Querying Data Permission Security
To query data permission security, use the Security Data Inquiry component.
These topics discuss querying data permission security.
|
Page Name |
Definition Name |
Usage |
|---|---|---|
|
SCRTY_CLASS_DISP |
Query the actual view SQL text used in a specific component. Enter the name of the view you want to query in the View Name field. You can use the SQL Object ID to view the definitions of the SQL objects used in the view. |
|
|
SCRTY_TRANS_DISP |
Display the security data for a selected security set and access type. You can view the user security data using the type and the transaction data secured by the type. |
|
|
SCRTY_OPR_DISP |
Query and review a user's security data, including assigned roles and permission lists. |
|
|
SCRTY_SJT_PERSON |
Review the transaction data used to secure a person's data and the permission lists and users who have access the person. |
|
|
Find in SJT_PERSON_USF Page (See Find in SJT_PERSON Page) |
SCRTY_SJT_PER_USF |
(USF) Review the transaction data used to secure a person's data and the permission lists and users who have access the person. |
|
SCRTY_SJT_DEPT |
Review the transaction data used to secure a department's data and the permission lists and users who have access the department. |
|
|
SCRTY_SJT_RSOPN |
Review the transaction data used to secure a job opening and the permission lists and users who have access the job opening. |
The Security Data Inquiry component enables you to quickly and easily query aspects of your data permission setup in the event that you have questions or concerns about the implications of the access you've set up. The component consists of seven pages, each querying a different aspect of HCM data permission:
|
Page |
Description |
|---|---|
|
Find Search View |
Use this page to review details about the security search view used by a component. There are a number of different search views and even the same component can use a different view, depending on which menu it is on. The security view text tells you which security set the data in the component falls into and if there is any special selection criteria. To use query search views you need to know the:
|
|
Display Security Data |
Use this page to review security data for the selected security set and security access type. You can further refine the query by selecting a user ID, permission list, or security key value, or a combination of the three. Review both the permission list access and the transaction data secured by the parameters. For example, you can review the data permission assigned to the permission list MyJobs for security set PPLJOB and security access type 001 (department 11000). Or you can review the transaction data available to permission list MyJobs for security set PPLJOB and security access type 002 (112 people with jobs). To compile a list of access for more than one access type, download the data in the grids to Microsoft Excel |
|
User Security Data |
Review a user's data permission profile, including his or her roles, role-based permission lists, and row security permission lists, and the data permission associated with them. The query only includes the roles and role-based permission lists that contain data permission security. |
