Managing User Authentication
This section provides overviews of user authentication, outbound user authentication, inbound user authentication, and discusses how to:
Activate user authentication on service operations.
Set up user authentication on sending systems.
Exclude PeopleSoft authentication tokens in outbound requests to PeopleSoft nodes.
Access to invoke service operations is enforced at the user level.
When integrating with other PeopleSoft systems, user authentication determines the user ID to set on outbound integrations. The receiving system extracts this information and uses the user ID to validate against the permission list to which a service operation is assigned. If the user ID is assigned to the permission list, the sender can invoke the service operation.
When using Integration Broker for integrations among PeopleSoft systems, you must implement single signon and set up remote/target nodes as trusted nodes for user authentication to be validated. See Implementing PeopleSoft-Only Single Signon for more information about implementing single signon and defining trusted nodes in the database.
Note: User authentication can be implemented on PeopleTools 8.48 and later systems only.
User IDs
The PeopleSoft system can use the following methods to set the user ID in an outbound transaction:
|
Field or Control |
Definition |
|---|---|
| Authentication Token |
When the node is a PeopleSoft (PIA) node type, the PeopleSoft system automatically generates an authentication token and includes the token in the outbound transaction. The authentication token sets the user ID in the outbound transaction to the user ID that created the service operation. |
| Default User ID |
The Node Definition page contains a Default User ID field. This is the user ID to which the node defaults, when no other user ID described in this section is set. |
| External Name/External Password |
You can programmatically set an external name and external password in the outbound SOAP message header or query string. |
| External User ID/Password |
The Node Definitions page contains an External User ID and an External Password field. These fields are used in conjunction with WS-Security and are used for user authentication and to set the UsernameToken credentials for WS-Security processing. The External Password value is optional. |
On inbound integrations from a PeopleSoft node, the PeopleSoft system looks for a user ID to associate with the permission list set for a service operation in the following order.
Authentication token.
Default User ID.
On inbound integrations not from a PeopleSoft node (External nodes and third-party systems), the PeopleSoft system looks for a user ID to associate with the permission list set for a service operation in the following order.
External Name/External Password.
External User ID/External Password.
Default User ID.
The outbound user authentication process determines the user ID to identify and attach to the outbound service operation. If the receiving system is a PeopleSoft system, the system validates the user ID and if the user ID belongs to the permission list to which the service operation is assigned, the service operation can be invoked.
The PeopleSoft system sets the user ID based on whether the sending node type is a PeopleSoft node (PIA) and by user ID information that may be defined in the SOAP message included with the service operation.
Outbound User Authentication: Sending Node is PeopleSoft Node Type
The following diagram illustrates the user authentication process when the local sending node is a PeopleSoft node:
Image: Outbound User Authentication Processing when the Sending Node is a PeopleSoft Node
The following diagram illustrates the user authentication process when the local sending node is a PeopleSoft node.
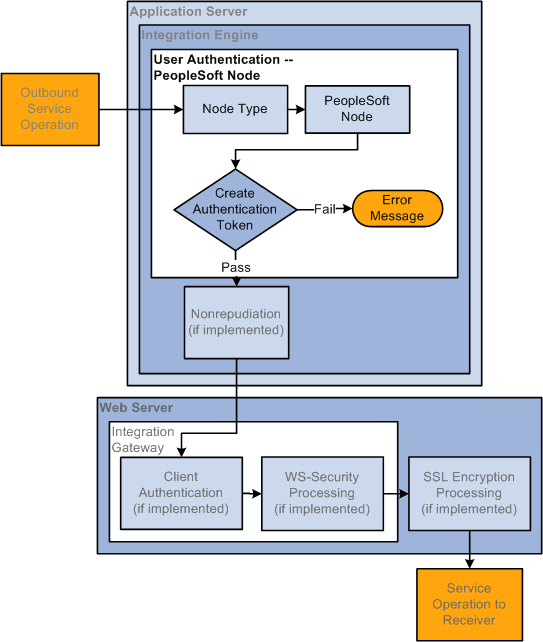
When the sending node is a PeopleSoft node, the user authentication process creates an authentication token to include in the transaction. The token is used on the receiving system to identify the sending node.
Note: The sending node must be defined as a trusted node on the receiving system for the PeopleSoft authentication token to be validated.
