Integrating Google Apps with OAM and IdP
Google Apps provide a set of services that companies sometimes leverage for their day to day activities, which allow their employees to offload mail, calendar, document storage in the Google cloud.
When a company purchases Google Apps for its employees, it needs to create user accounts in Google and provide the employees with their account information:
-
Username and password to access Google Apps
-
How to set/reset their password in Google Apps (initially, or if the password needs to be reset periodically)
Every time the user needs to access Google Apps, an authentication operation takes place where the user enters the Google Apps credentials, which is different from the on-premise company’s user credentials.
Google Apps supports the SAML 2.0 SSO protocol as a Service Provider, where the Google Apps service for the company can be integrated with the on-premise Federation SSO IdP server in order to:
-
Provide true SSO capabilities for the user: the user authentication state is propagated from the on-premise security domain to Google Apps
-
Do not force the user to manage and remember a different set of credentials
-
Allow the on-premise administrator to control more efficiently password policies locally.
This article describes step by step how to integrate Google Apps as an SP with OAM as an IdP via the SAML 2.0 SSO protocol.
Important Note: Enabling Federation SSO for a domain also affects the administrators for that domain who needs to authenticate via Federation SSO thereafter.
User Mapping
Users in Google Apps are uniquely identified by their email addresses which was set when those users were created.
During a SAML 2.0 SSO flow, the IdP needs to provide the user ID to Google Apps:
-
In the SAML 2.0
NameIDfield With theNameIDvalue set: -
Either to the user’s email address at Google Apps
-
Or the identifying part of the email address (that is, before the @ character)
Let’s take the example of the company ACME who purchased a Google Apps service, for their acme.com domain.
To view a user account in Google Apps, perform the following steps:
-
Launch a browser
-
Go to http://www.google.com/a
-
Click Sign In
-
In the domain field, enter the name of your domain (in this example, www.acme.com)
-
Select Admin Console
-
Click Go
- In the Dashboard, click on Users
- Select a user to view

Description of the illustration Google_SignIn.jpg
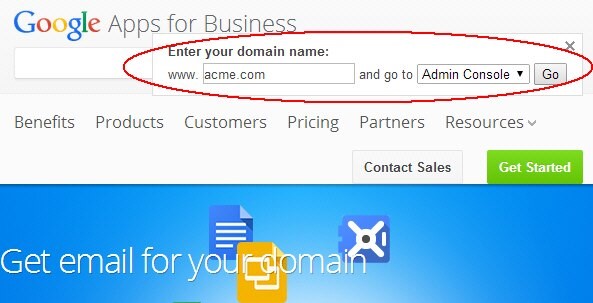
Description of the illustration Admin_Console.jpg
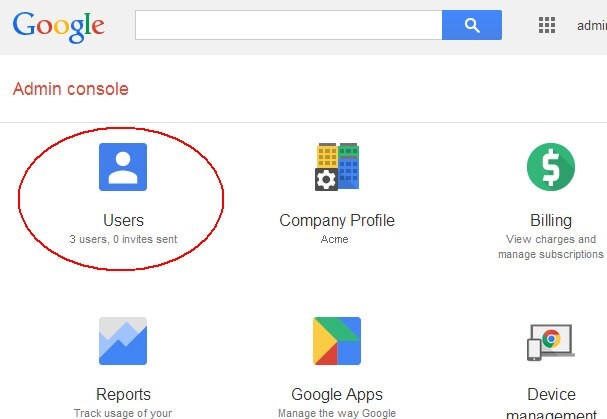
Description of the illustration Dashboard.jpg
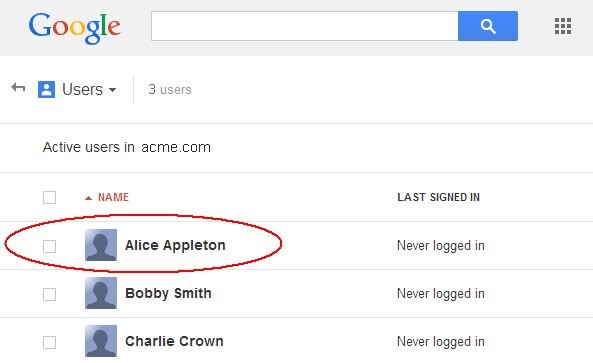
Description of the illustration User_View.jpg
