Understanding Data Permission Security for HCM
Data permission security refers to controlling access to the rows of data in your system. In PeopleSoft HCM, you can control access to the following types of data:
People.
Employees.
Contingent workers.
People of interest (POIs) with jobs.
People of interest (POIs) without jobs.
Note: The data of people of interest without jobs is secured differently from the data of people with jobs.
Recruiting job openings.
Departments.
Note: Row security for departments secures department budgets and positions, if you are using Manage Positions. The Departments component is not secured by data permission so control access to department definitions by restricting access to the component or change the search record to DEPT_SEC_SRCH.
The system enforces data permission security with security search views. To understand how this is done it helps to understand how the system retrieves data when you access a component.
When you open a component in PeopleSoft HCM the system displays a search page. The search page represents the search record and the fields that appear are the search keys and alternate key fields that uniquely identify each row of data. The system uses the information that you enter in the key or alternate key fields to select the rows of data that you want to view or manipulate (except for the Add action, where you enter a key and the system creates a new data row). For example, a search page may have EmplID as a key field and Name as an alternate key. If you enter Smith in the Name field, the system retrieves all data rows with Name field data that matches Smith.
The system also uses search records to enforce data permission security. Search views for components that contain sensitive data also contain a security view to control data access.
The system adds the user's security profile, including their user ID and the values of the permission lists attached to their user profile, to the SQL (Structured Query Language) select statement along with the values that the user entered on the search page. The system retrieves the data that matches the criteria from the search page and the user's data permission lists. The system doesn't retrieve data for people to whom you haven't granted the user's permission lists data access.
Using the above example, if you enter Smith in the Name alternate key field, the system retrieves data only for the people with the name Smith to whom you have access, which are workers in department 123. Workers with the name of Smith outside of your security permission, department 123, are not retrieved or accessible to you as the user. This diagram illustrates the data retrieval process:
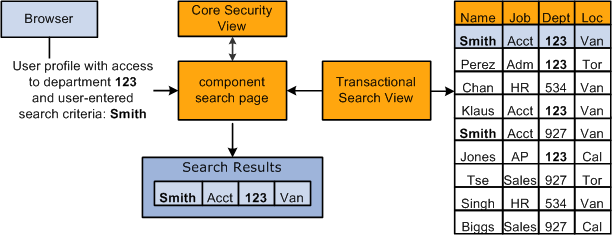
Note: Security for process and queries is enforced in much the same way.
Not all PeopleSoft HCM components require data permission security. Their security requirements can be met using application security (restricting access to the entire page, component, or menu). Only components containing sensitive information, such as salary information, use the security search views. If necessary, you can add data permission security to any component that accesses person data, as long as the search records are defined as SQL views (some search records are defined as SQL tables).
A component can have only one search record. To associate more than one search record with a component (for example, data level security for some users and not for others), you reinstall the component on different menus, one for each search record, and grant access to the appropriate component using application security.