Outbound User Authentication: Sending Node is not PeopleSoft Node Type
The following diagram illustrates the user authentication process when the local sending node is not a PeopleSoft node type:
Image: Outbound User Authentication Processing when the Sending Node is Not a PeopleSoft Node
The following diagram illustrates the user authentication process when the local sending node is not a PeopleSoft node type.
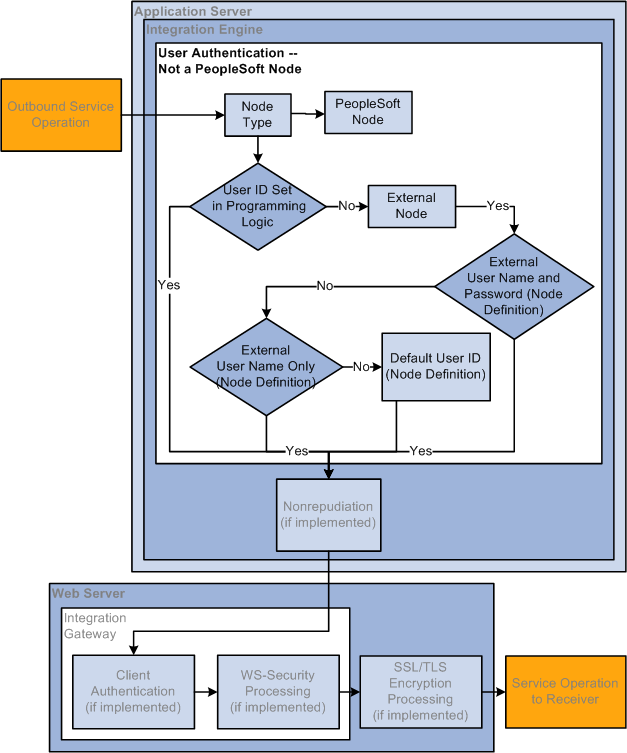
When the sending node is not a PeopleSoft node, the system first looks at the SOAP message associated with the service operation to see if an external user ID or external user ID and password have been provided programmatically in the outbound SOAP message header. If so, the system uses that user ID/password and the service operation passes user authentication.
If an external user ID or external user ID and password are not specified programmatically in the SOAP message header, the system looks on the external node definition for user ID and password information. The system first looks for user ID and password information in the External User ID and External Password fields on the Node Definition page. If no External User ID or no External User ID/External Password is set, the system uses the Default User ID set on the Node Definitions page.
To summarize, when the sending node is not a PeopleSoft node type, the system follows this precedence for setting the user ID in the outbound service operation:
User ID/password set in SOAP message header.
User ID and password set in External User ID and External Password fields on the local external node definition.
User ID set in the External User ID field on the local external node definition.
User ID set in the Default User ID field on the local external node definition.
The inbound user authentication process determines the user ID that has been sent with an inbound service operation and determines if the sender is able to invoke the service operation.
The inbound user authentication process depends on whether the sender is a PeopleSoft node, the sender is an external node, or if the sender is not associated with any node. This section discuss user authentication processing for each of these situations.
Inbound User Authentication: PeopleSoft Node is the Sending Node
The following diagram illustrates the inbound user authentication process when a PeopleSoft node type is the sending node:
Image: Inbound User Authentication Processing when the Sending Node is a PeopleSoft Node
The following diagram illustrates the inbound user authentication process when a PeopleSoft node type is the sending node.
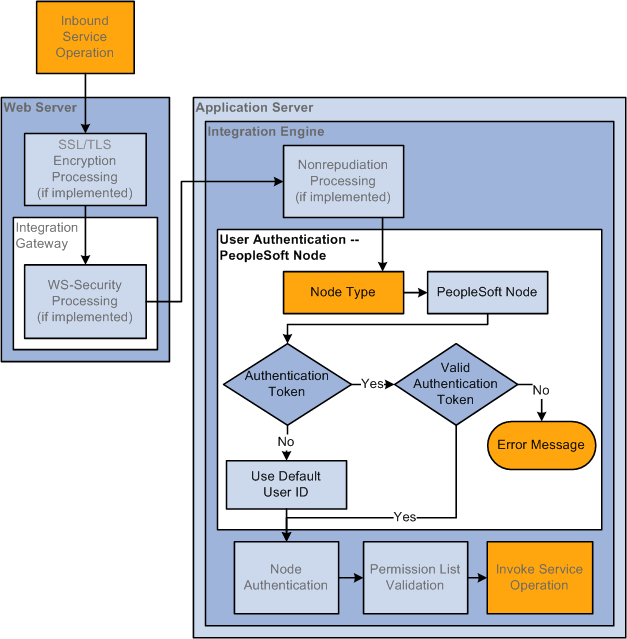
If the sending node is a PeopleSoft node, the system determines if an authentication token has been sent with the transaction. The system uses the authentication token to verify the sending node.
