User Authentication
The Rules Palette application provides an out-of-the box user authentication mechanism. Out-of-the box user authentication is performed for interactive users to access the system. On the application's login screen, interactive users are prompted to provide a username and password to authenticate to the server. Web services are protected with WS-Security, which requires outgoing web service calls to carry a security header with a user name and password.
Both web service and interactive user authentication are implemented through the same authentication service provided by the business logic tier of the Rules Palette. The authentication service retrieves a matching user record from the database that contains basic user information and a secure digest of a password. The password digest is then compared to the digest of the incoming password, and an authentication decision is made based on the result of the comparison.
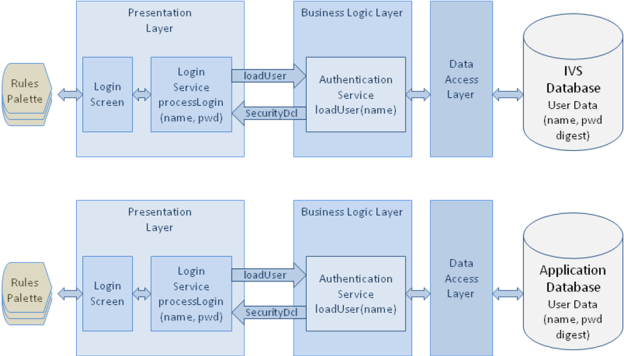
Figure 2. Rules Palette User Authentication (Top is IVS environment, bottom is non-IVS)
The Rules Palette's Web Utility also provides an out-of-the-box user authentication mechanism. On the application's login screen, interactive users are prompted to provide a username and password to authenticate to the server.
The Upgrade Utility uses the same authentication mechanism used by the Rules Palette. Additional authorizations are granted to those users who are allowed to use the Upgrade Utility.
The encrypted password digest is created by the application when a user is created. When a new OIPA environment is created using the Rules Palette's Web Utility, the process expects input from the user for the configuration of the encryption parameters to be used by the encryption algorithm. The settings include the particular encryption algorithm (from the list of the supported algorithms below), and the number of iterations of the algorithm.
- SHA-256
- SHA-384
- SHA-512
The number of encryption iterations is a value between 1000 and 9999. A higher number of iterations makes the password more secure, but also requires more computation to encrypt. These settings are used within the Rules Palette, its Web Utility and within the OIPA Application. For more information, please refer to the associated version of the Rules Palette Help that is located on the Oracle Technology Network.