The next screen shows details about the user. The email address is displayed underneath the user’s identity. In this example, the ACME IdP will have to send to Google Apps either alice or alice@acme.com during the SAML 2.0 SSO operation:
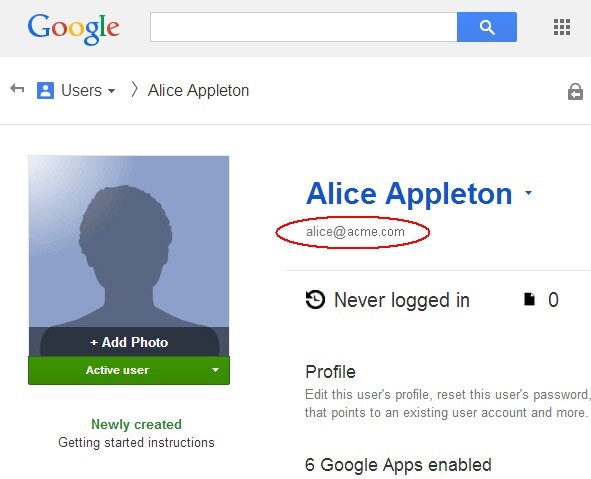
Description of the illustration User_Details.jpg
IdP Configuration
Google Apps Identifier
Google Apps can be configured by the Google Apps administrator to be known to the IdP:
-
Either as
google.com -
Or as
google.com/a/<YOUR_DOMAIN.COM>(for example:google.com/a/acme.com)
This behavior is dictated by the “Use a domain specific issuer” in the Google Apps SSO admin section.
Typically, you would not need to use a specific issuer/providerID, and Google Apps in the SAML 2.0 SSO flow would be known as google.com.
Google Apps SP Partner
To create Google Apps as an SP Partner, perform the following steps:
-
Go to the OAM Administration Console:
http(s)://oam-admin-host:oam-adminport/oamconsole -
Navigate to Identity Federation , Identity Provider Administration
-
Click on the Create Service Provider Partner button
-
In the Create screen:
-
Enter a name for the partner: GoogleApps for example
-
Select SAML 2.0 as the Protocol
-
-
In the Service Details:
-
Click Enter Manually
-
Set the Provider ID to google.com (if in Google Apps you enabled the “Use a domain specific issuer” feature, you would enter
google.com/a/<YOUR_DOMAIN.COM>). -
Set the Assertion Consumer URL to
https://www.google.com /a/<YOUR_DOMAIN.COM>/acs(for examplehttps://www.google.com/a/acme.com/acs) -
Select Email Address as the
NameIDformat
-
-
Select the LDAP User Attribute containing the
userIDthat needs to be provided to Google Apps. In this example, theuidattribute contained theuserID: select User ID Store Attribute then enteruid -
Select the Attribute Profile that is used to populate the SAML Assertion with attributes (default empty profile is acceptable since Google Apps does not expect any SAML
-
Attributes other than the
NameID) -
Click Save
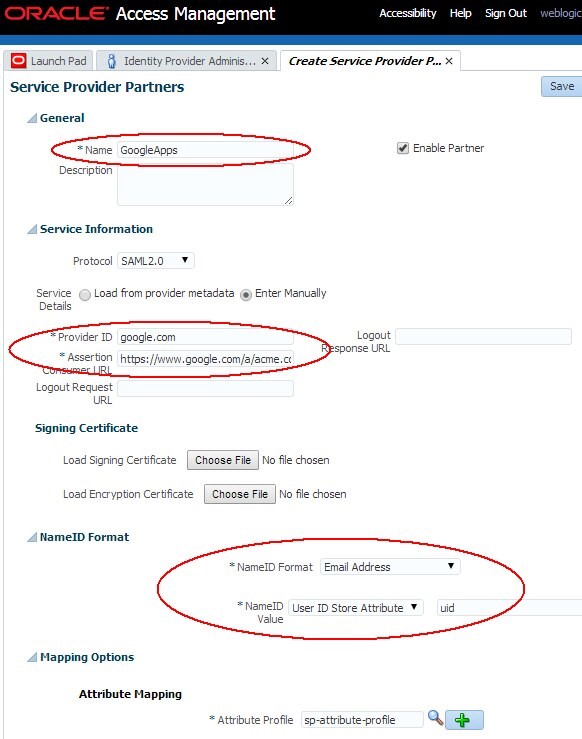
Description of the illustration Google_Apps.jpg
Collecting OAM Information
The following information needs to be provided into the Google Apps SSO Admin console:
-
SAML 2.0 SSO IdP endpoint
-
X.509 Signing Certificate used by the IdP to sign the SAML 2.0 Assertion
In earlier article, we listed the endpoints published by OAM. The SAML 2.0 SSO IdP endpoint and the SAML 2.0 logout endpoint would be http(s)://oampublic-hostname:oam-public-port/oamfed /idp/samlv20, with oam-public-hostname and oampublic-port being the values of the public endpoint, where the user accesses the OAM application (load balancer, HTTP reverse proxy…).