|
Use this page to review the access to transaction data. You can review:
|
Use the Find Search View page (SCRTY_CLASS_DISP) to query the actual view SQL text used in a specific component.
Enter the name of the view you want to query in the View Name field. You can use the SQL Object ID to view the definitions of the SQL objects used in the view.
Navigation
Image: Find Search View page
This example illustrates the fields and controls on the Find Search View page. You can find definitions for the fields and controls later on this page.
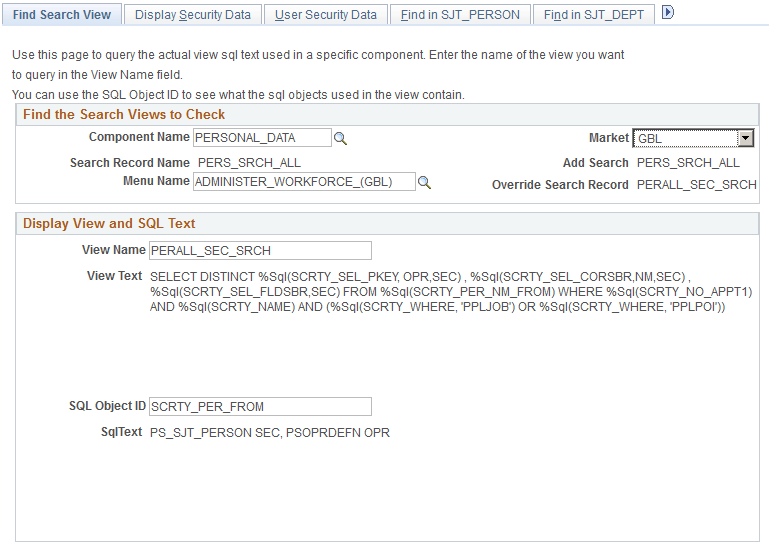
To review the view and SQL text used in a security search view indicate which search view to search by entering the:
Component name
Market
Menu name
|
Field or Control |
Definition |
|---|---|
| Search Record Name |
Displays the component's default search record when you access the component in update or display mode. Note: You can assign an override search record to a component at the menu level. If the component uses an override search record, the search record displayed in the Override Search Record will be different from this one and you should search it instead. |
| Add Search |
Displays the component's search record when you access the component in add mode. |
| Override Search Record |
Displays the component's override search record when you access the component in update or display mode. |
| View Name and View Text |
To review the text from a search record view, enter it into the View Name field. The system displays the view text when you tab out of the View Name field. |
| SQL Object ID and SqlText |
To review the SQL text within an SQL Object used by the view, enter the SQL object ID into the SQL Object ID field. The system displays the SQL text when you tab out of the SQL Object ID field. Note: SQL objects are used to store common SQL. |
For example, the security search view for the Personal Data component on the Administer Workforce menu, when accessed in Update mode, is PERALL_SEC_SRCH. This search view uses the security sets PPLJOB and PPLPOI and the transaction security join table SJT_PERSON. The view text has a special selection criteria to not return rows where the APPT_TYPE (appointment type) is equal to 1.
You can use this information to review the security data in greater detail. Perhaps to see what data is secured in security set PPLPOI or if the record a user is trying to access in this component has an appointment type value equaling 1 and that is why the record is unavailable.
See PeopleTools: Application Designer Developer's Guide.
Use the Display Security Data page (SCRTY_TRANS_DISP) to display the security data for a selected security set and access type.
You can view the user security data using the type and the transaction data secured by the type.
Navigation
Image: Display Security Data (1 of 3)
This example illustrates the fields and controls on the Display Security Data (1 of 3). You can find definitions for the fields and controls later on this page.
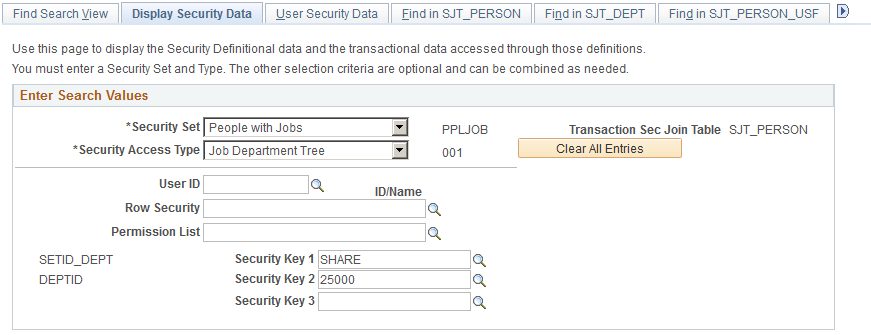
Image: Display Security Data (2 of 3)
This example illustrates the fields and controls on the Display Security Data (2 of 3). You can find definitions for the fields and controls later on this page.
