User Management
User Registration in Rules Palette Web Utility
A user must have a Web Utility User Account identified by a username and password to log into the Rules Palette Web Utility.
Because of security considerations, the Rules Palette's Web utility does not come pre-configured with any default user accounts. When the Web Utility is launched to create an environment, the process provides the ability to create the first Web Utility administrator account.
This administrator account can then be used to create new accounts using the functionality provided in the web application.
Rules Palette
A user must have an existing Rules Palette user account identified by username and password to log into the Rules Palette application. A Rules Palette administrator uses the Rules Palette to create a new Rules Palette user account.
The Rules Palette's Web Utility allows for the creation of the first Rules Palette Administrator account when a new environment is created in the Web Utility. In addition to the user, it also creates a Security Role with administrative privileges. This administrator account is then used in the Rules Palette to create new Rules Palette user accounts. The administrator can also add other security roles with appropriate privileges that enable various mixes of functionalities in the Palette. When creating a new Palette user account, an administrator enters the following information:
- In an IVS environment:
- User's login name and password
- Security role to which the user belongs
- In a non-IVS environment:
- User's login name and password
This information is persisted in the IVS database (for IVS environments) or application database (for non-IVS environments), with the encrypted password digest stored as discussed in the User Authentication section of this document. The user's security role determines what features of the system are available to the user.
User Privileges and Role-Based Access Control
The user privileges and access restrictions implementation is based on the role-based access control (RBAC) model. According to the model, user permissions are assigned to a specific role that is created for various job functions. A user who is assigned to a particular security role gains permissions through that role to perform particular system functions. A user can only be assigned to one security role at a time.
For example, users that are assigned to the Configuror role will only have the ability to change rule configuration. A user in a Security Manager role should be able to update various security settings for users and security roles. A user in an administrator role is usually allowed access to all resources.
The following picture shows what application resources are protected by the security.
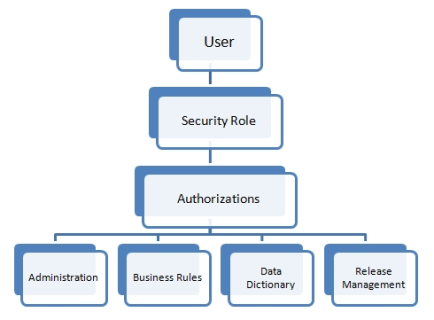
Figure 3. Hierarchy of User Authorizations
In setting up the security roles, an administrator needs to be careful to include only the minimum set of permissions that allow users of a particular security role to perform their job functions.
For more information on how to create security roles and manage user accounts, please refer to the Rules Palette Help.
