Integrating Office 365 with OAM and IdP
This is a continuation of the article where we configured OAM (11.1.2.2.0 or later) as an IdP with Office 365 for Federation SSO using the SAML 2.0 protocol.
Be sure to have read the article about pre-requisites.
The integration covers:
-
Browser Federation SSO integration: This is the flow the user exercises when accessing the
www.office365.comresources via a browser -
The
www.office365.comprompts the user to enter email address -
The server detects that Federation SSO should be used for that domain and starts a Federation SSO flow the IdP
-
IdP challenges the user, create a SAML Assertion and redirect the user to
www.office365.com -
www.office365.comgrants access to the user -
ActiveSync mail integration: In this flow, the user uses a mail application configured for Office 365
-
When the mail application is started, it sends the user’s credentials (email address and IdP password) to Office 365.
www.office365.commakes a direct connection over SSL to the IdP and uses the SAML 2.0 ECP protocol to send a SAML AuthnRequest and the user’s credentials via HTTP Basic Authentication -
The IdP validates those credentials and return a SAML Assertion via the ECP protocol
-
Office 365 grants access to the mail application
It is important to note that integration with Office 365 for non SAML 2.0 components will not work, such as:
-
Lync clients
-
OWA Mobile Apps
This article is based on:
-
The testing performed from Oracle team
-
The Microsoft article regarding SAML 2.0 support for Office 365 and more specifically the technical document listing steps required to configure Office 365 (user management and Federation trust establishment)
-
Microsoft Blog
-
Technical document describing how to configure Office 365
Testing Environment
For this test integration, use the following approach:
-
User alice at OAM:
-
Username (uid attribute): alice.appleton
-
Email address (mail attribute): alice.appleton@acme.com
-
First name (givenname attribute): Alice
-
Last name (sn attribute): Appleton
-
-
User alice at Office 365 (see the Microsoft technical document on more information on how to create a user in Azure AD):
-
UserPrincipalName: alice.appleton@acme.com
-
ImmutableId: alice.appleton
-
DisplayName: Alice Appleton
-
FirstName: Alice
-
LastName: Appleton
-
UsageLocation: US
-
-
Federation agreement:
-
SAML 2.0 NameID format:
urn:oasis:names:tc:SAML:2.0:nameid-format:persistent -
LDAP attribute used to populate SAML 2.0
NameIDvalue:uid(because theNameIDmust match theImmutableId)
-
-
SAML Attribute contained in the SAML Assertion
-
Name: IDPEmail
-
LDAP Attribute used to populate this attribute value: mail (because the attribute value must match the
UserPrincipalName)
-
-
Office 365 specifics:
-
The domain name will be
acme.com -
The protocol used will be SAMLP
-
ActiveSync mail application will be supported OAM Configuration
-
Setting up Office 365 as an SP in IdP consists of:
-
Creating an SP Attribute Profile in order to send the
IDPEmailattribute containing the mail attribute -
Creating an SP partner for Office 365 and bind it to the new SP Attribute Profile
-
Updating the Office 365 SP Partner configuration for
-
SHA-1 hashing algorithm in signatures
-
Inclusion of OAM’s signing certificate in outgoing SAML messages
-
HTTP Basic Auth for ActiveSync mail integration
Office 365 Configuration
Please refer to the following Microsoft information when reading this section:
-
Microsoft Blog
-
Technical document describing how to configure Office 365
Windows Powershell
Ensure that the Windows Powershell tools are installed on the computer from which you will connect to Office 365 for administration purposes.