If you are unsure about the oam-public-hostname and oam-public-port, you can:
-
Go to the OAM Administration Console:
http(s)://oam-admin-host:oam-adminport/oamconsole -
Navigate to Configuration , Access Manager Settings
-
The
oam-public-hostnameis the OAM Server Host, theoam-public-portis the OAM Server Port and the protocol (http or https) is listed in OAM Server Protocol.
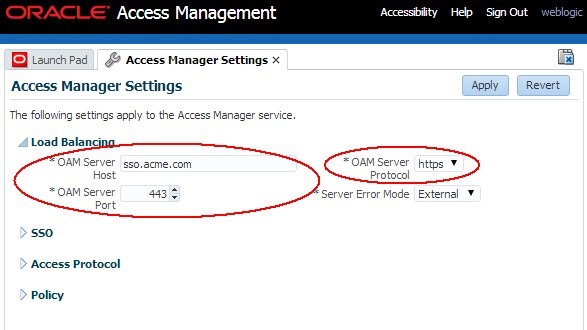
Description of the illustration Access_Manager_Settings.jpg
In the same article, we also explained how to determine which key entry is used to sign SAML messages and how to retrieve the corresponding Signing Certificate used by IdP:
-
Go to the OAM Administration Console:
http(s)://oam-admin-host:oam-adminport/oamconsole -
Navigate to Configuration , Federation Settings
-
The Signing Key field in the General section indicates which key ID entry is used for SAML message signature operations
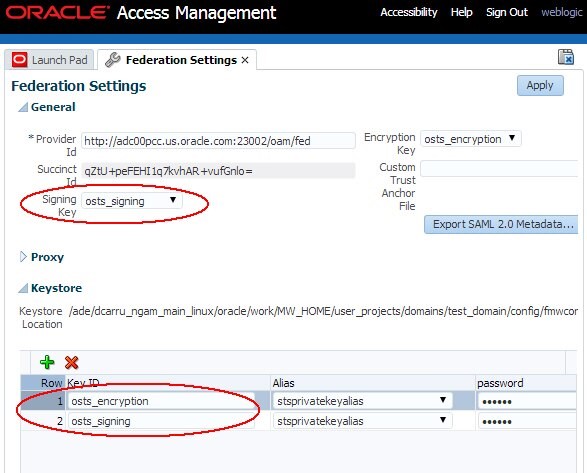
Description of the illustration Federation_Settings.jpg
To retrieve the certificate file of a specific key ID, open a browser and use the following URL to retrieve the certificate and save it locally:
http://oam-runtime-host:oam-runtime-port/oamfed /idp/cert?id=<KEYENTRY_ID>
-
The id query parameter contains the key entry ID for the certificate. Replace
<KEYENTRY_ID>- An example is:
http://acme.com/oamfed/idp/cert?id=osts_signing