Core Security Views
PeopleSoft delivers the following core security views for components tracking people:
|
Security Views for Components Storing All Person Types |
|||
|---|---|---|---|
|
Type |
Includes Future-Dated Security |
Security View |
Rows Returned |
|
Component search view |
Yes |
PERALL_SEC_SRCH |
One row per EMPLID and distinct search items. Includes future-dated rows. |
|
SQR view |
No |
PERALL_SEC_SQR |
One row per EMPLID. |
|
Query view |
No |
PERALL_SEC_QRY |
One row per EMPLID. |
|
Security Views for Components Storing People With Jobs |
|||
|---|---|---|---|
|
Type |
Includes Future-Dated Security |
Security View |
Rows Returned |
|
Component search view |
Yes |
PERS_SRCH_GBL |
One row per EMPLID and EMPL_RCD combination, effective date, and distinct search items. Includes future-dated rows. |
|
Component search view |
Yes |
PERS_SRCH_EMP |
One row per EMPLID for employees only. Includes future-dated rows. |
|
Component search view |
No |
PERS_SRCH_CURR |
One row per EMPLID. |
|
SQR view |
No |
FAST_SQR_SEC_VW |
One row per EMPLID. |
|
Query view |
No |
PERS_SRCH_QRY |
One row per EMPLID. |
|
Prompt view |
No |
EMPL_ACTV_SRCH |
One row per EMPLID for people with current, active (as of the system date) job records. |
|
Prompt view |
No |
WORKER_PROMPT |
One row per EMPLID for employees and contingent workers with current, active (as of the effective date of the component) job records. |
|
Security Views for Components Storing People With Potentially More Than One Job Data Record |
|||
|---|---|---|---|
|
Type |
Includes Future-Dated Security |
Security View |
Rows Returned |
|
Component search view |
Yes |
EMPLMT_SRCH_GBL |
One row per EMPLID and EMPL_RCD combination, effective date, and distinct search items. Includes future-dated rows. |
|
Component search view |
Yes |
EMPLMT_SRCH_EMPbe |
One row per EMPLID and EMPL_RCD combination for employees only. Includes future-dated rows. |
|
SQR View |
Yes |
FAST_SQRFUT_SEC |
One row per EMPLID. Includes future-dated rows. |
|
SQR view |
No |
FAST_SQR_SEC_VW |
One row per EMPLID and EMPL_RCD combination. |
|
Query view |
No |
EMPLMT_SRCH_QRY |
One row per EMPLID and EMPL_RCD combination. |
|
Prompt view |
No |
PERJOB_PROMPT |
One row per EMPLID for people with current, active (as of the effective date of the component) job records. |
|
Security Views for Components Storing People Without Jobs |
|||
|---|---|---|---|
|
Type |
Includes Future-Dated Security |
Security View |
Rows Returned |
|
Component search view |
N/A |
POI_SEC_SRCH |
One row per EMPLID, POI_TYPE and distinct search items. |
|
SQR view |
N/A |
POI_SEC_SQR |
One row per EMPLID and POI_TYPE. |
|
Query view |
N/A |
POI_SEC_QRY |
One row per EMPLID and POI_TYPE. |
See PeopleTools: PeopleSoft Application Designer
Data permission is controlled on two sides: transaction and user.
Transaction Security Data
Transaction data is the data that is being secured. Certain transaction fields on a transaction data row are used to secure access to that row. The data in these fields is called transaction security data. When the value of the transaction security data matches the value that a user can access (user security data), the system makes the entire row of data available to the user.
When the user accesses the component search page the security search view filters the data rows, displaying only the rows of data with the same transaction security values that the user has access to.
This diagram shows the Department field being used as transaction security data to secure the data of people in the organization in which the user only has security access to the workers in department 123:
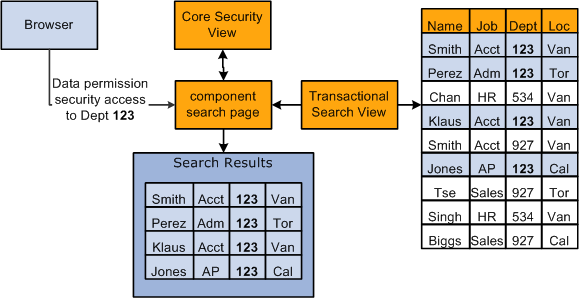
This table lists where you enter and maintain transaction data, to which record the transaction data is saved, and which fields can be used as transaction security data:
|
Data Type |
Transaction Component in which Data is Entered or Maintained |
Record Storing Transaction Data |
Fields Available for Transaction Security Data |
|---|---|---|---|
|
Departments |
Departments component (DEPARTMENT_TBL) |
DEPT_TBL |
|
|
Job openings |
Job Opening page (HRS_JO_360) |
HRS_JOB_OPENING |
|
|
|
JOB |
|
|
POIs without jobs |
|
PER_POI_SCRTY |
|
Note: All people, regardless of type, are first entered in the Add a Person component (PERSONAL_DATA), where you enter their personal information and assign them an ID. These pages do not capture any transaction security data. Transaction security data is captured on the components that you use to enter details about the person's relationship to the organization.
