SAML Authentication
Security Assertions Markup Language (SAML) associates a principal with additional identity information that can be used to determine the principal's access rights within a specific domain.
SAML is a standard that provides a means for exchanging security information across security domains. In a typical exchange between SAML messages between two domains, one party acts as a relying party while the other acts as an asserting party. The asserting party asserts information, such as whether a user has been authenticated, authorized to perform a certain action, and so forth. The relying party uses information provided by the asserting party to make security-related decisions (for example, what types of access to a specific resource the user should be granted).
When a user signs into a SAML-compliant service of a relying party, the service sends a "request for authentication assertion" to the issuing authority. The issuing authority returns an "authentication assertion" reference stating that the user was authenticated by a particular method at a specific time. The service then passes this assertion reference to other relying parties to validate the user's credentials. When the user accesses another SAML-compliant site that requires authentication, that site uses the reference to request the "authentication assertion" from the issuing authority, which states that the user has already been authenticated. At the issuing authority, an assertion layer handles request and response messages using SAML, which can bind to various communication and transport protocols (for example, HTTP, SOAP, and so on).
While the user who requests an assertion always consumes assertions, the issuing authority can act as producer and consumer since it can both create and validate assertions.
Identity Federation
Federated identity is the mapping of user credentials across security domains (identity providers and service providers) to allow access to hosted computing resources and services. In a federated environment, businesses that utilize federated identity can obtain identity information about an individual or other entity from the user's home organization or security domain. This provides twin benefits:
- End users do not need to enter login information to access each entity, or site, where business is conducted. This eliminates the need for users to remember and manage multiple passwords. Users will still need accounts for each site so that the accounts can be mapped.
- Enterprises do not need to create additional accounts to manage the identities of users who are already known to a partner organization.
Logging in to an Application that Utilizes Identity Federation with SAML authentication
The following diagram provides a general overview of the processes that occur when a user attempts to log in to a Primavera application after SAML authentication and identity federation has been successfully configured using Oracle Access Manager.
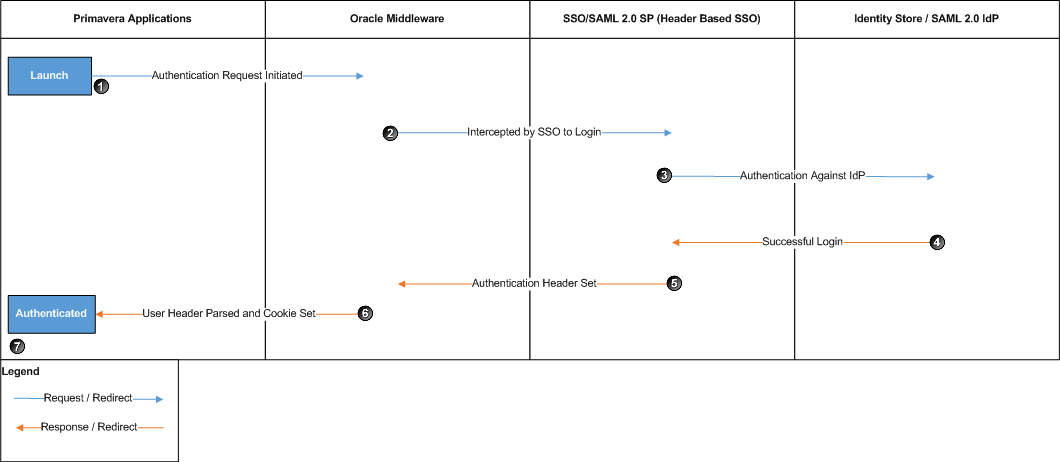
When a user attempts to log in to a Primavera application instance that requires SAML authentication, the following processes occur:
- The Primavera application sends an authentication request.
- The authentication request is intercepted by SSO in an embedded browser in which a user is required to enter their login information.
- The user is authenticated against the identity provider (IdP).
- After the user is authenticated, the IdP redirects the SAML assertion to the Service Provider (SP).
- The SP parses the SAML assertion and sets the authentication header.
- WebLogic reads the header and sets the authentication cookie. The Primavera application reads the cookie and establishes a session.
- The user is logged in to the application.
Note: SAML authentication is not supported for P6 Professional when using Primavera Virtual Desktop.