- An example is:
Google Apps Configuration
To configure Google Apps for SAML 2.0 SSO flow, perform the following steps:
-
Launch a browser
-
Go to
https://www.google.com/enterprise/apps/business/ -
Authenticate and go to the Admin Dashboard
-
Click on More Controls
- Click Security
- Click Advanced Settings
- Click Set up single sign-on (SSO)
Description of the illustration More_Controls.jpg

Description of the illustration Security_Screen.jpg
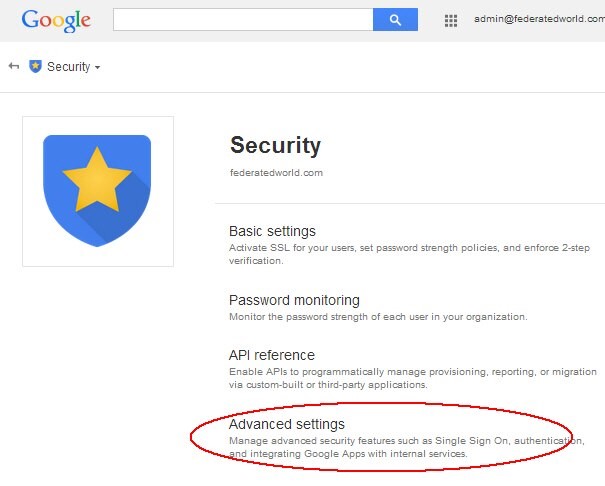
Description of the illustration Advanced_Settings.jpg
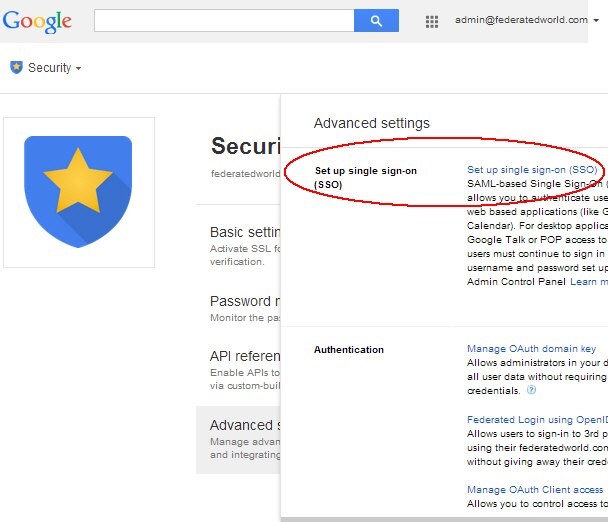
Description of the illustration SSO_Screen.jpg
In the SSO Setup page, upload the certificate:
-
In the Verification Certificate section, click Choose file
-
Select the OAM IdP certificate saved earlier
-
Click upload
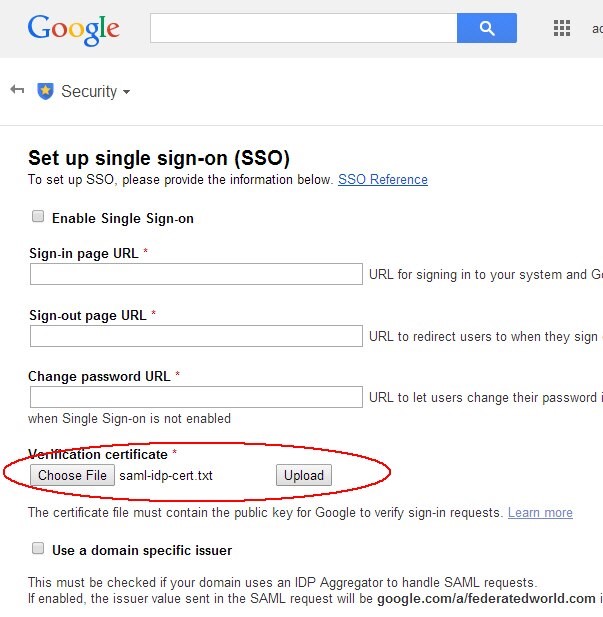
Description of the illustration Upload_certificate.jpg
In the SSO Setup page, to set up the URLs and enable Federation SSO:
-
Enter the Sign-in URL (IdP SAML 2.0 SSO endpoint), similar to
http(s)://oam-publichostname:oam-public-port/oamfed/idp/samlv20(for example:https://sso.acme.com/oamfed/idp/samlv20) -
Enter the Sign-out URL (IdP SAML 2.0 Logout endpoint), similar to
http(s)://oam-publichostname:oam-public-port/oamfed/idp/samlv20(for example:https://sso.acme.com/oamfed/idp/samlv20) -