Note: If you create a person but do not create a job data record or POI type record for them the system will save the person as a POI without job with a POI Type of Unknown. Somebody in your organization must have data permission access to unknown POIs in order to access their data and create either a job data or POI type record for them, otherwise the data is inaccessible.
Make sure that users who enter people into the system understand the consequences of not creating and saving a Job Data or POI type record for new people at the time the person is entered in the system.
When a transaction record is successfully completed and saved for the person on the Add an Employment Instance component, Add a Contingent Worker component, Add a POI Instance component, or Add a POI Reltn. component, the system deletes the Unknown POI instance for that person.
See (Classic) Adding a Person.
User Security Data
User security data is the data about a user's security access. It enables the system to ensure that users have access only to that which you have granted them access. User security data for HCM data permission is the data permission that you assign to permission lists and the roles and users to whom you assign the permission lists.
Data permission is granted to row security (tree-based) permission lists (ROWSECCLASS) and regular (role-based) permission lists (CLASSID). Both permission lists are created using the Permission Lists component and Copy Permission Lists component.
When you create a permission list on the Permission Lists component you can assign security to a number of different aspects of the application. Data permission is assigned separately on the Security by Dept Tree page and Security by Permission List page.
Note: When you add a permission list to the Security by Dept. Tree component, the system saves it as ROWSECCLASS.
This diagram shows that permission lists are created, assigned data permission (using either security by department tree or security by permission list), and then assigned to a user directly on the User Profile - General page as the Row Security permission list or assigned to a user on the User Profile - Roles page by assigning roles to the user, which are associated with permission lists:
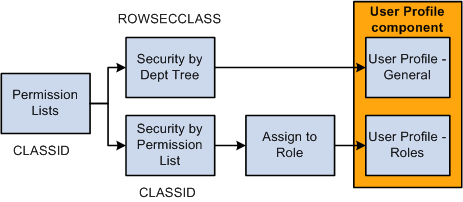
This table lists the key differences between role-based permission lists with data permission and row security permission lists:
|
Row Security Permission Lists |
Role-Based Permission Lists |
|---|---|
|
Are assigned to users on the Row Security field on the User Profile – General page. |
Are assigned to users by way of roles. |
|
Are limited to one per user. |
Users can have multiple role-based permission lists and the combined data permission access of each list. |
|
Bring with them only the data permission assigned to the user on the Row Security field on the User Profile - General page. |
Bring with them data permission access assigned to them on the Security by Permission List page and any application security access granted to the permission list on the Permission Lists component. The user will not have access to any data permission assigned to them on the Security by Dept Tree page. |
|
Should have only department security tree-based security. |
Can have only non-department tree-based security. |
Note: You can use the same permission list as a row security permission list and a role-based permission list by adding it to both the Security by Dept Tree component and Security by Permission List component and then adding them to the user on the User Profile - General page and by way of roles.
Note: The system recognizes non-tree based security associated with row security permission lists. Customers who modified the system to use non-tree based security in previous releases only have to import the customized table capturing the row security permission lists and security definitions into SJT_CLASS. You can continue to assign the permission lists to users in the Row Security field on the User Profile - General page.
New customers, or customers using non-tree based security for the first time, should use role-based permission lists. This will provide you much greater flexibility.
