Securing Reports
This section discusses about:
Secure Report Distribution
Masked Data in Reports
You have different security considerations for distribution based on the type of output: file, email, or web.
When you output reports as files, remember that files are stored in the directories and files that you specified in the directory templates and file templates. These directories and files are on your file server and are not stored in the PeopleSoft database. You must set up network security to map the accessibility of the reports and ensure that unauthorized users do not have access to these reports on your file server.
When you output reports as email, you control who receives the reports using the email template in the report request. You can specify precise email addresses in the email template, or indirectly specify email addresses by user ID or role ID. If you specify your email recipients using role or user IDs, then the email addresses from those profiles are used.
When you output reports using the web, the reports are distributed through Report Manager. You control who receives the reports using security templates in the report requests. If nothing is entered in the security template, the default recipient is the user who runs the report.
You can associate a scope with the email template or the web security template using %DES% variables. You must specify who can modify the email template or the security template from the report request, and who can access the values of the %DES% variable in the table associated with the scope.
Additionally, when a report is distributed through email or web, it uses the report server to run the report and then distribute the output. In the report server, the directory templates and file templates from the report requests are used as temporary locations to store the intermediate files before the reports are transferred to the report repository or to the email system. Access to the file server that stores the intermediate reports should be secured through your network security. Set up PeopleSoft Process Scheduler as a Tuxedo Service so that PS/nVision reports can be run in the background and no data can be viewed during the report execution time.
PS/nVision reports that use query, connected query, or composite query as a data source may include data fields containing sensitive information, which should be masked with a masking character, for example, an asterisk (*).
The data fields that are masked in the data source will appear as masked in the PS/nVision report.
If a PS/nVision layout query fails due to data masking, the PS/nVision report using this layout will fail and data permission error will be displayed in the message log.
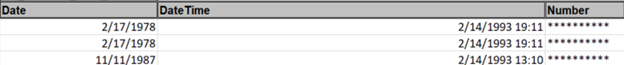
Image: PS/nVision report with masked values
This example illustrates an nVision report with masked values for the Number field because this field is masked in the query data source.
Note: Data masking is not implemented for matrix reports.