Enter the Change Password URL for your deployment (note: In this example use
/changePassword, but this is not an OAM service; you need to enter the Password Management service URL for your deployment) -
Check the Enable Single Sign-On to turn on Federation SSO
-
Click Save
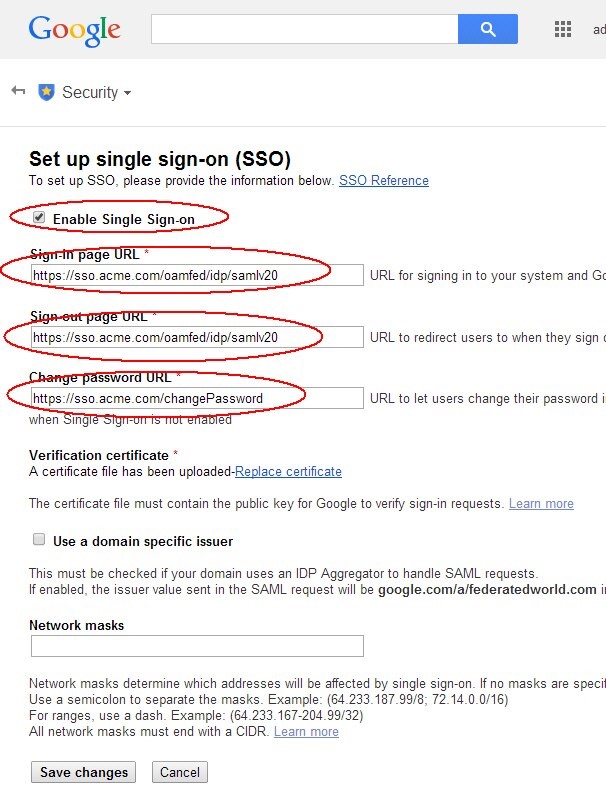
Description of the illustration Enable_SSO.jpg
Testing
To test:
-
Open a fresh browser
-
Go to these URLs to authenticate via Federation SSO for the following Google Apps:
-
Gmail:
https://mail.google.com /a/\<YOUR_DOMAIN.COM\>/(for examplehttps://mail.google.com/a/acme.com/) -
Calendar:
https://calendar.google.com /a/\<YOUR_DOMAIN.COM\>/(for examplehttps://calendar.google.com/a/acme.com/) -
Documents:
https://docs.google.com /a/\<YOUR_DOMAIN.COM\>/(for examplehttps://docs.google.com/a/acme.com/) -
Enter the Gmail URL for example
You will be redirected to OAM IdP
- Enter your credentials
- Click Login
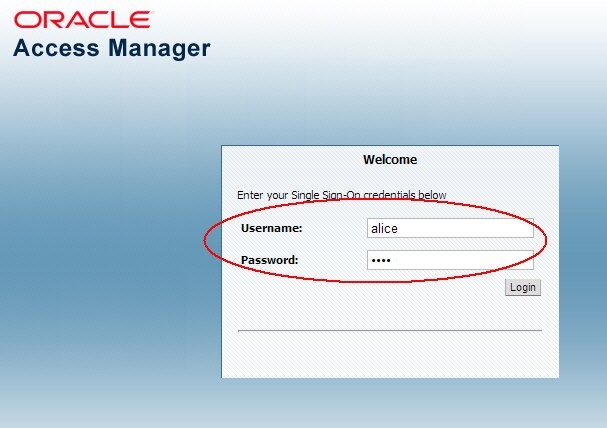
Description of the illustration Access_Manager.jpg
The Gmail application is displayed:
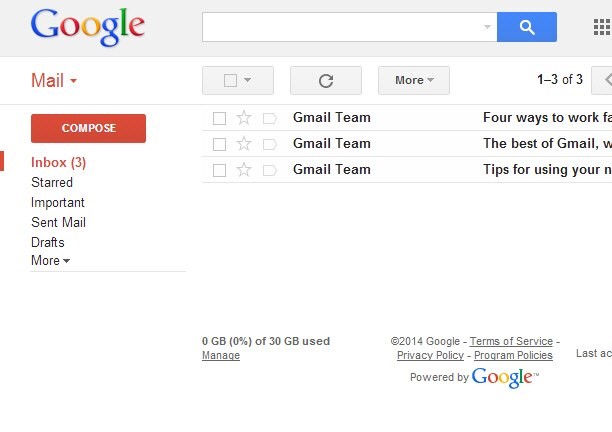
Description of the illustration Gmail_Login.jpg
[Description of the illustration Gmail_Login.jpg](files/Gmail_Login.txt)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Integrating Google Apps with OAM and IdP
F60935-01
September 2022
Copyright © 2022, Oracle and/or its affiliates.