This diagram shows the search page determining which permission lists a user has and what data permission the list gives the user. The user, TRN, is associated with the permission list TRAIN for both row security and permission lists through roles. Since permission list TRAIN is granted access to worker's records in department 123 only, the search results will display only those workers from this department:
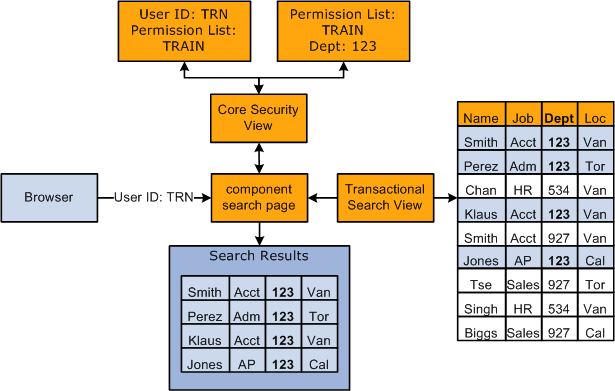
This table lists where you enter and maintain user security data and to which record the user security data is saved:
|
Data Type |
Security Page in which Data is Entered or Maintained |
Record Storing User Security Data |
|---|---|---|
|
Row security permission lists |
Security by Dept Tree page |
SCRTY_TBL_DEPT This data is loaded into SJT_CLASS_ALL |
|
Role-based permission lists |
Security by Permission List page |
SJT_CLASS This data is loaded into SJT_CLASS_ALL |
|
Permission lists assigned to roles |
Roles - Permission Lists page |
PSROLECLASS This data is loaded into SJT_OPR_CLS. |
|
Roles assigned to users |
User Profile - Roles page |
PSROLEUSER This data is loaded into SJT_OPR_CLS |
|
Row security permission lists assigned to users |
User Profile - General page |
PSOPRDEFN This data is loaded into SJT_OPR_CLS |
Note: The data from PSROLECLASS, PSROLEUSER, and PSOPRDEFN is loaded into SJT_OPR_CLS either automatically by the system, when you enable the USER_PROFILE and ROLE_MAINT messages, or when you run the Refresh SJT_OPR_CLS process.
See Understanding PeopleSoft Security.
See Setting Up and Assigning Tree-Based Data Permission.
See Assigning Role-Based Data Permission Security to Permission Lists.
The system stores security data in transaction and user security join tables (SJTs). When you access a transaction component with a security search view, the security view references the security join tables to determine how the data is secured and what access the user has.
This graphic shows the search page determining which permission lists a user has and what data permission the list gives the user using either the transaction or user security join tables. The transaction security join table is determined by the type of data stored in the component:
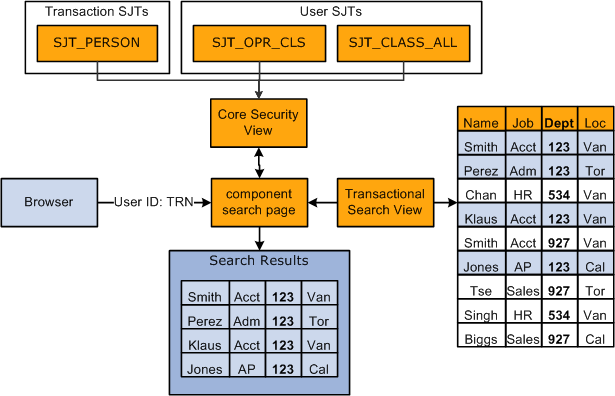
Transaction Security Join Tables
Each transaction security join table stores the transaction data required to secure each row of data. The security join tables store one row of data for each unique combination of key fields.
There are four transaction security join tables:
|
Transaction Security Join Table |
Description |
Stores Data From: |
Key Fields |
|---|---|---|---|
|
SJT_PERSON SJT_PERSON_USF Note: SJT_PERSON is used by customers using the core job data components and SJT_PERSON_USF is used by customers using the USF job data components. |
Contains transaction data for the people (employees, contingent workers, POIs with jobs, and POIs without jobs) in your HCM system. |
|
SCRTY_TYPE_CD SCRTY_KEY1 SCRTY_KEY2 SCRTY_KEY3 EMPLID |
|
SJT_DEPT |
Contains the transaction data for the HCM departments. |
DEPT_TBL |
SCRTY_TYPE_CD SCRTY_KEY1 SCRTY_KEY2 SCRTY_KEY3 SETID DEPTID |
|
HRS_SJT_JO |
Contains the transaction data for the job openings in your system. |
|
SCRTY_TYPE_CD SCRTY_KEY1 SCRTY_KEY2 SCRTY_KEY3 HRS_JOB_OPENING_ID |
The key fields are:
SCRTY_TYPE_CD (security access type code)
Security access types indicate which field is used for transaction security data. For example the security type 002 enables you to secure person data by location.
Security access types are unique to a security access set.