Note that the sending node does not need to be defined as trusted node on the receiving system for the PeopleSoft authentication token to be validated.
See Understanding User Authentication.
If authentication passes, the service operation has passed user authentication. If the authentication cannot be validated an error message is generated.
If no authentication token is included with the service operation, the system uses the default user ID on the external PeopleSoft node as the user ID.
Inbound User Authentication: External Node is the Sending Node
The following diagram illustrates user authentication processing when the sending node is an external node:
Image: Inbound User Authentication Processing when the Sending Node is an External Node
The following diagram illustrates user authentication processing when the sending node is an external node.
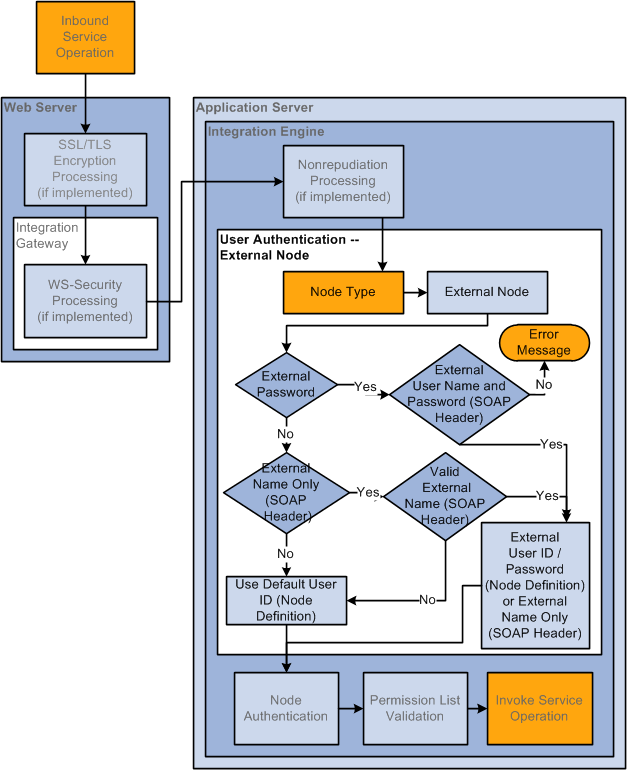
If the sending node is an external node type, the system first looks for a user ID and password set in the SOAP message header included with the inbound service operation. If both a user ID and password are not found, the system looks in the SOAP message header for a user ID only. If no user ID/password or no user ID are found in the SOAP message header, the system uses the user ID set in the Default User ID field in the remote node definition.
Inbound User Authentication: Third–Party System Sending the Service Operation
The following diagram illustrates user authentication processing when a third-party system sends a service operation:
Image: Inbound User Authentication Processing when the Sending Node is a Third-Party System
The following diagram illustrates user authentication processing when a third-party system sends a service operation.
