Tracking User Sign In and Sign Out Activity
This topic describes tracking user sign in and sign out activity.
Understanding Abandoned Sessions and the PSACCESSLOG Table
PeopleSoft provides several queries to track user sign in and sign out activity. The information is stored in the PSACCESSLOG table.
The information captured in the PSACCESSLOG table does not account for abandoned PIA sessions.
An abandoned session can occur when:
A user’s PIA session times out.
A user puts a new URL in the current PIA page and navigates to another web site.
If a user does not sign out of the system properly, he or she appears as still signed into the system.
Tracking User Sign In/Sign Out Activity
Access the Access Log Queries page (select and click the Access Log Queries link on the Review Security Information page).
Image: Access Log Queries page
This example illustrates the fields and controls on the Access Log Queries page.
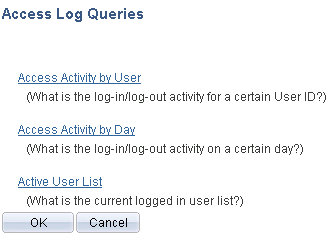
PeopleSoft Security provides three audit logs that track user sign in and sign out activity in PeopleSoft applications..
Select one of the following logs:
Access Activity by User
View a single user's sign in and sign out activity. This log includes the users' client IP addresses, sign in times, and sign out times.
Access Activity by Day
View one or more days of all user sign in and sign out activity. This log includes the users' IDs, client IP addresses, sign in times, and sign out times.
Active User List
View the users who are currently signed in to the application in the browser. This log includes users' IDs, client IP addresses, sign in times, and duration in minutes.
These logs are generated using data from the PSACCESSLOG table. If you are not interested monitoring access activity, you can delete the PSACCESSLOG table. Deleting this table has no negative effect.
Note: If you delete the PSACCESSLOG table and then decide that you would like to track user sign in and sign out activity, you must recreate the table using the same exact column names and order as were in the previous PSACCESSLOG table: OPRID, LOGIPADDRESS, LOGINDTTM, LOGOUTDTTM. Use Application Designer to open the PSACCESSLOG record definition and create the table.