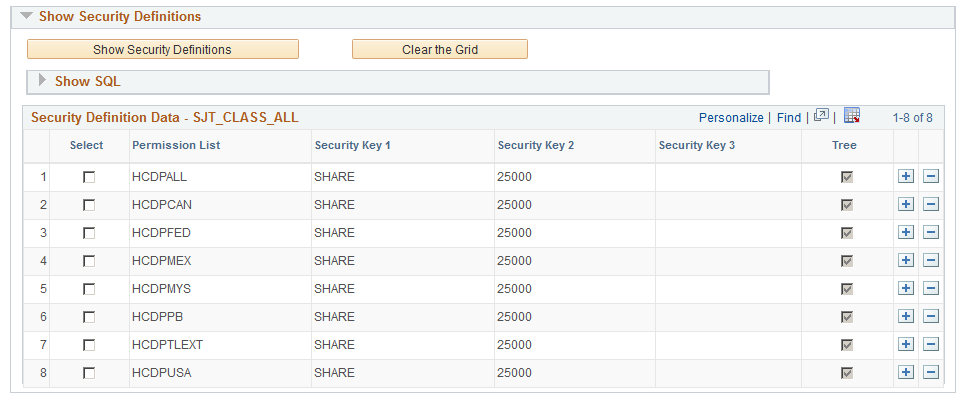
Image: Display Security Data (3 of 3)
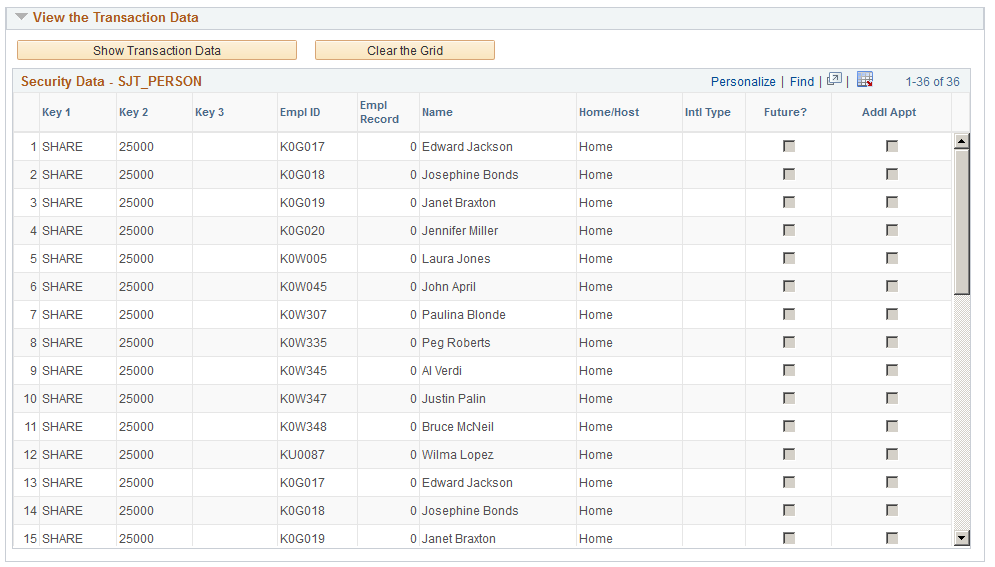
This example illustrates the fields and controls on the Display Security Data (3 of 3). You can find definitions for the fields and controls later on this page.
Click the Clear All Entries button to clear the search value fields.
Enter Search Values
|
Field or Control |
Definition |
|---|---|
| Security Set, Transaction Sec Join Table , and Security Access Type |
Select the security set and security access type whose security data you want to review. The system displays the transaction security join table used by the security set. |
Note: If you want to review date permission security data for more than one security access type or for more than one of the additional parameters below, down the results in the Show Security Definitions and View the Transaction Data grids to Microsoft Excel and add to them as you perform your search.
To further refine the search within the selected security set or security access type, enter one or more values in these fields:
|
Field or Control |
Definition |
|---|---|
| User ID and ID/Name |
To review a user's data permission security data, select the user ID. The system displays the ID and name of the person assigned to the selected profile. |
| Row Security |
To review the data permission security data of a row security permission list, select the permission list. When you select a tree-based security access type and enter a user ID, the system enters the row security permission list associated with the user ID. This field is only available when you select a tree-based security access type. |
| Security Key 1, Security Key 2, and Security Key 3 |
To review the data permission security data for a selected security key, select the values (for example, to review the security data for department 10000, enter the department setID SHARE in Security Key 1 and the department id 10000 in Security Key 2). |
Expand the Show SQL group boxes in the Show Security Definitions group box and the Viewing Transaction Data group box to review the SQL used to query SJT_CLASS_ALL table and transaction security join table for this query.
Show Security Definitions
Click the Show Security Definitions button to display the user security data that meets the search criteria.