SCRTY_KEY1, SCRTY_KEY2, and SCRTY_KEY3 (security keys)
The key security fields uniquely identify the security transaction data securing a row of data. The system determines the key fields by the security access type. For example, if person data is secured by location, then the key security fields are BUSINESS_UNIT (the prompt value for location) and LOCATION (the third key field isn't required for this example).
EMPLID
A person's unique identifying number that is assigned to them on the Personal Data pages.
SETID and DEPTID
A department's set ID and department ID.
HRS_JOB_OPENING_ID
A job opening's unique identifying number, which is assigned to it on the Job Opening page.
Each table stores additional fields depending on the type of security you are using.
For example, if you are securing the data of people with jobs using the security access type Job Department Tree (001), the key fields of the security join table SJT_PERSON looks like this:
|
SCRTY_TYPE_CD |
SCRTY_KEY1 |
SCRTY_KEY2 |
SCRTY_KEY3 |
EMPLID |
|---|---|---|---|---|
|
001 |
Department set ID: SHARE |
Department ID: 123 |
N/A |
IN3321 |
|
001 |
Department set ID: SHARE |
Department ID: 534 |
N/A |
IN7894 |
|
001 |
Department set ID: USA |
Department ID: OKL |
N/A |
US8390 |
If you used two security access types, for example Job Location (002) and Job Department Tree, SJT_PERSON looks like this:
|
SCRTY_TYPE_CD |
SCRTY_KEY1 |
SCRTY_KEY2 |
SCRTY_KEY3 |
EMPLID |
|---|---|---|---|---|
|
001 |
Department set ID: SHARE |
Department ID: 123 |
N/A |
IN3321 |
|
002 |
Location business unit: FRA01 |
Location code: PAR |
N/A |
IN3321 |
|
001 |
Department set ID: SHARE |
Department ID: 534 |
N/A |
IN7894 |
|
002 |
Location business unit: AUS01 |
Location code: SYD |
N/A |
IN7894 |
|
001 |
Department set ID: USA |
Department ID: OKL |
N/A |
US8390 |
|
002 |
Location business unit: USA |
Location code: KSC |
N/A |
US8390 |
Note: Locations and departments do not need three key fields to uniquely identify them so the third security key field isn't necessary for this example.
When you first enable a security access type, load the transaction data into security join tables using the SJT Refresh process. After the initial load, the system updates the tables using SavePostChange PeopleCode when you make a change to the transaction security data in the transaction components. You can also capture any changes the PeopleCode misses by running the SJT Refresh process as needed or the Nightly Refresh process.
Note: The SavePostChange PeopleCode on the transaction component subpage SCRTY_SJT_SBP updates the security join tables.
This graphic illustrates how the transaction security join tables are kept up to date, as described above:
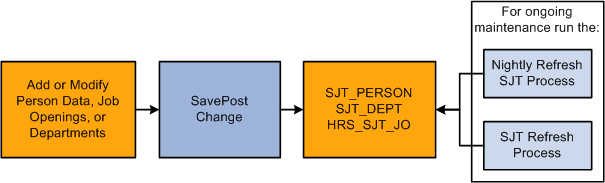
User Security Join Tables
The user security join tables store the user security data required to determine users' data permission. The security join tables store one row of data for each unique combination of key fields.
There are two user security join tables:
|
User Security Join Table |
Description |
Stores Data From: |
Key Fields |
|---|---|---|---|
|
SJT_CLASS_ALL |
Contains the data permission information for all the permission lists that are given data access on the Security by Dept Tree page or Security by Permission List page. |
|
CLASSID SCRTY_SET_CD SCRTY_TYPE_CD SCRTY_KEY1 SCRTY_KEY2 SCRTY_KEY3 |
|
SJT_OPR_CLS |
Contains the user IDs of people with data permission and the permission lists with data permission that are assigned to them. |
|
OPRID CLASSID |
In addition to the security access type field and security key fields, the user security join tables store the following fields:
SCRTY_SET_CD (security set code)
A security set is a set of data secured in HCM. For example, PPLJOB is the security set for the data of people with jobs and DEPT is the security set for the department data. Each security set has security access types.
