Setting Up WSRP Security Options
This section discusses how to:
Use HTTPS protocol to communicate between producer and consumer.
Install certificates for encryption and signature.
Note: Ensure that your PeopleSoft system is completely configured for SSL, including setting the value of KeyStorePwd in configuration.properties to be the encrypted value of the truststore password specified when you installed your PeopleSoft web server.
If you choose the security option Authentication token as Username token in clear text format, Oracle recommends that you use HTTPS to protect the user name and password. For you to use HTTPS protocol, both the producer and consumer must first configure and enable SSL for HTTPS on their web servers.
Before the consumer imports the producer \pspc\wsdl\wsrp4j_service.wsdl, the producer must modify the file by setting it to HTTPS mode and changing the port number from the HTTP port number to the HTTPS port.
Note: The system automatically inserts the host name and port number using the values entered during installation.
Example:
<?xml version="1.0" encoding="UTF-8"?>
<wsdl:definitions targetNamespace="urn:oasis:names:tc:wsrp:v1:wsdl"
xmlns:bind="urn:oasis:names:tc:wsrp:v1:bind"
xmlns="http://schemas.xmlsoap.org/wsdl/"
xmlns:wsdl="http://schemas.xmlsoap.org/wsdl/"
xmlns:soap="http://schemas.xmlsoap.org/wsdl/soap/">
<import namespace="urn:oasis:names:tc:wsrp:v1:bind"
location="wsrp_v1_bindings.wsdl"/>
<wsdl:service name="WSRPService">
<wsdl:port binding="bind:WSRP_v1_Markup_Binding_SOAP" name="WSRPBaseService">
<soap:address location="https://<Producer Hostname>:<SSL port>/pspc/wsrp4j/WSRPBaseService"/>
</wsdl:port>
<wsdl:port binding="bind:WSRP_v1_ServiceDescription_Binding_SOAP" name="WSRPServiceDescriptionService">
<soap:address location="https://<Producer Hostname>:<SSL port>/pspc/wsrp4j/WSRPServiceDescriptionService"/>
</wsdl:port>
</wsdl:service>
</wsdl:definitions>
Note: In the preceding example, <Producer Hostname> is the host name of the producer web server and <SSL port> is the SSL port number of the producer web server.
If you are using an SSL accelerator in your PeopleSoft system, and you want to use the HTTPS protocol for WSRP to communicate with PeopleSoft Pure Internet Architecture, you need to use the following properties file:
PS_CFG_HOME\webserv\peoplesoft\applications\peoplesoft\pspc\WEB-INF\config\services\PIAService.properties.
Note: This is similar to using Web Profile Default Addressing fields.
In this properties file, specify the default protocol, host, and port to override the incoming request protocol, host, and port. The settings that WSRP checks in the PIAService.properties file are:
|
Field or Control |
Definition |
|---|---|
| usePIAConfig = true |
Checks whether settings in the PIAService.properties file should be used. If you set usePIAConfig to true, the incoming request is overridden by values set in the PIAService.properties file. Otherwise, the system uses the incoming request values for protocol (scheme), host, and port. |
| portalHost=<your webserver host> |
The default host to use. |
| portalPort=<your port> |
The default port to use. |
| SSLToPIA=true |
If you set SSLToPIA to true, the system uses HTTPS; otherwise, it uses the HTTP scheme. |
When you select the Authentication token as Username token with full security option, both the producer and the consumer must install the certificates that are used to enable the encryption and signature.
Image: Process for installing certificates and enabling encryption and signature
This diagram illustrates the process flow for installing certificates and enabling encryption and signature:
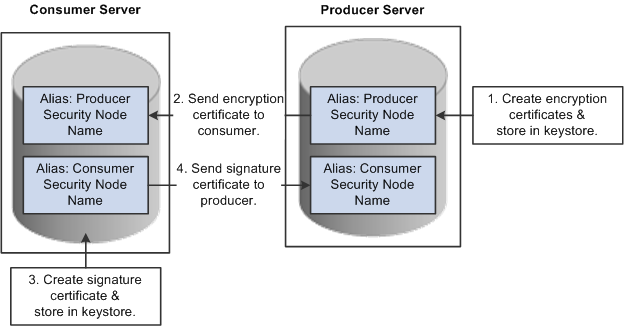
First use the following reference for instructions on how to create and request your encryption and signature certificates.
See Implementing WebLogic SSL Keys and Certificates.
Enabling Encryption
Producer:
The encryption key and certificate are created on the producer and stored in the web server predefined key store.
Note: Make sure that when you create the entry to hold your encryption keys and certificate in your key store, the entry's alias name must be the security node name of your producer server.
Send the encryption certificate to the consumer. You can do this by using an out-of-band method, such as file copy or email.
Consumer:
Install the encryption
certificate on the consumer server by running pskeymanager.cmd -import.
Note: Make sure that when you import the certificate, the entry's alias name must be the security node name of your producer server.
Enabling Message Signature
Consumer:
Create the signature key and certificate on the consumer and store in the web server predefined key store.
Note: When you create the entry to hold your signature keys and certificate in your key store, the entry's alias name must be the security node name of your consumer server.
Send the signature certificate to the producer. You can do this by using an out-of-band method, such as file copy or email.
Producer:
Install the signature
certificate on the producer server by running pskeymanager.cmd -import.
Note: When you import the certificate, the entry's alias name must be the security node name of your Producer server.
Encrypting Key Store Password Using PSCipher
A copy of the wss.properties file, which contains PKI Java key store information such as key store file location and password for the key store can be found on both the consumer and producer servers:
The location of the wss.properties file on the consumer web server is:
PS_CFG_HOME\webserv\peoplesoft\applications\peoplesoft\PORTAL.war\WEB-INF\classesThe location of the wss.properties file on the producer web server is:
PS_CFG_HOME\webserv\peoplesoft\applications\peoplesoft\pspc.war\WEB-INF\classes
Here is the sample wss.properties file:
org.apache.ws.security.crypto.provider=org.apache.ws.security.components.crypto.Merlin
org.apache.ws.security.crypto.merlin.keystore.type=jks
org.apache.ws.security.crypto.merlin.keystore.password=*** Encrypted password ***
org.apache.ws.security.crypto.merlin.file=keystore/pskeyTo define the location
of the key store file, the portal administrator needs to define the
proper key store file to replace above theorg.apache.ws.security.crypto.merlin.file property.
To encrypt the key store password using Java program PSCipher:
Run PSCipher.bat (.sh for UNIX) to encrypt the password
% PSCipher.bat <password>For example,
PSCipher interopprovides output asencrypted_passwordUpdate the encrypted password in the wss.properties file for
org.apache.ws.security.crypto.merlin.keystore.passwordwith the output from PSCipher.
See Understanding the Advanced Encryption Standard (AES) Implementation.