Adding and Registering PS Process Monitor Targets
This section provides an overview and discusses:
Configuring PROCESSREQUEST Web Service.
Adding PS Process Monitor Targets From Discovery Results Page.
Adding PS Process Monitor Targets From the Process Monitor Setup Page.
PS Process Monitor Configuration Variables.
Working with custom SSL configurations.
Registering PS Process Monitor targets requires a few additional steps that need to be completed prior to the discovery process. Before you can discover and register a PS Process Monitor target, at least one PS PIA target needs to be discovered, and the PROCESSREQUEST web service must be published through the Integration Gateway.
You discover and register PS Process Monitor targets using:
Add PeopleSoft Targets: Discovery Results page.
Process Monitor Setup page.
Note: From PeopleTools version 8.56, the PROCESSREQUEST web service is part of PeopleTools database. Users need to execute the IB Template available in Automatic Configuration Templates. This will perform the IB configuration. Once the IB configuration is done, Users can proceed to discover the Process Monitor. On Process Monitor Discover page, click the Fetch WSDL button to fetch the wsdl from the PeopleTools Database. Users can proceed to discover process monitor after entering the User Name and Password,
Note: If the Process Monitor Discovery did not complete successfully, then verify if all the steps mentioned in Configuring PROCESSREQUEST Web Service is in place.
The following information assumes that you have a working knowledge of PeopleSoft Integration Broker and have it configured in your environment.
See the product documentation for PeopleTools: Integration Broker.
To configure the PROCESSREQUEST web service:
Configure Integration Broker for your environment.
Make sure to specify a Secure Target Location.
Note: The PROCESSREQUEST web service is enabled by default in PeopleTools 8.56 and PeopleSoft Applications built on PT8.58 and higher. Hence PeopleTools 8.56 and higher does not require you to perform the steps from 2 to 7.
Select , enter PROCESSREQUEST, and click Search.
Open each service operation and verify that Security Verification is set to one of the following:
Encrypt/Digital Sign or SSL
Encrypt or SSL
Digital Sign or SSL
SSL
Select open PROCESSREQUEST on the Select Services page, and click Next.
On the Select Service Operations page, select Use Secure Target Location, (to create a secure end point address in WSDL), select these service operations, and then click Next.
FindRequests
GetParams
GetProcessNames
GetPrompt
GetReport
GetRequest
GetServerConstraints
Note: GetServerConstraints service operation is included only for PeopleTools 8.54 version and above.
Schedule
UpdateRequest
Note: Version v1 must be set as the default for FindRequest, GetPrompt, and GetRequest service operation. You must include v1 for FindRequest, GetPrompt, and GetRequest service operation in the PROCESSREQUEST web service.
On the View WSDL page, click View WSDL to verify the generated WSDL, and click Next.
On the Specify Publishing page, click Finish, and copy the generated WSDL URL, which you will need when you discover and set up the PS Process Monitor target.
Configure the distribution agent.
Select PeopleTools, Process Scheduler, Report Nodes, select the Add a New Value tab, enter PRCSMNTRNODE, and click Add.
Select Ftp/XCopy.
Enter the URL as: http://<host>:port/psreports/<site>
Enter Network Path as: \\<host>\psreports
Click Save.
Configure server definition.
Select PeopleTools, Process Scheduler, Servers.
Select the appropriate server (PSNT, PSUNX, and so on).
Select the Distribution tab and enter Distribution Node Name as PRCSMNTRNODE.
Select the Transfer System Files to Report Repository check box.
Click Save.
Note: The replicate PIA may fail due to redundancy in classpath. For workaround, see E-PSEM: Oracle Enterprise Manager - Setup Process Monitor for Peoplesoft PIA (Doc ID 1620052.1).
During the typical discovery process, you have the option to add and register PS Process Monitor targets. The Add PS Process Monitor page can be launched only if a PS PIA target has been discovered and selected.
Note: For discovering PS Process Monitor targets, the PeopleTools version for the PS PIA target must be at least PeopleTools 8.50.
During PS Process Monitor discovery, the EM Agent communicates with Integration Broker over HTTPS using the default SSL configuration setup.
The following process outlines the typical Process Monitor discovery workflow, which existed in previous releases, and is supported by default in the current release, as well.
Image: Discover Process Monitor
Discover Process Monitor
Discover the PIA target.