Provisioning IdP as a Partner in Office 365
Top create OAM as an IdP partner for the acme.com domain in Office 365, perform the following steps:
-
Connect to Office 365 as the administrator for acme.com
-
Connect-MsolService
-
Set the following environment variables (the data used is the one retrieved from the pre-requisites section; note that the string for
$idpSigningCertis on the same line as the$idpSigningCert =, and that it is a single line): -
$domainName= “acme.com” -
$BrandName- “ACME IdP” -
$browserSSOLoginURL= “https://acme.com/oamfed/idp/samlv20 -
$ecpSSOURL= “https://acme.com/oamfed/idp/soap” -
$logoutURL= “https://acme.com/oamfed/idp/samlv20 -
$issuerProviderID= “https://acme.com/oam/fed” -
$idpSigningCert= “MIIB+DCCAWGgAwIBAgIBCjANB……oInVUbGTBDMfqmW5iZ/wjpzItg==” $ssoProtocol = “SAMLP” -
Execute the following command using the above variables:
Set-MsolDomainAuthentication -DomainName $domainName-FederationBrandName $BrandName -Authentication Federated -PassiveLogOnUri$browserSSOLoginURL -ActiveLogOnUri $ecpSSOURL -SigningCertificate$idpSigningCert -IssuerUri $issuerProviderID -LogOffUri $logoutURL-PreferredAuthenticationProtocol $ssoProtocol
OAM Configuration
SP Attribute Profile
To create a new SP Attribute Profile that will be set up to send the SAML IDPEmail Attribute containing the user’s UPN value, perform the following operations:
-
Go to the OAM Administration Console:
http(s)://oam-admin-host:oam-admin port/oamconsole. -
Navigate to Identity Federation, Identity Provider Administration.
-
Click on the Service Provider Attribute Profiles tab.
-
Click on the Create SP Attribute Profile button.
-
Enter a name for the new profile (for example
Office365-attr-profile). -
In the Attribute Mapping section, click Add.
-
Enter the following information:
-
Message Attribute Name:
IDPEmail -
Value: enter the LDAP user attribute containing the user’s UPN in the directory used by OAM (in this example: user, attr, mail)
-
Always send: checked
-
-
Click OK.
- Click Save.
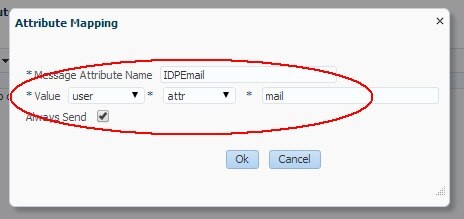
Description of the illustration Attribute_Mapping.jpg
The Attribute Profile will be shown:
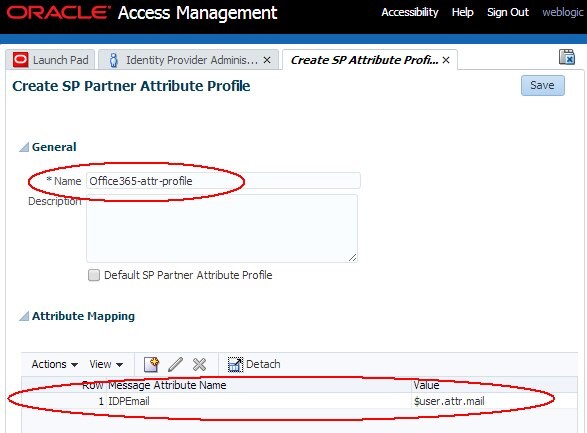
Description of the illustration Attribute_Profile.jpg
Office 365 SP Partner
To add Office 365 as an SP partner in OAM, perform the following steps:
-
Go to the OAM Administration Console:
http(s)://oam-admin-host:oam-admin port/oamconsole -
Navigate to Identity Federation, Identity Provider Administration
-
Click on the Create Service Provider Partner button
-
In the Create screen:
-
Enter a name for the partner (for example Office365)
-
Select SAML 2.0 as the Protocol
-
Click Load Metadata and upload the SAML 2.0 Metadata =le for the Office 365
-
Select Persistent as the
NameIDformat -
