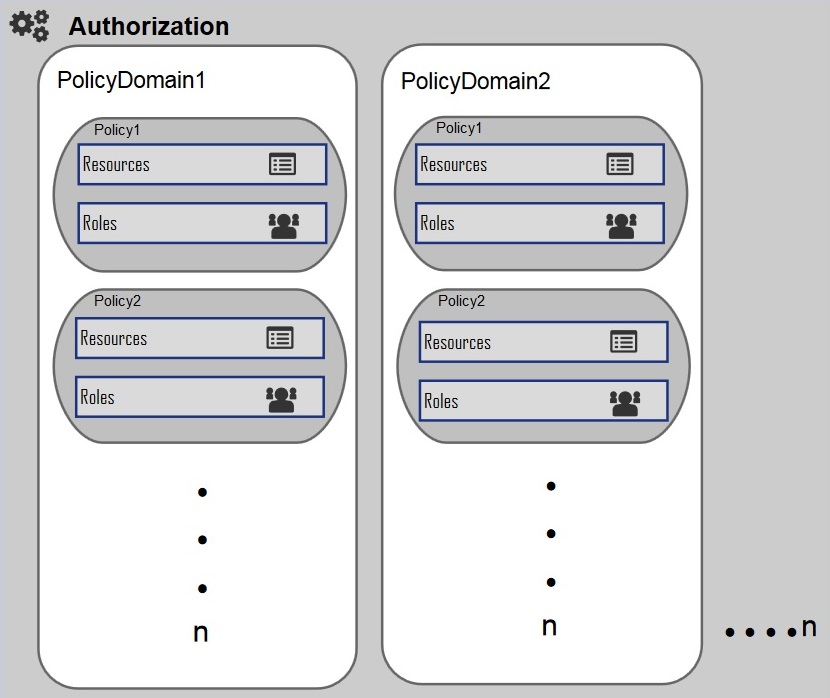
Below diagram shows the relationship and hierarchy of Authorization components like Policy Domain, Policy, Resources, and Roles.
Policy Domain
A Policy Domain is a container for multiple policies created in the system.
One policy domain holds group of policies defined for a specific region. Administrator![]() Administrator is a set of individuals that administer the applicant/Affiliate entity. For example, Accountants, Authorized Signatories for organizations, Power of Attorney for individuals. can create, update, delete Policy domain.
Administrator is a set of individuals that administer the applicant/Affiliate entity. For example, Accountants, Authorized Signatories for organizations, Power of Attorney for individuals. can create, update, delete Policy domain.
Policy
Policy defines mapping between resources/entitlements and application roles/enterprise roles.
Each policy can be designed to PERMIT or DENY access to resources depending on business regulations. Policy can have multiple resources or multiple application roles.
When there is a need for a group two or more resources, administrator can create an entitlement and add it in the policy for user authentication.
Resource
A Resource is the complete path of a method provided in the code. As per the business policy, the administrator may want to give access to that code only after login. In such a scenario, this particular resource is added to a policy for a given user role.
Application Role
Application role is a logical grouping of one or many enterprise roles.
It defines criteria for mapping enterprise Roles to a user defined role. One target Application may have several different Application Roles, with each one assigned a different set of privileges offering more fine-grained access.
One Enterprise Role can be mapped to many Application Roles. For example, the Enterprise Role employee (stored in LDAP-based identity store) can be mapped to the Application Role customersupport member (defined in one Application) and to the Application RoleIT member (defined in another Application).
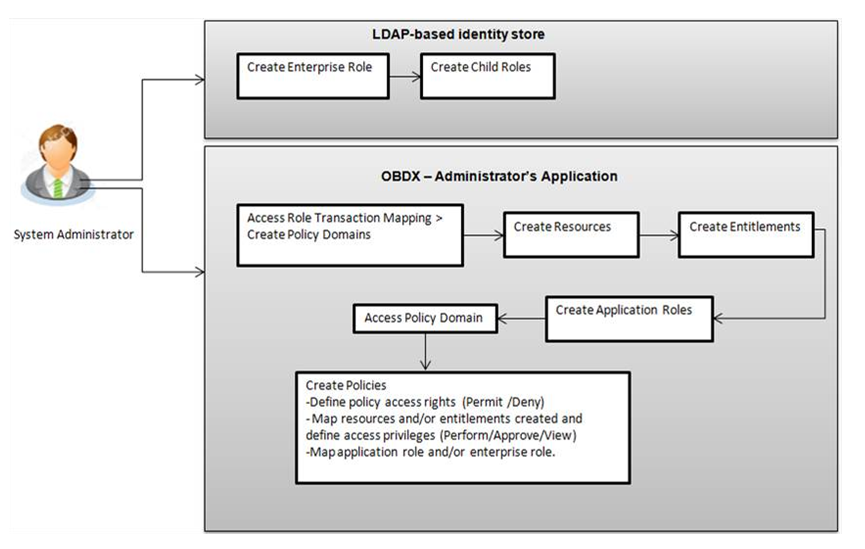
Role to Transaction Mapping (Authorization) allows the System Administrator to:
Business scenario 1
- ZigBank wants to create three enterprise roles – Administrator, Corporate users, Retail users (Define in LDAP based identity store)
- Further, the requirement is to enable following child roles under each enterprise role (Define in LDAP based identity store)
- Administrator – Maker and Approver
- Corporate Users – Maker, Viewer, Approver, Corporate Admin Maker, Corporate Admin Approver
- Retail User – Customer
- Out of box, 2 Domains are available, one for administrator types of users and another is for bank’s customers. Additional domain can be created, if required.
- Create resources for new transactions in addition to the resources which are available out of box (Resource is the complete path of a method provided in the code),
- Create entitlements e.g. create an entitlement with all payment related resources. (entitlement is logical grouping of resources)
- Create one application role and map to all required enterprise roles for commonly used transactions like mailbox, change password etc if required.
- Access policy Domain > ZBAdmin.
- Create a policy and define policy effect - Permit or Deny
- Map resources and/or entitlements created and define access privileges (Perform/Approve/View)
- Map application role and/or enterprise role.
Workflow
Business scenario 2
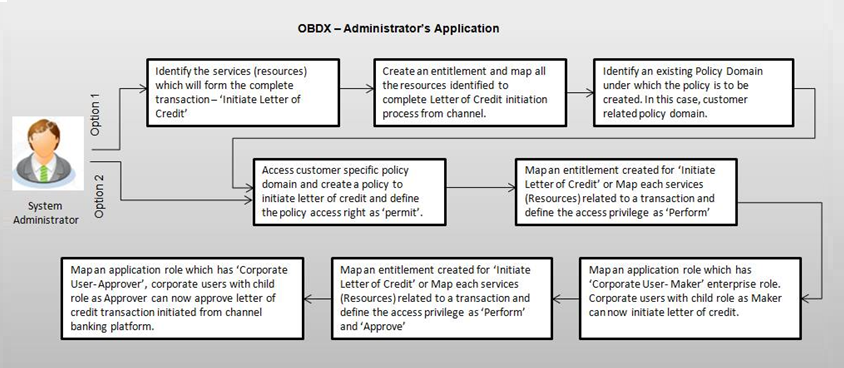
After few months of Bank’s operation, Zigbank wants to now introduce the functionality to ‘Initiate Letter of credit’ from channel banking platform and wants to enable the feature only to Corporate User with child role as Maker so that the users can initiate the transaction from channel. Also the requirement is that a Corporate User with child role as Approver should be able to approve the transaction initiated by maker.