Security Considerations When Using Simplified Analytics
The analytic reports that are created using Simplified Analytics can be restricted to be accessed only within the component context, that is within the My Analytics section in the right panel of the component.
To configure for restricting reports within the component context, deselect the When used as analytics template, allow created reports to be accessed outside the component context option in the Pivot Grid Wizard - step 4 for the base template model. This option is selected for all Pivot Grid models by default.
Image: Pivot Grid Wizard - step 4 - Fluid Options
This example illustrates the Pivot Grid Wizard - step 4. In the Fluid Mode Options section, the When used as analytics template, allow created reports to be accessed outside the component context option is selected.
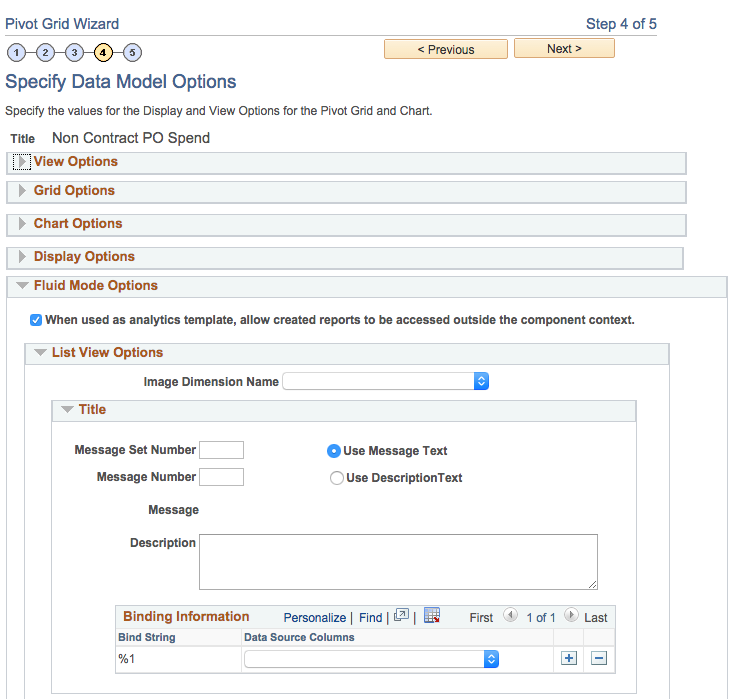
In general, this option should be deselected if Authorization as Service is implemented for the Simplified Analytics of the component, where there is custom logic in code to control who can see or create which type of reports. Because custom authorization code cannot be run outside the component context, this option must be deselected.
When this option is deselected, the reports that are created using the Create Analytics Wizard based on the specific template:
Can be accessed only from the My Analytics section at the right of the component from which it is created.
Cannot be published to the fluid homepage using the Publish or Add to Homepage options.
Cannot be accessed using the Pivot Grid Viewer (Reporting Tools, Pivot Grid, Pivot Grid Viewer), drilling URLs, pagelets, related actions, and so on.
This security option can also be used if the prompt values passed from the page (as bind parameters) control the security of the data that the users are viewing. These prompts (such as the Supplier in the previous examples) are:
Read-only when they are accessed from within the component context (for example, My Analytics).
Editable when they are accessed from outside the component context (such as when they are invoked from the landing page).
Therefore, you can use this security option to restrict the report only to the component context as needed.
However, Oracle PeopleSoft strongly recommends that you implement row-level security on the query to restrict the data for specific users. Further, the view behind the lookup prompts for the analytic reports should also include the correct security joins to display only the list of values allowed for any user.
You can use query security or web services to secure access to simplified analytics reports and templates.
For performance reasons, simplified analytics will execute query security before invoking an authorization application class. In other words only if the user has access to the query behind the template/report it will be part of the available list for authorization class to filter further.
Any authorization class defined on the component (enabled for simplified analytics) will be invoked while getting the list of reports available for the user, or while getting the list of templates available to create the report for the user.
Like any other authorization service, the PTCS_SECURITY:SECURITY:AuthRequest application class needs to be extended to implement simplified analytics authorization logic. This class has a variable “MasterTemplate”. The value of this variable is empty for all non-simplified analytics use cases. The code gets invoked twice while rendering simplified analytics as follows:
The first request is for the list of templates. You can write custom logic to control which template can be made available for specific users. In this case, the value of the ‘MasterTemplate’ variable value is ANALYTICSERVICE.