Enter the LDAP user attribute that contains the user’s
ImmutableIdvalue (in this example,uid) -
Select the SP Attribute Profile that was previously created (in this example
Office365-attr-profile)
-
-
Click Save
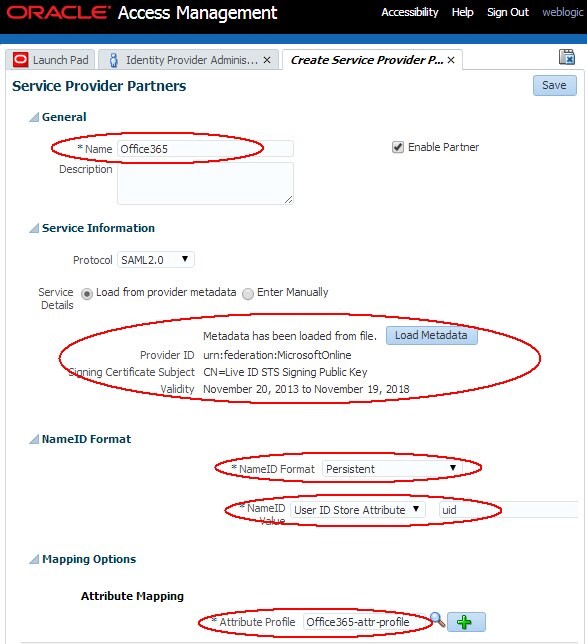
Description of the illustration Service_Provider_Partner.jpg
SHA-1 Hash Algorithm for Digital Signature
To configure OAM to use SHA-1 for signatures for the Office 365 SP partner, perform the following steps:
-
Enter the WLST environment by executing:
$IAM_ORACLE_HOME/common/bin/wlst.sh -
Connect to the WLS Admin server:
connect() -
Navigate to the Domain Runtime branch:
domainRuntime() -
Execute the
configureFedDigitalSignature()command: -
Replace
PARTNER_NAMEwith the name of the added partner- An example is:
configureFedDigitalSignature(partner="Office365", partnerType="sp”, algorithm="SHA-1")
- An example is:
-
Exit the WLST environment:
exit()
configureFedDigitalSignature(partner="PARTNER_NAME", partnerType="sp",algorithm="SHA-256/SHA-1")
OAM’s Signing Certificate in XML Digital Signature
To configure OAM so that the Federation server includes its X.509 signing certificate in all outgoing signed SAML messages for the Office 365 SP partner, perform the following steps:
-
Enter the WLST environment by executing:
$IAM_ORACLE_HOME/common/bin/wlst.sh -
Connect to the WLS Admin server:
connect() -
Navigate to the Domain Runtime branch:
domainRuntime() -
Execute the
updatePartnerProperty()command:updatePartnerProperty("PARTNER_NAME", "sp", "includecertinsignature", "true""boolean") -
Replace PARTNER_NAME with the name of the added partner An example is:
- Exit the WLST environment:
exit()
updatePartnerProperty("Office365", "sp", "includecertinsignature", "true", "boolean")
HTTP Basic Auth for ActiveSync Mail Integration
In the SAML 2.0 ECP flow, the Office 365 server makes a direct connection to IdP over SOAP over HTTPS and posts a SAML AuthnRequest message. Alongside the SOAP request, the HTTP request contains the user’s credentials as part of the HTTP Basic Authentication headers.
IdP must be configured to use an OAM HTTP Basic Authentication scheme to validate those credentials. Also this operation must not result in an OAM session to be created, since this is rather a credential validation operation initiated by the Office 365 server, and not the user involved with OAM. For those reasons, IdP must be configured to use a scheme based on:
-
BASIC mode
-
With the challenge parameters containing the
CookieLessMode=trueentry
The BasicSessionlessScheme can be used for this flow.
Also, OAM must be configured to send urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport as a SAML 2.0 Authentication Method when the client is authenticated via the BasicSessionlessScheme.