OPRID
The user's user ID.
CLASSID
The ID of the role-based or row security permission list.
Note: The security join tables store row security permission lists (ROWSECCLASS) as CLASSID permission lists but identify them using a row security flag.
The permission list data in SJT_CLASS_ALL comes from two sources:
SCRTY_TBL_DEPT
When you add tree-based data permission to a permission list, you use the Security by Dept Tree page and the system saves the permission list information to the SCRTY_TBL_DEPT record.
SJT_CLASS
When you add non-tree based data permission to a permission list, you use the Security by Permission List page and the system saves the permission list information to the SJT_CLASS record.
For example, if you are securing the data of people with jobs using the security access type Job Department Tree (001), the key fields of the SCRTY_TBL_DEPT table look like this:
|
ROWSECCLASS |
SET ID |
DEPTID |
|---|---|---|
|
TRAIN |
Department set ID: SHARE |
Department ID: 123 |
|
PAY1 |
Department set ID: SHARE |
Department ID: 534 |
|
PAY2 |
Department set ID: USA |
Department ID: OKL |
To load the data from the SCRTY_TBL_DEPT table, you need to run the Refresh SJT_CLASS_ALL process. In SJT_CLASS_ALL, the Refresh SJT_CLASS_ALL process:
Creates a row of data for each enabled, tree-based security access type (and it's security set) with the data permission you set up on the Security by Dept Tree page.
For example, if you enable security access type 012 (RS Dept Id) and security access type 001 (Job Department Tree) and grant the row security permission list TRAIN data permission to department 123, the process will create a row for each security access type and the permission will have access to people with jobs in department 123 and job openings in department 123.
Saves the row security permission list as a CLASSID permission list.
Saves the department set ID as SCRTY_KEY1 and the department ID as SCRTY_KEY2.
If you are securing the data of people with jobs using the security access type Job Location (002), the key fields of the security join table SJT_CLASS look like this:
|
CLASSID |
SCRTY_SET_CD |
SCRTY_TYPE_CD |
SCRTY_KEY1 |
SCRTY_KEY2 |
SCRTY_KEY3 |
|---|---|---|---|---|---|
|
TRAIN |
PPLJOB |
002 |
Location business unit: FRA01 |
Location code: PAR |
N/A |
|
PAY1 |
PPLJOB |
002 |
Location business unit: AUS01 |
Location code: SYD |
N/A |
|
PAY2 |
PPLJOB |
002 |
Location business unit: USA |
Location code: KSC |
N/A |
When you save your changes on the Security by Permission List page, SavePostChange PeopleCode automatically updates the data to the security join table SJT_CLASS_ALL.
If you are using both security access types, SJT_CLASS_ALL looks like this after you have run the Refresh SJT_CLASS_ALL process and the PeopleCode has updated it:
|
CLASSID |
SCRTY_SET_CD |
SCRTY_TYPE_CD |
SCRTY_KEY1 |
SCRTY_KEY2 |
SCRTY_KEY3 |
|---|---|---|---|---|---|
|
TRAIN |
PPLJOB |
001 |
Department set ID: SHARE |
Department ID: 123 |
N/A |
|
TRAIN |
PPLJOB |
002 |
Location business unit: FRA01 |
Location code: PAR |
N/A |
|
PAY1 |
PPLJOB |
001 |
Department set ID: SHARE |
Department ID: 534 |
N/A |
|
PAY1 |
PPLJOB |
002 |
Location business unit: AUS01 |
Location code: SYD |
N/A |
|
PAY2 |
PPLJOB |
001 |
Department set ID: USA |
Department ID: OKL |
N/A |
|
PAY2 |
PPLJOB |
002 |
Location business unit: USA |
Location code: KSC |
N/A |
This graphic illustrates how the permission list user security join tables are kept up to date, as previously described:
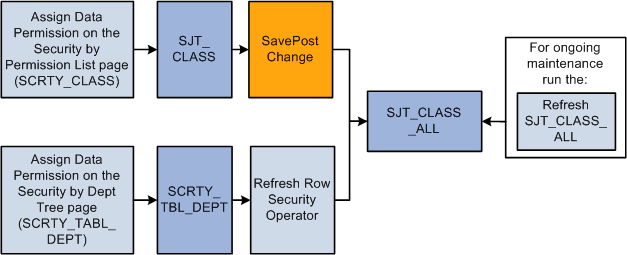
See Refresh SJT_CLASS_ALL Page.
