Working with Authentication and Authorization
Search Framework handles various security related tasks, including:
Authenticating users (development, administration, and end users).
Authenticating systems requesting access to service operations.
Authorizing end user search requests.
When managing search requests with Search Framework, it is important to distinguish between authentication and authorization.
Authentication determines if a user is a legitimate user, who can access the system. Authentication is configured using PeopleSoft user profiles, roles, and permission lists.
Authorization determines the access level for an authenticated user. Once a user is authenticated, the system invokes the authorization rules. You define authorization (access controls) per search definition on the Security tab. For some instances, applying No Security is a valid option. However, for other situations, you need to apply stricter control over what users can and cannot see. You can restrict access by the source (search definition) or by the document (search result).
Source-level security applies to all the documents in the data source. Setting source-level security is useful when you want to prevent global visibility of data source content. When defining a source-level security you specify the users and roles that can view the search results for that search definition. When a user searches the associated index, the system verifies the user’s access level prior to displaying any search results.
Document-level security restricts access to specific search results. The document-level authorization uses security attributes. The attributes are defined using PeopleSoft Query or Connected Query during design time and are used to evaluate access during runtime. While defining a search definition, some of the fields chosen for the query may not be used necessarily for searching, but mainly as security attributes. For example, Department ID or Business Unit are examples of attributes that users may not necessarily search on, but their values can be used in the authorization process to evaluate if a user can view search results for a specific Department ID or Business Unit.
If applying any level of security, you should define an application class for every search definition. The application class is responsible for fetching a list of runtime values based on the security attributes. You associate the application class with a search definition on the Security tab of the search definition.
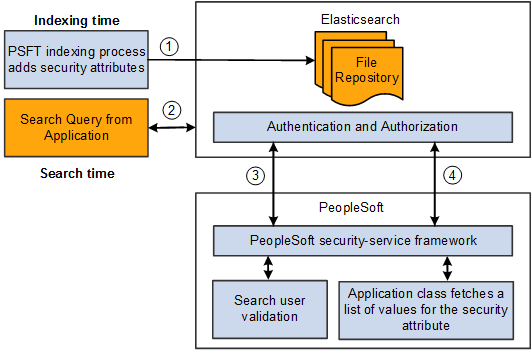
The following diagram illustrates the elements involved with authorization and authentication and the interaction between them.
Image: PeopleTools and Elasticsearch interacting to authenticate users and authorize user access to search results
This example illustrates how PeopleTools and Elasticsearch interact to authenticate users and authorize user access to search results.
|
Step |
Description |
|---|---|
|
1 |
During the index build, the crawler collects the defined security attributes and access restriction options associated with search definitions. The crawler applies those security attributes to the data sources (indexes). |
|
2 |
An application end user runs a search query. |
|
3 |
Elasticsearch security framework using the orcl-security-plugin invokes the PeopleSoft security service for user authentication. |
|
4 |
Based on the authenticated user, Elasticsearch performs either a source-level or a document-level authorization using the orcl-security-plugin. For document level authorization PeopleSoft invokes the Application class defined for the Data Source. This would fetch a list of values for the security attribute which then Elasticsearch would use for filtering the search results. |