Implementing Nonrepudiation
This section provides and overview of nonrepudiation and discusses how to configure nonrepudiation.
PeopleSoft Integration Broker applies nonrepudiation to cross-node messaging by digitally signing service operation requests and their responses.
Nonrepudiation Processing Overview
In PeopleSoft applications, nonrepudiation provides two-way protection; both the request and its response are nonrepudiated. PeopleSoft Integration Broker uses PKI technology to implement nonrepudiation for integrations. Each participating node’s keystore contains its own private key and the public keys of the nodes with which it exchanges nonrepudiation service operations.
Nonrepudiation works in the following manner:
Node A generates a number, known as a digest, which uniquely identifies its service operation request.
Node A uses its private key to generate a signature based on the digest, and inserts the signature into the nonrepudiation service operation request.
Node A sends the nonrepudiation request to Node B.
When it receives the nonrepudiation request, Node B uses Node A’s public key in its keystore to confirm the integrity of the digest.
It then separately recreates the digest from the service operation, and compares it to the received digest to confirm the integrity of the service operation.
Node B generates a digest that uniquely identifies its response.
Node B uses its private key to generate a signature based on the digest, and it inserts the signature into the nonrepudiation response to confirm receipt of the nonrepudiation request.
Node B sends the nonrepudiation response to Node A.
When the nonrepudiation response is received, Node A uses Node B’s public key in its keystore to confirm the integrity of the digest.
It then separately re-creates the digest from the service operation and compares it to the received digest to confirm the integrity of the service operation content.
Nonrepudiation produces the following results:
The sending node cannot repudiate that the service operation was sent, because the receiving node has a copy of the request signed by the sender.
The receiving node cannot repudiate that the service operation was received and processed, because the sending node has a copy of the response signed by the receiver.
The service operation integrity is verified, because the validated signature of each nonrepudiated service operation assures that the service operation content as received, exactly matches the content as sent.
Inbound Nonrepudiation Processing
This section discusses inbound nonrepudiation processing.
Nonrepudiation processing occurs on the application server in the integration engine.
Image: Inbound Nonrepudiation Processing
This diagram illustrates inbound nonrepudiation processing. The diagram shows all possible security processing for an inbound integration to show where in the processing flow nonrepudiation processing occurs. Nonrepudiation processing is highlighted in the foreground of the diagram.
The diagram illustrates the nonrepudiation processing steps on an inbound integration, including the validation that nonrepudiation is implemented, the validation of the nonrepudiation digest.
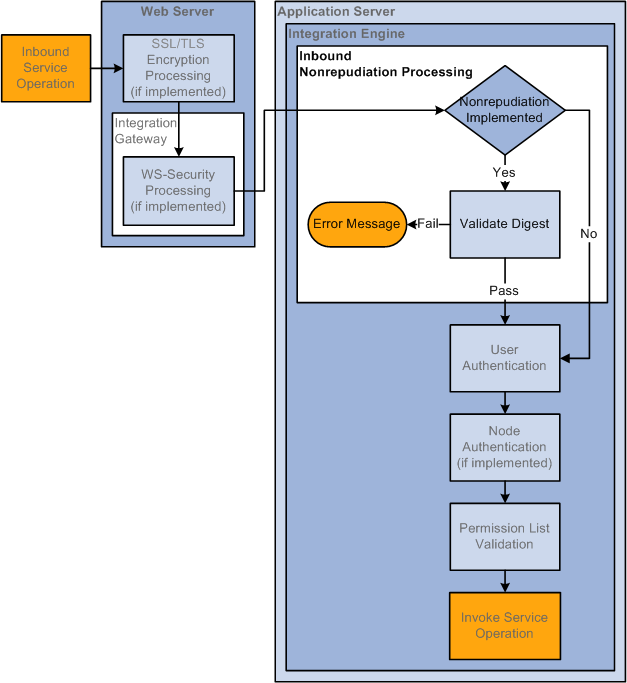
In inbound nonrepudiation processing, the system uses the integration partner's public key to validate the digest attached to the inbound service operation. It then uses its private key to recreate the digest on the service operation to validate the integrity of the service operation content.