To configure OAM to use HTTP Basic Authentication in the SAML 2.0 ECP flow, perform the following steps:
-
Enter the WLST environment by executing:
$IAM_ORACLE_HOME/common/bin/wlst.sh -
Connect to the WLS Admin server:
connect() -
Navigate to the Domain Runtime branch:
domainRuntime() -
Execute the
setSPPartnerAlternateScheme()command to instruct OAM to useBasicSessionlessScheme:setSPPartnerAlternateScheme(PARTNER_NAME, "true", httpHeaderName="X-MSClient-Application", httpHeaderExpression=".\*Microsoft.Exchange..\*" authnScheme="BasicSessionlessScheme") -
Replace PARTNER_NAME with the name of the added partner
- Retrieve the OAM Fed partner profile used by the Office 365 SP partner in OAM:
- Replace
PARTNER_NAMEwith the name of the added partner -
Execute the
addSPPartnerProfileAuthnMethod()command to instruct OAM to send “urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport” as the SAML 2.0 Authentication Method when the client is authenticated viaBasicSessionlessScheme:addSPPartnerProfileAuthnMethod(PARTNER_PROFILE,"urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport","BasicSessionlessScheme") -
Replace PARTNER_PROFILE with the value retrieved in the earlier step
- Exit the WLST environment:
exit()
An example is: setSPPartnerAlternateScheme("Office365", "true", httpHeaderName="X-MS-Client-Application", httpHeaderExpression=".\*Microsoft.Exchange..\*" authnScheme="BasicSessionlessScheme")
getFedPartnerProfile(PARTNER_NAME "sp")
An example is: getFedPartnerProfile("Office365", "sp") Write down the returned value
An example is: addSPPartnerProfileAuthnMethod("saml20-sp-partner-profile", "urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport", "BasicSessionlessScheme")
Testing
Browser SSO
To test the Browser SSO flows:
-
Open a browser
-
Go to
http://office365.com -
Click Sign In
-
Enter the user’s email address
- Click Next
-
At IdP enter username/password (depending on the Authentication scheme used to authenticate Federated users,
LDAPSchemein this example) -
Click Login
Description of the illustration Signin_Page.jpg
Office 365 attempts to locate your Office 365 domain based on the suffix of the email address
Once the domain has been located, Office 365 triggers a Federation SSO flow to redirect you to OAM / IdP for authentication
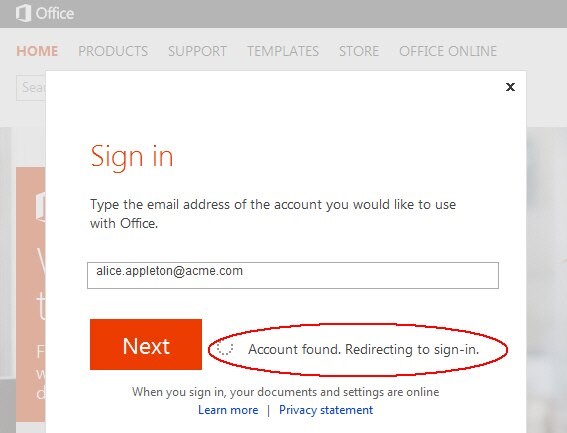
Description of the illustration Account_Found_Page.jpg
[Description of the illustration Account_Found_Page.jpg](files/Account_Found_Page.txt)
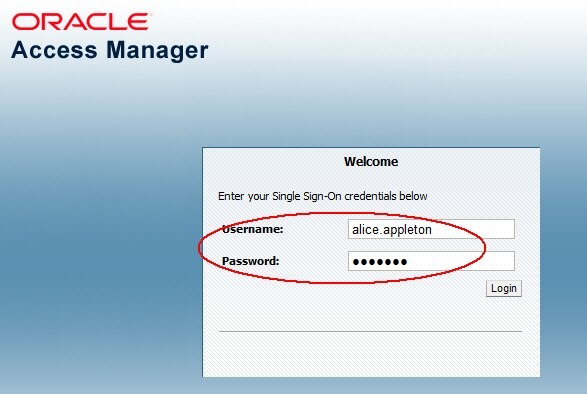
Description of the illustration Access_Manager_Screen.jpg
IdP validates the credentials, create a SAML 2.0 Assertion and redirects the user back to Office 365 where the user is granted access:
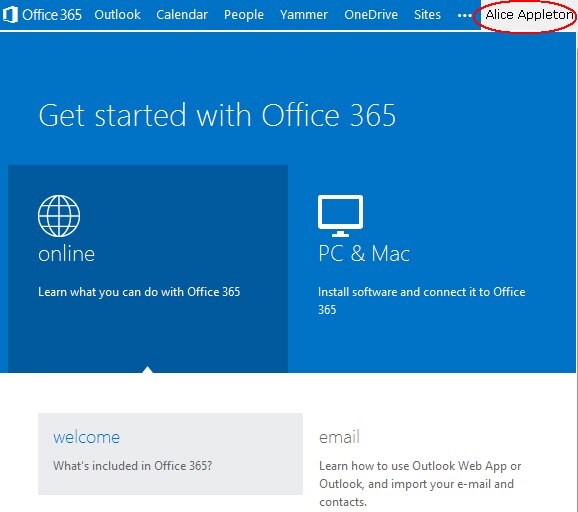
Description of the illustration Office_Screen.jpg
A sample SAML 2.0 Assertion sent by OAM / IdP to Office 365 looks like:
