Understanding PeopleSoft Integration Broker Security Processing
This section discusses:
Outbound PeopleSoft Integration Broker security processing.
Inbound PeopleSoft Integration Broker security processing.
This section discusses security processing for outbound integrations from PeopleSoft Integration Broker.
Image: Outbound PeopleSoft Integration Broker Security Processing
This diagram illustrates security processing for outbound integrations from PeopleSoft Integration Broker. The diagram shows that as an outbound service operation passes onto the application server, it goes through user authentication and nonrepudiation (if implemented) on the integration engine. As processing moves to the web server, the service operation may go through client authentication (if implemented) and WS-security processing (if implemented). The last type of security processing through which a service operation may go is through on the PeopleSoft side is SSL/TLS encryption (if implemented) on the web server.
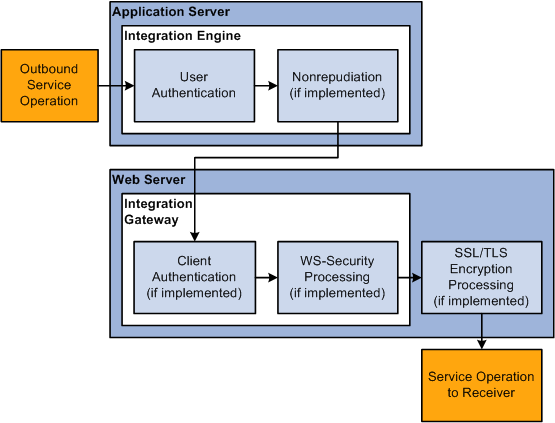
PeopleSoft Integration Broker applies the following security elements to outbound integrations:
Note: The elements are discussed in the order in which the system applies them.
|
Field or Control |
Definition |
|---|---|
| User authentication |
If the outbound service operation originates from a PeopleSoft (PIA) node, the user authentication process attaches the PeopleSoft authentication token to the service operation. If the service operation originates from an external (External) node, the model determines the user ID for the service operation and passes the information to the WS-Security framework so it can generate the UsernameToken for the outbound transaction. |
| Nonrepudiation |
Nonrepudiation processing is performed. |
| Client authentication |
Client authentication secures the connection between the PeopleSoft application server and the integration gateway on outbound transactions. You use digital certificates to secure this connection. |
| WS-Security |
Outbound WS-Security processing includes generating the UsernameToken for the WS-Security SOAP header. This process may also involve encrypting and digitally signing the data, if specified in the WS-Security parameters on the node. |
| SSL/TLS encryption |
SSL/TLS encryption on outbound integrations establishes a secure web server connection with an integration partner. |
This section discusses inbound integration broker security processing.
Image: Inbound PeopleSoft Integration Broker Security Processing
This diagram illustrates security processing for inbound integrations to PeopleSoft Integration Broker. The first type of security processing that may be performed on an inbound service operation occurs on the web server where SSL/TLS encryption processing takes place if it is implemented. As service operation processing moves to the integration gateway located on the web server, it may go through WS-security processing (if implemented). As processing moves to the application server, an inbound service operation my go through nonrepudiation processing (if implemented), then user authentication. After user authentication, node authentication (if implemented) occurs. The final security processing before service invocation is permission list validation.
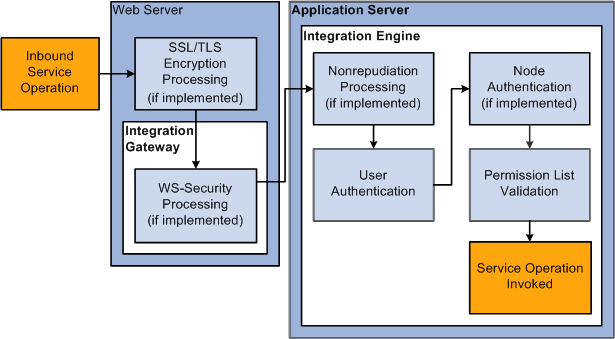
PeopleSoft Integration Broker applies the following security elements to inbound integrations:
Note: The elements are discussed in the order in which the system applies them.
|
Field or Control |
Definition |
|---|---|
| SSL/TLS encryption |
If the inbound service operation is encrypted, the integration gateway decrypts the data. |
| WS-Security |
On inbound transactions, WS-Security processing includes validating a digital signature (if required), decrypting user information (if required), and passing the extracted user information to the integration engine for authentication. |
| Nonrepudiation |
Nonrepudiation processing is performed. |
| User authentication |
The system determines and validates the user ID associated with the inbound service operation. |
| Node authentication |
If a node password is employed, the system validates that the inbound service operation contains the node password. If certificate authentication is employed, the system authenticates the node certificate. |
| Permission list validation |
The system matches the user ID passed in with the service operation to the appropriate permission list. |