The second request will be to correspond to the saved reports. This includes both the user-created reports as well as the administrator-published reports. In this case, the ‘MasterTemplate’ variable will point to the parent pivot grid template used to create the report.
In both requests you can use the details of the level 0 field values on the page to apply custom logic to filter the reports/templates. The AuthRequest.KeyVal array in the app class includes all of the level 0 field name and values in the format RECNAME.FIELDNAME=CURRENTFIELDVALUE.
In addition to using the authorization service as a security control for reports/templates, it can also be used to control the list of reports/templates that can be made available based on the current page/current data in the component the user is accessing.
Here is an example of implementing an application class that is associated to the supplier watch list component.
Note: When authorization as a service is enabled, the code is called while getting the list of the reports to be shown on "My Analytics" for the user and also while getting the list of templates for the user for report creation. This example code handles both the cases.
import PTCS_SECURITY:Security:*;
class SupplierWatchlist extends PTCS_SECURITY:Security:SecurityHandler
method GetAuthorization &arrAuthReq As array of PTCS_SECURITY:Security:AuthRequest);
protected
property array of PTCS_SECURITY:Security:AuthRequest oAuthRequest;
private
Constant &PGNAME = "PGNAME";
end-class;
method GetAuthorization
/+ &arrAuthReq as Array of PTCS_SECURITY:Security:AuthRequest +/
/+ Extends/implements PTCS_SECURITY:Security:SecurityHandler.GetAuthorization +/
Local string &SET, &SUPP, &master, &PG, &name, &val, &MST, &COMP, &COMPITEM,
&pglt, &ParentServiceId, &template;
Local number &i, &k, &j, &a, &b;
Local array of string &templ;
Local SQL &sql;
&pglt = %Page;
/*Process the level 0 field to get any needed context information. In this case the application page field CONTEXT_WRK.CONTEXTVAL stores context information*/
For &k = 1 To &arrAuthReq.Len
For &j = 1 To &arrAuthReq [&k].KeyVal.Len
&name = &arrAuthReq [&k].KeyVal [&j][1];
if &name = "VENDOR_SETID.VENDOR_ID " Then
&val = &arrAuthReq [&k].KeyVal [&j][2];
break;
end-if;
End-For;
End-For;
&templ = CreateArrayRept("", 0);
/*PS_TEMPLATE_CREF is an example custom application table that stores which
templates/admin published reports which user has access to. It is based
on the operator id, page name and context page field (VENDOR_ID) value.
Here we query to get the current list applicable for the specific user*/
&sql = CreateSQL
("select TEMPLATE_DESC from PS_TEMPLATE_CREF WHERE OPRID = :1
AND PAGE_FIELD_NAME = :2
AND VENDOR_ID =:3",
%OperatorId, &pglt, &val, &template);
While &sql.Fetch(&template)
&templ.Push(&template);
End-While;
For &i = 1 To &arrAuthReq.Len
/*Get the current report name*/
&PG = &arrAuthReq [&i].GetParameterValue(&PGNAME);
/*Get the current master template*/
&MST = &arrAuthReq [&i].MasterTemplate;
/*Is the current report is present in the allowed list of administrator
published reports for the user*/
&a = &templ.Find(&PG);
/*Is the current template available in the list of allowed templates for
the user for creating a report*/
&b = &templ.Find(&MST);
/*Allow if the current report is in the list of allowed published reports for
the user or allow if the template is allowed for report creation for the user.
Do not allow otherwiser*/
If (&a > 0 Or &b > 0) Then
&arrAuthReq [&i].Access = "T";
Else
&arrAuthReq [&i].Access = "F";
End-If;
End-For;
end-method;
Note that the custom authorization logic to control the access for templates/reports will not be executed outside the component context, for example, while accessing the published reports from the landing page. As a result, it is recommended that if you are using the authorization service for controlling report access, clear the Fluid option
When used as an analytics template, Step 4 of the Pivot Grid wizard allows created reports to be accessed outside the component context
A Simplified Analytic report that uses query, connected query, or composite query as a data source may include data fields containing sensitive or personally identifiable information (PII) data. Data masking enables you to use a masking character, for example, an asterisk (*) or any character, to mask output and prevent the display of this data. The SetDisplayMask method replaces each character of the displayed field text value with the chosen mask character.
Data masking in Simplified Analytic reports behave similar to data masking in Pivot Grid reports. See Data Masking in Pivot Grid