<samlp:Response ... Destination="https://login.microsoftonline.com/login.srf" ID="ideBpq-cnpGfrWXMpBIjxN7QPQKa6WTVtnuZZr0Qe" InResponseTo="_d111d2a7-3475-4bc2-928f-34b83a4a0f64"IssueInstant="2014-01-18T16:58:05Z" Version="2.0"> <saml:Issuer Format="urn:oasis:names:tc:SAML:2.0:nameidformat:entity">https://acme.com/oam/fed</saml:Issuer <samlp:Status><samlp:StatusCodeValue="urn:oasis:names:tc:SAML:2.0:status:Success"/></samlp:Status>
<saml:Assertion ID="id-nTZcRuTaECKj2X9wzUTn7e-CknyECbGljTSo1T70"
IssueInstant="2014-01-18T16:58:05Z" Version="2.0"> <saml:Issuer Format="urn:oasis:names:tc:SAML:2.0:nameidformat:entity">https://acme.com/oam/fed</saml:Issuer
<dsig:Signature>
<dsig:SignedInfo>
<dsig:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-ex c14n#"/>
<dsig:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rs sha1"/>
<dsig:Reference URI="#id-nTZcRuTaECKj2X9wzUTn7e-CknyECbGljTSo1T70">
<dsig:Transforms>
<dsig:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#envelope signature"/>
<dsig:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
</dsig:Transforms>
<dsig:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"
<dsig:DigestValue>6iKaxdO74Xi5eRnv0X7nsmN/y10=</dsig:DigestValue>
</dsig:Reference>
</dsig:SignedInfo>
<dsig:SignatureValue>WYCBhIgPLafDeXroMSME80/QM...K/sNsI=
</dsig:SignatureValue>
<dsig:KeyInfo>
<dsig:X509Data>
<dsig:X509Certi=cate>MIIB+DCCAWGgA...plaoMZLcRoInVUbGTBDMfqmW5iZ/wjpzItg==
</dsig:X509Certi=cate>
</dsig:X509Data>
</dsig:KeyInfo>
</dsig:Signature>
<saml:Subject>
<saml:NameID Format="urn:oasis:names:tc:SAML:2.0:nameid-format:persistent"NameQuali=er="https://acme.com/oam/fed"SPNameQuali=er="urn:federation:MicrosoftOnline">alice.appleton</saml:NameID>
<saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
<saml:SubjectConfirmationData InResponseTo="_d111d2a7-3475-4bc2-928f-
34b83a4a0f64" NotOnOrAfter="2014-01-18T17:03:05Z"
Recipient="https://login.microsoftonline.com/login.srf"/></saml:SubjectCon=rmatio
</saml:Subject>
<saml:Conditions NotBefore="2014-01-18T16:58:05Z"
NotOnOrAfter="2014-01-18T17:03:05Z">
<saml:AudienceRestriction>
<saml:Audience>urn:federation:MicrosoftOnline</saml:Audience>
</saml:AudienceRestriction>
</saml:Conditions>
<saml:AuthnStatement AuthnInstant="2014-01-18T16:58:05Z" SessionIndex="id-IMSvfoQa8uVVtSmN-lrdOfgEVKFJHF8AhmIDzj-"
SessionNotOnOrAfter="2014-01-18T17:58:05Z">
<saml:AuthnContext>
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnCon </saml:AuthnContext>
</saml:AuthnStatement>
<saml:AttributeStatement>
<saml:Attribute Name="IDPEmail"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"> <saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema xsi:type="xs:string">alice.appleton@acme.com</saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>
</saml:Assertion>
</samlp:Response>
ActiveSync Mail Application
For this test, add an Exchange email account on an iPhone. During the setup, the iPhone mail application sends the email address and password to Office 365 mail server, which extracts the user identifier from the email address and perform the SAML 2.0 ECP protocol with HTTP Basic Authentication.