The grid displays the permission list and the security key values that the permission list can access.
|
Field or Control |
Definition |
|---|---|
| Tree |
The system selects this check box for row security (tree-based) permission lists. |
View the Transaction Data
Click the Show Transaction Data button to display the transaction data stored in the transaction security join table of the selected security set. The rows in the grid vary depending on which security set you are querying.
|
Field or Control |
Definition |
|---|---|
| Security Key 1 or Key 1, Security Key 2 or Key 2, and Security Key 3 or Key 3 |
Displays the transaction security data (and the necessary key values) used to secure this row of data. |
| SetID, Department, Effective Date, and Description |
For rows of department transaction data, displays the set ID and the department whose data is secured. |
| Job Opening ID |
For rows of recruiting solutions job openings, displays the ID of the job opening whose data is being secured. |
| Empl ID, Empl Record, and Name |
For rows of person transaction data, displays the ID, employee record number (if applicable), and the name of the person whose data is secured. A person with more than one unique empl ID and employee record number combination will have more than one row of data. |
| Home/Host |
This field is for global assignments and indicates if the transaction row is from the home or the host assignment job data record. Only job data records for the global assignment will display Host. |
| Intl Type (international type) |
If you are using special security options for global assignment job data records, this field indicates if this row was created by the system to enable special job security. |
| Future? |
This field indicates of the row comes from a future-dated transaction row. |
| Addl Appt (additional appointment) |
(JPN) Indicates if this is an additional appointment transaction row. |
| WIP Status, Retirement, NOA Code, and Stat Type |
(USF) displays additional information about the job data row. These values are not used to secure data. |
Use the User Security Data page (SCRTY_OPR_DISP) to query and review a user's security data, including assigned roles and permission lists.
Navigation
Image: User Security Data page (1 of 2)
This example illustrates the fields and controls on the User Security Data page (1 of 2). You can find definitions for the fields and controls later on this page.
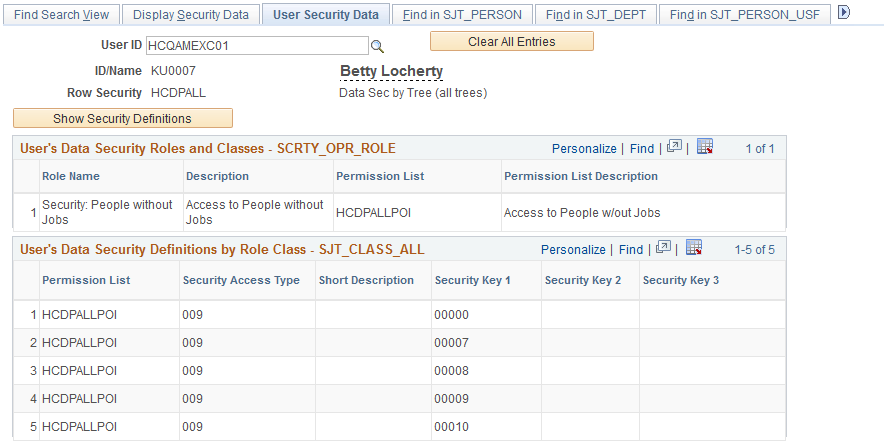
Image: User Security Data page (2 of 2)
This example illustrates the fields and controls on the User Security Data page (2 of 2). You can find definitions for the fields and controls later on this page.
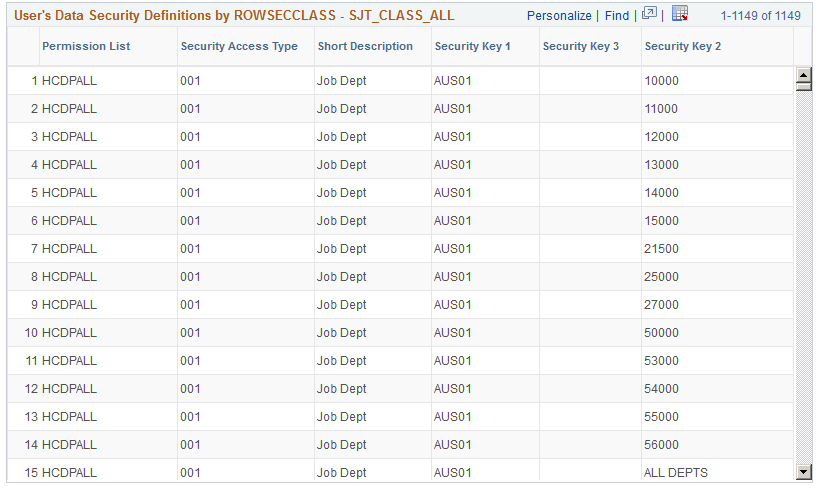
|
Field or Control |
Definition |
|---|---|
| User ID |
Select the user ID of the person whose data permission access you want to query. The system displays the user's name and his or her row security permission list. |
Click the Show Security Definitions button to populate the grids on the page.