If the system is able to validate the integrity of the digest and the service operation content, the service operation then goes through the user authentication process. If the system is unable to validate the digest or the service operation content, the transaction fails.
Outbound Nonrepudiation Processing
This section discusses outbound nonrepudiation processing.
Nonrepudiation processing occurs on the application server in the integration engine.
Image: Outbound Nonrepudiation Processing
This diagram illustrates outbound nonrepudiation processing. The diagram shows all possible security processing for an outbound integration to show where in the processing flow nonrepudiation processing occurs. Nonrepudiation processing is highlighted in the foreground of the diagram.
The diagram illustrates the nonrepudiation processing steps on an outbound integration, including the validation that nonrepudiation is implemented, the determination if the message is a request or response, and then the generation of the digest and signature for the request or response.
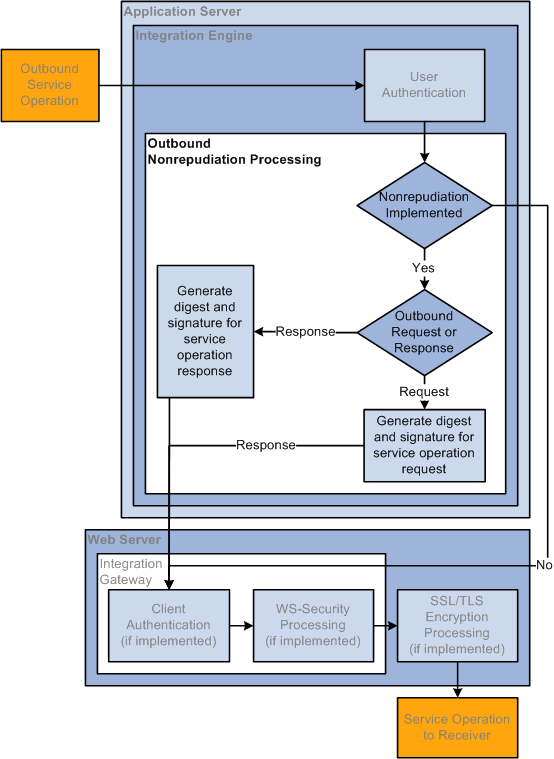
On outbound service operations, the system determines if the service operation is a request or a response.
When the service operation is a request, the system uses its private key to generate a digest and signature, and attaches those items to the request.
When the service operation is an outbound response, the system uses its private key to generate a signature and response and inserts them into the service operation.
You must install application server-based digital certificates on both sending and target systems to implement nonrepudiation.
See Installing Application Server-Based Digital Certificates.
This section discusses nonrepudiation configuration tasks on sending and target PeopleSoft systems using PeopleSoft Integration Broker.
If a participating node doesn’t use PeopleSoft Integration Broker, that node is still responsible for managing the appropriate private and public keys, inserting properly formatted signatures in the nonrepudiation service operation it sends, and properly handling signatures in the service operations that it receives.
With both archived and active nonrepudiation service operations, you can regenerate the digest in the Service Operations Monitor to reconfirm that it matches the attached digest.
See Viewing Nonrepudiation Signatures in XML Format.
Configuring Nonrepudiation on Sending PeopleSoft Systems
This section discusses configuring nonrepudiation on sending systems for asynchronous or synchronous transactions.
Prerequisites for configuring nonrepudiation are discussed elsewhere in this section.
See Prerequisites for Implementing Nonrepudiation.
To configure nonrepudiation for service operations on the source system you must:
Select the Non-Repudiation check box on the service operation that will be invoked.
Select the Non-Repudiation check box on the remote node definition that represents the target system.
Configuring Nonrepudiation on Target PeopleSoft Systems
You must supply the digital certificates containing the private and public keys required for nonrepudiation transactions.
No additional configuration is required on target PeopleSoft systems to handle nonrepudiated service operations. A nonrepudiated service operation received by a target PeopleSoft system will attempt to validate the service operation regardless if the local node and service operation are set for nonrepudiation.
Saving Nonrepudiated Service Operations
To save nonrepudiation service operations for future reference, you must archive them.