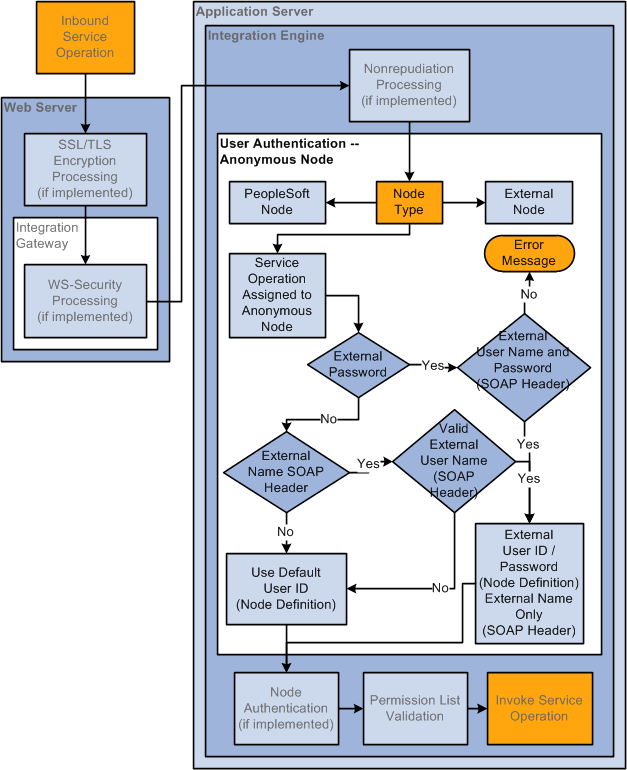
Because third-party systems do not understand the concept of a node as defined and used within the context of PeopleSoft systems, PeopleSoft assigns transactions that have no node specified to a PeopleSoft-delivered Anonymous node.
If the PeopleSoft system first checks the SOAP message header for an external name and password set programmatically.
If none is found or if the system cannot validate the user ID or password that was set programmatically, it uses the Default User ID set on the Node Definitions page on the remote Anonymous node definition.
To activate user authentication on a service operation:
Access the Service Operations-General page ( and click the General tab.
Check the User/Password Required check box.
Save the changes.
This section discusses how to:
Set up user authentication on remote PeopleSoft nodes.
Set up user authentication on remote external nodes.
Set up user authentication for third-party systems.
Understanding Setting Up User Authentication on Sending Systems
To set up user authentication on a sending system you must define the user ID on the remote node for the outbound transaction.
Setting Up User Authentication on Remote PeopleSoft Nodes
No set up is required to set up user authentication on a remote PeopleSoft (PIA) node type. An authentication token is automatically included in the outbound transaction. If the receiving system fails to authenticate the token an error message is returned. .
Setting Up User Authentication on Remote External Nodes
You can set the user ID for user authentication in any of the following ways on an external node:
External Name/Password. Set programmatically in the SOAP message header or query string.
External User ID and External Password. Set using the Node Definitions page.
Default User ID. Set on the Node Definitions page.
Note: The user ID you specify must have access to the permission list to which a service operation is assigned to invoke the operation on the receiving system.
To access the Node Definitions page select
Setting Up User Authentication for Third-Party Systems
As discussed previously in this section, all inbound transactions that do not have PeopleSoft (PIA) node or external (External) node type specified are assigned to an Anonymous node.
You can set the user ID in requests from third-party systems programmatically in the external name/password elements in the outbound SOAP message header.
If the system does not find an external name or password in these locations, it uses the Default User ID field that you define on the remote Anonymous node.
This section discuss how to exclude PeopleSoft authentication tokens in outbound requests to PeopleSoft nodes.
Understanding Excluding PeopleSoft Authentication Tokens in Outbound Requests to PeopleSoft Nodes
A PeopleSoft authentication token in an outbound request to a PeopleSoft target node signifies to the target PeopleSoft target system that the sender is a valid user on its system.
However, for some integrations there can be many users or validating users may not be warranted. In such cases you can exclude the PeopleSoft authentication token from inclusion in outbound requests to PeopleSoft target nodes.
When the PeopleSoft authentication token is excluded in a request, the default user ID for the sending node on the target system is the user ID used for integration authentication.
When you exclude PeopleSoft authentication tokens, user authentication is not performed. In lieu of user authentication, you can perform node authentication when authentication tokens are excluded. The following set-up is required on sending and receiving systems for node authentication:
Install application server-based digital certificates.
See Installing Application Server-Based Digital Certificates
Implement two-way SSL.
Viewing Service Operations where PeopleSoft Authentication Tokens Have Been Excluded
Use the Exclude PSFT Auth Token page (IB_SVCSETUP5) to view service operations where PeopleSoft authentication tokens have been excluded.
To access the page, select and click the Exclude PSFT Auth Token tab.
Image: Service Configuration – Exclude PSFT Auth Token page
This example illustrates the Services Configuration – Exclude PSFT Auth Token page.