User's Data Security Roles and Classes – SCRTY_OPR_ROLE
Displays the roles assigned to the user and the permission lists with data permission assigned to those roles.
Note: The SCRTY_OPR_ROLE table only stores the roles that have permission lists with data permission. The grid does not list roles that do not have data permission .
User's Data Security Definitions by Role Class – SJT_CLASS_ALL
Displays the data permission of the role-based permission lists associated with this user's roles.
User's Data Security Definitions by ROWSECCLASS – SJT_CLASS_ALL
Displays the permissions of the row security permission list assigned to this user.
Use the Find in SJT_PERSON page (SCRTY_SJT_PERSON) or Find in SJT_PERSON_USF page (SCRTY_SJT_PER_USF) to review the transaction data used to secure a person's data and the permission lists and users who have access the person.
Navigation
Image: Find in SJT_PERSON page (1 of 2)
This example illustrates the fields and controls on the Find in SJT_PERSON page (1 of 2). You can find definitions for the fields and controls later on this page.
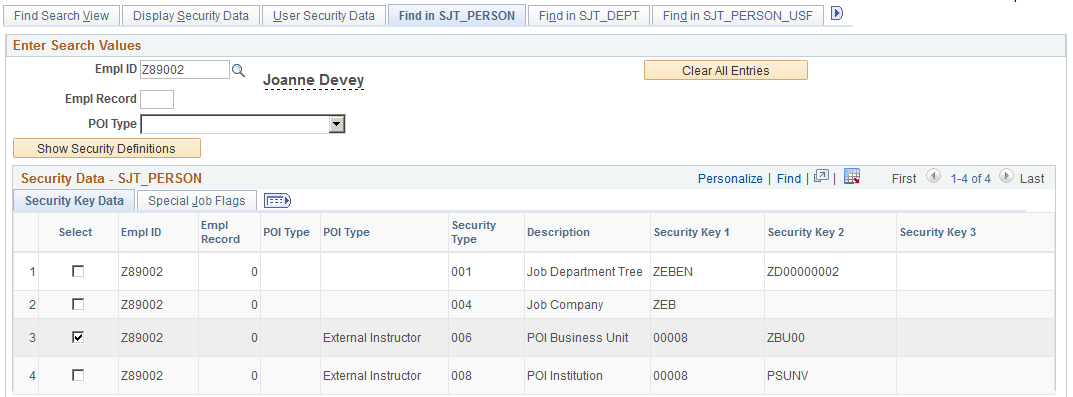
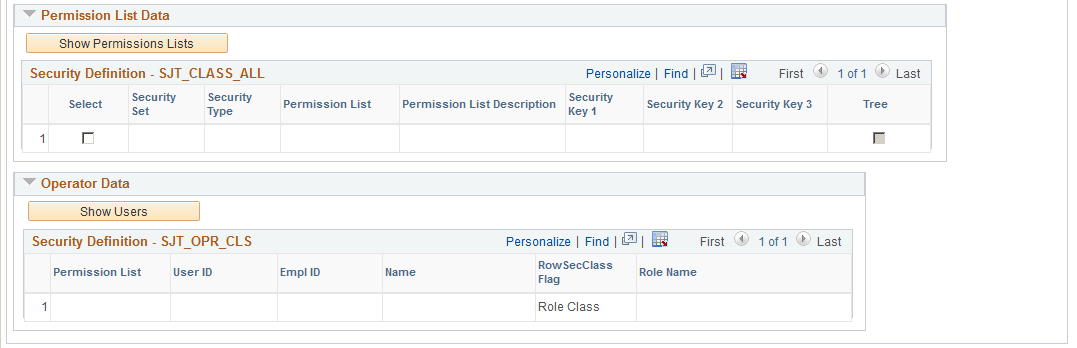
Image: Find in SJT_PERSON page (2 of 2)
This example illustrates the fields and controls on the Find in SJT_PERSON page (2 of 2). You can find definitions for the fields and controls later on this page.
Note: The Find in SJT_PERSON_USF page does not have the option to search for POIs.