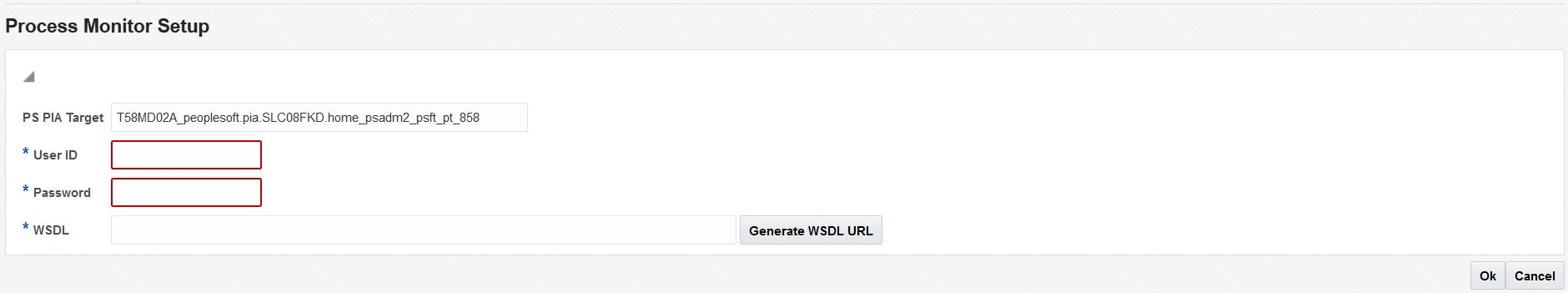
Use the PIA target in the All PeopleSoft Targets page, to discover the Process Monitor target.
In the Process Monitor discovery page, enter the WSDL URL or click the Generate WSDL URL button to fetch the WSDL url.
Discover the PS Process Monitor target.
This "typical" process:
uses the default SSL configuration.
makes no changes to the pskey.properties file.
keeps the property useCustomSSLConfiguration set to false (the default).
Additionally, the PeopleSoft plug-in supports EM Agent communicating with Integration Broker using a custom SSL configuration. The high-level steps for setting up the custom SSL configuration are:
Export the default signer certificate presented by the web server (WebLogic or WebSphere) for HTTPS communication (using the keytool utility).
Import this signer certificate into the keystore pskey used by the EM Agent using the keytool utility.
In pskey.properties file, enable the following property for the custom configuration setup:
useCustomSSLConfiguration=trueRestart the EM Agent and discover the Process Monitor target with the custom SSL configuration setup.
When using the custom SSL configuration, you import the signer certificate of the web server (WebLogic or WebSphere) into the agent’s custom keystore file which by default is: $AgentHome/sysman/config/pskey.
Note: The EM Agent’s keystore file (pskey) and properties file (pskey.properties) is required for implementing this feature and can be found in the directory $AgentHome/sysman/config.
Retrieving Signer Certificate from WebLogic
To retrieve the signer certificate:
Verify the signer certificate.
Go to the PIA signon URL using an HTTPS port.
Click View Certificates.
The certificate is displayed.
Click Export to export the certificate.
Save the certificate.
Export this signer certificate from the WebLogic keystore file, cacerts, using the keytool utility.
For example:
$Agent_Home/jdk/bin/keytool -export -rfc -keystore cacerts -alias certgencab -file certgencab.cer -storepass changeit -keypass changeitNote: If using a custom SSL configuration on WebLogic, you may need to export the appropriate signer certificate from the keystore, cacerts.
Import the signer certificate file certgencab.cer into the Agent’s custom keystore file, pskey, using the keytool utility.
For example:
$Agent_Home/jdk/bin/keytool -import -noprompt -trustcacerts -alias certgencab -file certgencab.cer -keystore pskey -storepass passwordEdit the pskey.properties file and ensure:
custom keystore location and other attributes are properly set.
useCustomSSLConfiguration is set to true.
Retrieving Signer Certificate from WebSphere
To retrieve the signer certificate from WebSphere:
Extract the signer certificate.
Login to WebSphere administration console, and navigate to Security, SSL certificate and key management, Key stores and certificates, NodeDefaultTrustStore, Signer certificates.
Select the default signer certificate, root, and click Extract.
This will extract the certificate into the given location in ASCII text mode by default.
Note: If you are using a custom SSL configuration on WebSphere, you may have to extract the appropriate signer certificate from the keystore, NodeDefaultTrustStore.
Import this signer certificate file, rootWAS.cer, into the Agent’s custom keystore file, pskey, using the keytool utility.
For example:
$Agent_Home/jdk/bin/keytool -import -noprompt -trustcacerts -alias rootWAS -file rootWAS.cer -keystore pskey -storepass passwordEdit the pskey.properties file to ensure:
the custom keystore location and other attributes are properly set.
useCustomSSLConfiguration is set to true.