Inserting Customized SIP Headers in an Outgoing INVITE
When the Oracle Communications Session Border Controller establishes a new TLS connection, it caches the following peer certificate attributes:
- Certificate Subject Name
- Certificate Subject Alternative Name (only DNS)
The Oracle Communications Session Border Controller constructs a customized P-Certificate-Subject-Common-Name SIP header and inserts the header into the outgoing INVITE with the Certificate Subject Name. The Oracle Communications Session Border Controller also constructs and inserts in the outgoing INVITE one or more P-Certificate-Subject-Alternative-Name SIP headers.
If you enable this capability and the incoming INVITE already has P-Certificate-Subject-Common-Name and P-Certificate-Subject-Alternative-Name headers, the Oracle Communications Session Border Controller strips them before inserting the new customized ones. It does so to avoid the risk of any attempt to spoof the headers and thereby gain unauthorized access to the UM server.
The following diagram shows a scenario where the calling party establishes a TLS connection with the Oracle Communications Session Border Controller. Because mutual authentication is enabled, the Oracle Communications Session Border Controller receives the peer certificate and caches required information from it. This information is inserted in the outgoing INVITE.
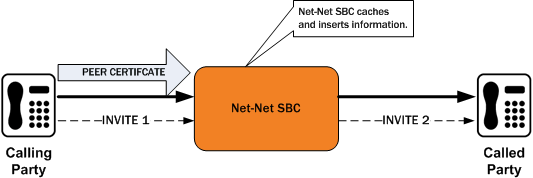
The peer certificate from the calling party during the TLS handshake with the Oracle Communications Session Border Controller looks like the following example.
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 9 (0x9)
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=US, ST=MA, L=Woburn, O=Smith Securities, OU=Certificate Authority Dept, CN=Smith Certificate Authority/emailAddress=Smith@CA.com
Validity
Not Before: Dec 10 21:14:56 2009 GMT
Not After : Jul 11 21:14:56 2019 GMT
Subject: C=US, ST=MA, L=Burlington, O=Acme Packet, OU=Certificate Authority Dept, CN=*.acme.com/emailAddress=ph1Client@acme.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (2048 bit)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Issuer Alternative Name:
email:Smith@CA.com
X509v3 Subject Alternative Name:
DNS:gw1.acme.com, DNS:gw3.ano.com, DNS:gw2.some.com
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
Signature Algorithm: sha1WithRSAEncryption
The outgoing SIP INVITE (INVITE 2 in the diagram) looks like the following sample. Bold text shows where the Oracle Communications Session Border Controller uses information from the certificate.
INVITE sip:222222@acme.com:5060 SIP/2.0 Via: SIP/2.0/UDP 172.16.27.113:5060;branch=z9hG4bK4jmg29cmm8l0cg7smmrn85o4q7 From: 111111 <sip:111111@acme.com>;tag=_ph1_tag To: 222222 <sip:222222@acme.com> Call-ID: _1-2_call_id-10147@acme.com-1- CSeq: 1 INVITE Contact: <sip:111111@172.16.27.113:5060;transport=udp> P-Certificate-Subject-Common-Name: *.acme.com P-Certificate-Subject-Alternative-Name: gw1.acme.com P-Certificate-Subject-Alternative-Name: gw3.ano.com P-Certificate-Subject-Alternative-Name: gw2.some.com Max-Forwards: 69 Subject: TBD Content-Type: application/sdp Content-Length: 138 Route: <sip:222222@172.16.27.188:5060;lr> v=0 o=user1 53655765 2353687637 IN IP4 172.16.27.113 s=- c=IN IP4 172.16.27.113 t=0 0 m=audio 20000 RTP/AVP 0 a=rtpmap:0 PCMU/8000