Select the EmplID of the person whose transaction security data you want to review. To limit the search to a single job data record, enter the employee record number. To limit the search to a specific person of interest type, select the type.
Click the Show Security Definitions button to populate the Security Data - SJT_PERSON grid with the transaction security data securing this person's record or records.
Security Data – SJT_PERSON
Click the Show Security Definitions button to populate the Security Data - SJT_PERSON grid.
The system lists the rows in SJT_PERSON that match the search criteria you entered. Review the security keys on the Security Key Data tab. Access the Special Job Flags tab to review special security job option data, such as if a row is a future-dated row or if it was created to enable home/host access or additional assignment access.
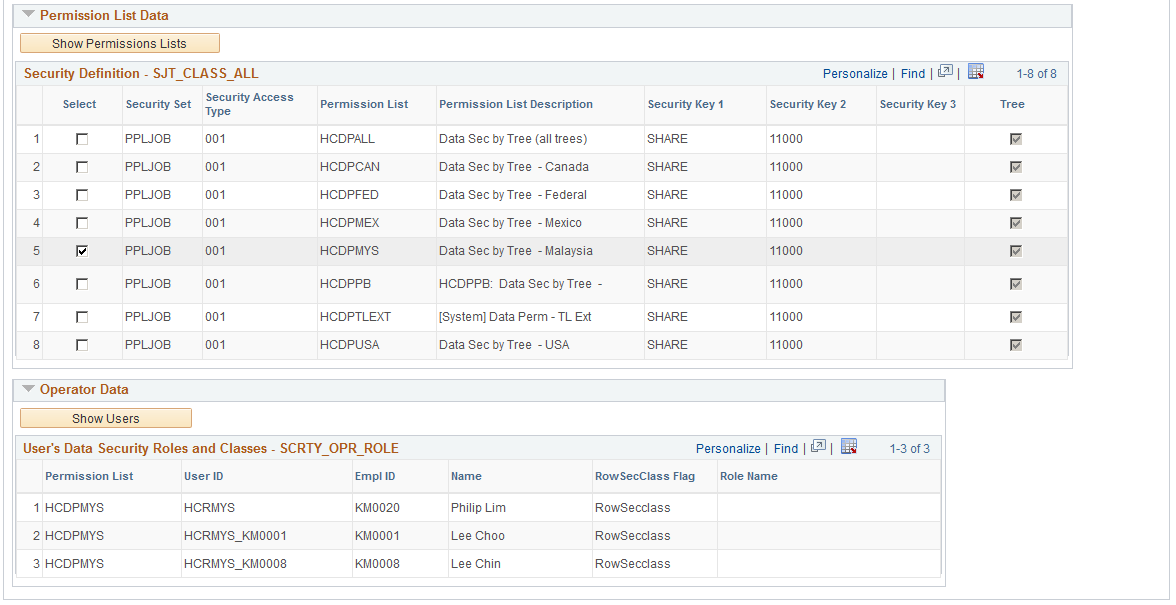
To review which permission lists have data permission access to one or more of these rows, select the rows and click the Show Permission Lists button.
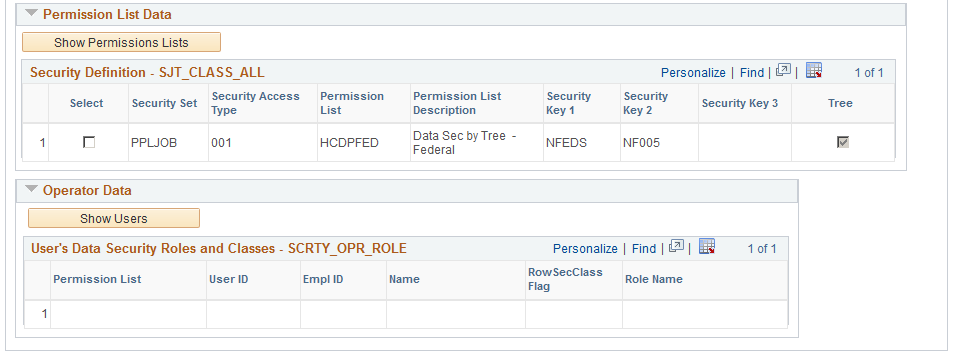
Permission List Data
Click the Show Permission Lists button to populate this grid
For each security set and security access type, the system lists the permission lists that can access the transaction rows you selected.
