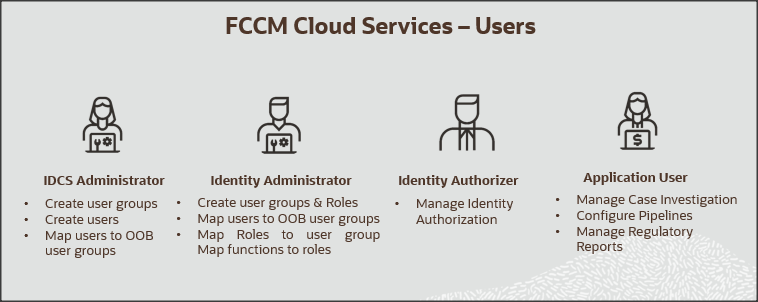
In Oracle Financial Crime and Compliance Management Cloud Service, users have roles through which they gain access to functions and data. Users can have any number of roles.
The following figure shows the User Persona Details:

NOTE:
User-Group mapping changes from IDCS will take 5 minutes to sync with application. If these changes are made during active user session then it will be reflected on next login.
Role-based security in Oracle Financial Services Crime and Compliance Management Cloud Service controls who can do what on which data.
This table summarizes role-based access.
Component |
Description |
Who |
Is a role assigned to a user? |
What |
Is a function that users with the role can perform? |
Which Data |
Is the set of data that users with the role can access when performing the function? |
This table provides some examples of role-based access.
Who |
What |
Which Data |
Data Administrator |
Can perform Data Preparation and ingestion |
Business Data |
Case Analyst |
Can view cases and update cases |
Business and Operational Data |
NOTE:
The new user should have the following roles to access Home page of the Cloud application.
· Function read role
· Group read role
· User read role
· Role read role
In order to allow users to access functions in the application, Administrators must classify users and the functions they are permitted to access. The Functions imply controlling various actionable units in the application via functional access. For example, create a case, add a customer, add an account, etc.
Users are mapped to groups,which must be mapped to specific security attributes, such as Business Domain and Jurisdiction. Groups are mapped to Roles, and Roles are mapped to Functions. Users can perform activities associated with their user group throughout the functional areas of the application.
Before mapping security attributes, you must complete the following:
1. Create users
5. Map user groups to security attributes
Security layers control how users interact with the application. The following table describes the security layers.
Security Layer |
||
Type |
Controls |
Description |
Roles |
Access to Features and Functions |
User roles identify which features and functions the user can access within the application. For example, Case Analysts can access and take action on cases. |
Business Domains |
Access to Case and Business Information |
You can restrict access along operational business lines and practices, such as Retail Banking. Users can only see cases that are assigned to at least one of the business domains their user group is mapped to. |
Jurisdictions |
Access to Case Information |
You can restrict access using geographic locations and legal boundaries. Users can only see cases that belong to the jurisdiction their user group is mapped to. |
The following table provides the User Group, User Role mapping, and activities.
Group |
User Role |
Functionality |
Identity Administrator |
Identity Administrator |
· View the reports · View the object storage · View the OAUTH credentials · Perform the Identity and access management operations |
Identity Authorizer |
Identity Authorizer |
Authorize the Identity and access management operations |
IDCS Administrator |
IDCS Administrator |
· Create users · Map users to IDNTY_ADMIN group · Map users to IDNTY_AUTH group |
| TM User Groups | ||
| TM Group - OFS_TM | ||
Pipeline Administrator Group |
Pipeline Administrator |
· Configure pipelines · Configure threshold sets |
Threshold Administrator Groups |
CS Administrator |
Load watch list data |
Investigation Hub User Groups |
||
IHUB Administrator Group |
IHUB Administrator |
· Configure jurisdictions and business domains · Configure case statuses · Configure case actions · Configure case system parameters · Configure Default Graph UI Settings · Manage Case Template |
IHUB Analyst Group |
IHUB Analyst |
· Search for cases · Investigate cases · Generate Dossier · Recommend case closure |
IHUB Supervisor Group |
IHUB Supervisor |
· Overwrite updates made by Analyst · Search for cases · Investigate cases · Generate Dossier · Approve or reject recommendations to close cases · Close cases |
Scheduler Service User Groups |
||
Job Administrator Group |
Job Administrator |
Manage jobs |
Scheduler Administrator Group |
Scheduler Administrator |
Manage batches |
Process Modelling Framework (PMF) User Groups |
||
IHUB Administrator Group |
Manage Workflow Monitor |
Access the Manage Workflow Monitor window NOTE: The mapping of this role does not allow view, edit, and add actions. |
IHUB Administrator Group
|
Workflow Access |
Access the Process Modeller menu from the Navigation Tree NOTE: The mapping of this role does not allow view, edit, and add actions |
IHUB Administrator Group
|
Workflow Monitor Access |
Access the Process Monitor window NOTE: The mapping of this role does not allow view, edit, and add actions. |
IHUB Administrator Group
|
Workflow Read |
View the PMF workflow |
IHUB Administrator Group
|
Workflow Write |
Perform view, edit, and add actions in PMF |
NOTE:
Administrators must be mapped to all the roles described in the preceding table to allow them to perform these operations in PMF.
Privileges |
Case Supervisor |
Case Analyst |
Access Cases |
x |
x |
Search for Cases |
x |
x |
View Case List |
x |
x |
View Case Summary |
x |
x |
View Event Details |
x |
x |
Set Event Decision |
x |
x |
Generate Dossier |
x |
x |
View/Expand Graph |
x |
x |
View Graph History |
x |
x |
Edit Graph Settings |
x |
x |
View Alerted transactions |
x |
x |
Add/View Accounts |
x |
x |
Add/View Customers |
x |
x |
Add/View Transactions |
x |
x |
Add/View External Entities |
x |
x |
View Related Case |
x |
x |
View Related Events |
x |
x |
Set Case Assignee |
x |
x |
Recommend Close without Regulatory Report |
|
x |
Recommend Close with Regulatory Report |
|
x |
Reject Recommendation |
x |
|
Close a Case as False Positive |
x |
|
Close a Case as True Positive |
x |
|
View Evidence (Attachment and Comment list) |
x |
x |
Add Document |
x |
x |
View Attachments |
x |
x |
Add/Edit Narrative |
x |
x |
View Narrative |
x |
x |
Add Investigation Comments |
x |
x |
Generate CRR Reports |
x |
|
Save Search Criteria of Case List |
x |
x |
Export Case List in Excel |
x |
x |
Export Transactions in Excel |
x |
x |
Privileges |
Case Admin |
Add Case Status |
x |
Edit Case Status |
x |
Add Case Action |
x |
Edit Case Action |
x |
Mapping the Action to Status |
x |
Mapping the Action to User Role |
x |
Configuring Case System Parameters |
x |
Add Business Domains |
x |
Edit Business Domains |
x |
Add Jurisdictions |
x |
Edit Jurisdictions |
x |
Configuring Security Mappings |
x |
Manage Case Template |
x |
Create Case Template |
x |
Update Case Template |
x |
Delete Case Template |
x |
Configure Default Graph UI Settings |
x |