Note: A similar flow is exercised if the setup involved an Outlook Desktop application instead of the iPhone mail native application.
Perform the following steps to set up the iPhone with Office 365:
-
Go to Settings
-
Go to Mail
-
Add Account
-
Select Exchange
-
Enter the email address (alice.appleton@acme.com in this example)
-
Password at OAM for the user (password for alice.appleton user; remember that the identifier will be used as the HTTP Basic Authentication username, alice.appleton in this example)
- Click Next
- After showing the successful validation, the iPhone displays a screen allowing the user to select which feature to enable. After selecting the features, save. The account is set up now.

Description of the illustration Add_Account.jpg
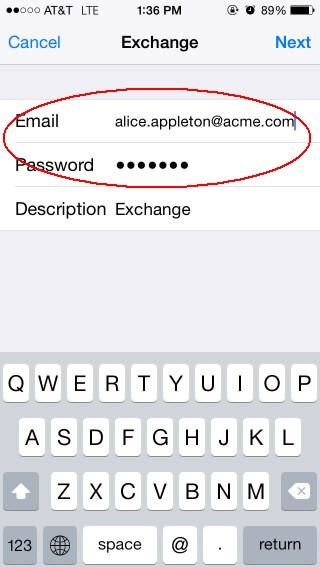
Description of the illustration Exchange_Screen.jpg
The mail application sends the user account information to Office 365 mail server Office 365 mail server interacts with OAM / IdP via the SAML 2.0 ECP protocol to validate the data, with the user identifier and password sent via HTTP Basic Authentication to OAM / IdP
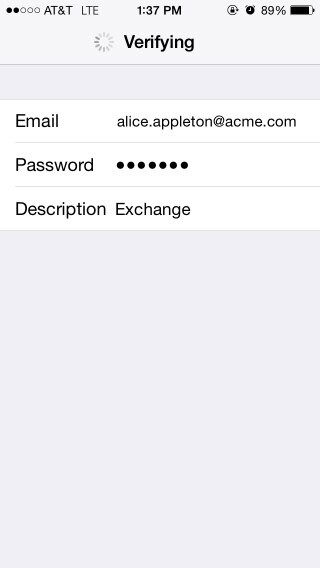
Description of the illustration Verifying_Screen.jpg
Upon successful validation, the iPhone shows:
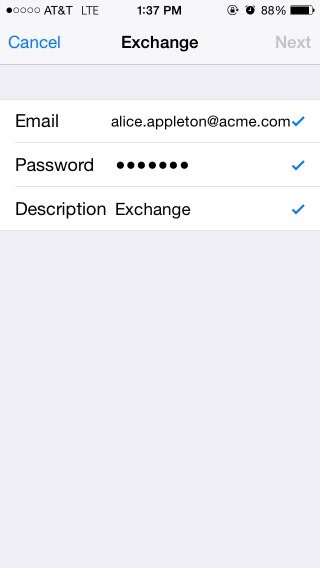
Description of the illustration iphone_Screen.jpg
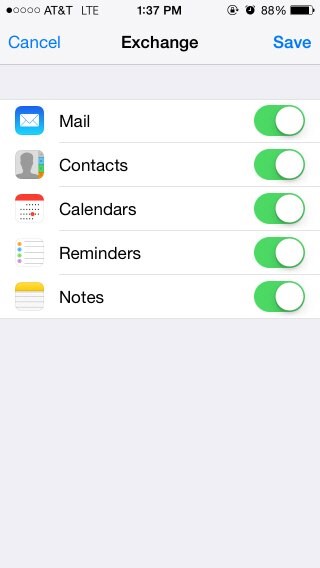
Description of the illustration Account_Setup.jpg
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Integrating Office 365 with OAM and IdP
F60938-01
September 2022
Copyright © 2022, Oracle and/or its affiliates.