To review which users are assigned to one or more of these permission lists, select the rows and click the Show Users button.
Operator Data
Click the Show Users button to populate the grid.
The system displays each user assigned to the permission list or lists that you selected and indicates if the permission list is assigned to the user as a row security permission list or role-based (role-class) and, if the permission list is role-based, which role it is assigned to on the user's profile.
Use the Find in SJT_DEPT page (SCRTY_SJT_DEPT) to review the transaction data used to secure a department's data and the permission lists and users who have access the department.
Navigation
Image: Find in SJT_DEPT page (1 of 2)
This example illustrates the fields and controls on the Find in SJT_DEPT page (1 of 2). You can find definitions for the fields and controls later on this page.
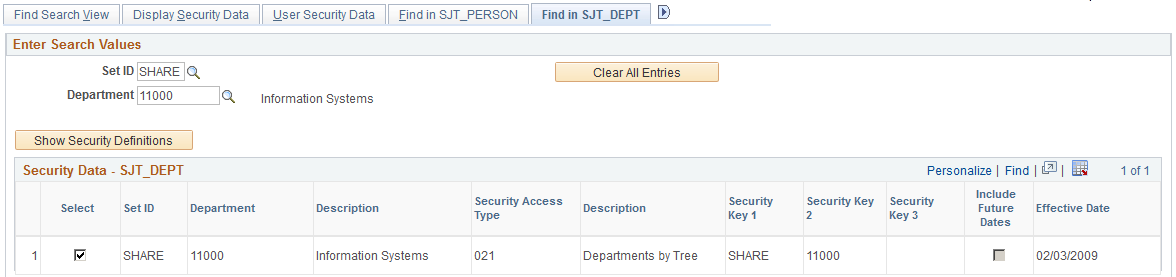
Image: Find in SJT_DEPT page (2 of 2)
This example illustrates the fields and controls on the Find in SJT_DEPT page (2 of 2). You can find definitions for the fields and controls later on this page.
Select the setID and department ID of the department whose transaction security data you want to review.
Click the Show Security Definitions button to populate the Security Data - SJT_DEPT grid with the transaction security data securing this department's record or records.
Use the Find in HRS_SJT_JO page (SCRTY_SJT_RSOPN) to review the transaction data used to secure a job opening and the permission lists and users who have access the job opening.
Navigation
Image: Find in HRS_SJT_JO page (1 of 2)
This example illustrates the fields and controls on the Find in HRS_SJT_JO page (1 of 2). You can find definitions for the fields and controls later on this page.
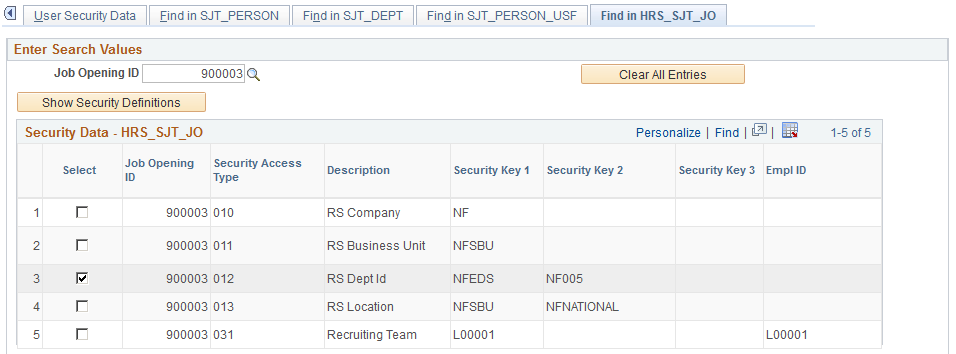
Image: Find in HRS_SJT_JO page (2 of 2)
This example illustrates the fields and controls on the Find in HRS_SJT_JO page (2 of 2). You can find definitions for the fields and controls later on this page.
Select the ID of the job opening whose transaction security data you want to review.
Click the Show Security Definitions button to populate the Security Data - HRS_SJT_JO grid with the transaction security data securing this job opening's record or records.