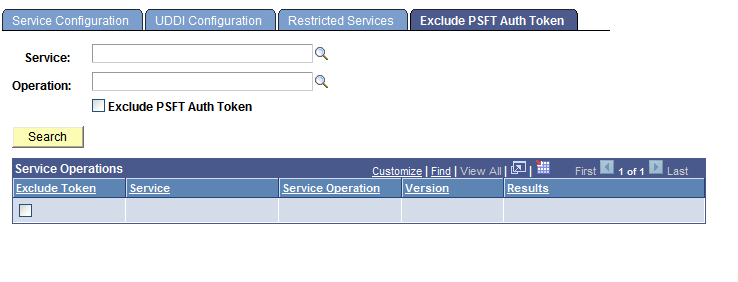
To view service operation where PeopleSoft authentication tokens have been excluded:
Access the Exclude PSFT Auth Token page ( and click the Exclude PSFT Auth Token tab).
Select the Exclude PSFT Auth Token box under the Operation field.
Click the Search button.
The system displays all service operations where the PeopleSoft authentication token has been excluded and will not be included in the service operation transaction.
Excluding PeopleSoft Authentication Tokens in Outbound Requests
Use the Exclude PSFT Auth Token page to exclude authentication tokens in outbound requests:
To access the page, select and click the Exclude PSFT Auth Token tab.
Image: Services Configuration – Exclude PSFT Auth Token page
This example illustrates the Services Configuration – Exclude PSFT Auth Token page. The example shows that the PeopleSoft authentication token has been excluded from the QE_ROUTE_ARR and QE_ROUTE_SYNC service operations
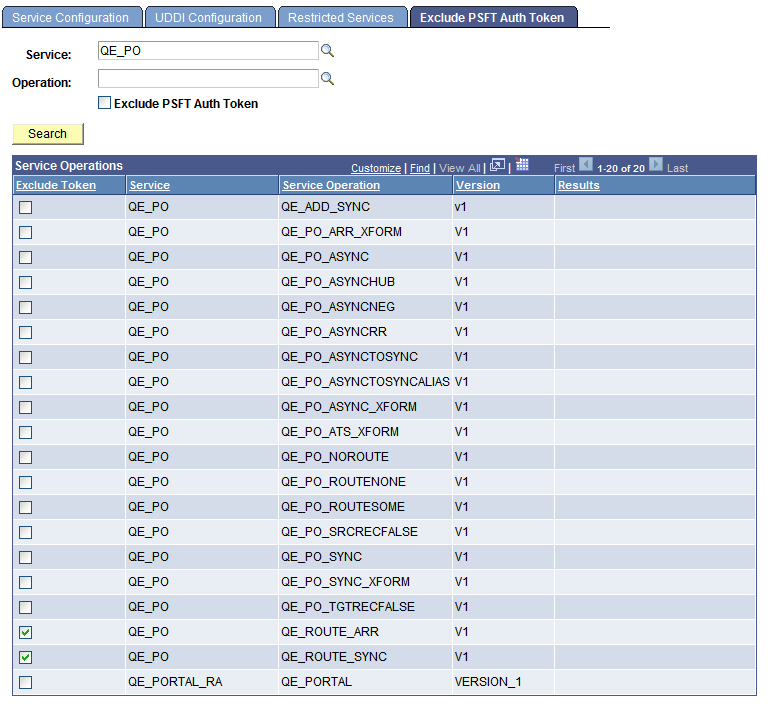
In the example shown, a search was performed on the service QE_PO. The QE_ROUTE_ARR and QE_ROUTE_SYNC service operations have been selected, and therefore the PeopleSoft authentication token will be excluded from those service operations. Scrolling to the right would reveal a Results column that indicates the selection was successful.
To exclude a PeopleSoft authentication token in an outbound request:
Access the Exclude PSFT Auth Token page ( and click the Exclude PSFT Auth Token tab).
Select one or more service operations from which to exclude the PeopleSoft authentication token:
To select one service operation, click the Service and Operation lookup buttons to locate the service operation. Click the Exclude PSFT Auth Token box.
To select multiple service operations, enter all or part of the service name or service operation name. Click the Search button. A list of results displays in the Service Operations section. Check the Exclude Token box next to each service operation that should not include a PeopleSoft authentication token.
Note that you can also click the Search button to display all service operations in the database.
Click the Save button.