The security join table SJT_OPR_CLS stores the relationship between User IDs and permission lists with data permission. The data in SJT_OPR_CLS comes from three sources:
PSOPRDEFN
This record contains the relationship between the User ID and row security permission list from the User Profile - General page.
PSROLEUSER
This record contains the relationship between the User IDs and roles from the User Profile - Roles page.
PSROLECLASS
This record contains the relationship between roles and permission lists from the Roles - Permission Lists page.
To update SJT_OPR_CLS with the data from PSOPRDEFN, PSROLECLASS, and PSROLEUSER, run the Refresh SJT_OPR_CLS process whenever you add a permission list with data security to a user profile (either by adding a row security permission list on the User Profile - General page, by adding a role-based permission list with data permission to a user-assigned role on the Roles - Permission Lists page, adding a role with data permission on the User Profile - Roles page, or by creating a new user profile by copying an existing one) or delete one from a user profile.
This graphic illustrates this process of when to update the user profile security join table:
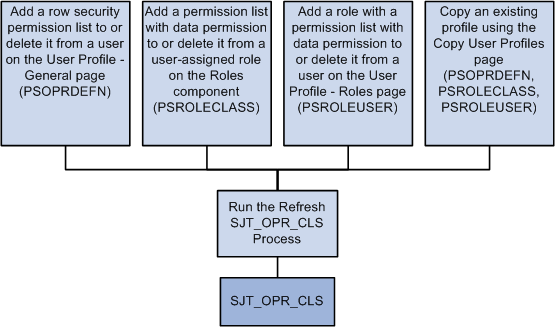
Note: You can enable the USER_PROFILE message and the local subscription HCM_Refresh_SJT_OPR_CLS and the ROLE_MAINT message and the local subscription HCM_Role_Refresh_SJT_OPR_CLS to automatically update SJT_OPR_CLS. PeopleSoft does not deliver the system with these messages enabled.
The Refresh SJT_OPR_CLS process loads the OPRID and ROWSECCLASS values from PSOPRDEFN directly into SJT_OPR_CLS, saving the row security permission list as CLASSID.
To establish the relationship between user profiles and role-based permission lists, the process first loads the OPRID and ROLENAME from PSROLEUSER and the ROLENAME and CLASSID from PSROLECLASS into a temporary table (ROLEUSER_ROLECLASS) and then loads the OPRID and CLASSID, and the relationship between them, into SJT_OPR_CLS.
This diagram illustrates the data stored in SJT_OPR_CLS and their source as described above:
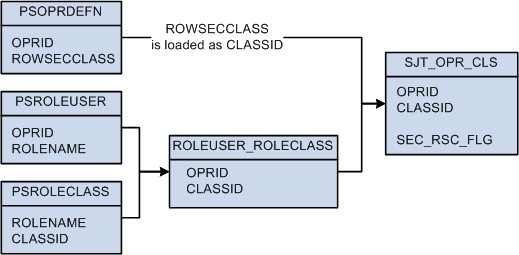
Note: The SEC_RSC_FLG field indicates if the CLASSID was originally a ROWSECCLASS permission list by flagging it with a value of Y.
A security set is a grouping of data that is being secured. The sets differ by the origin of the transaction security data. For example, people of interest without jobs have a separate security set from people with jobs because the transaction data used to secure them does not come from the JOB record, but from the PER_POI_SCRTY record.
PeopleSoft delivers the following five security sets:
|
Security Set |
Description |
Security Join Table Storing Data |
|---|---|---|
|
PPLJOB |
People with Jobs Includes the data of any person who has a JOB record and all the associated data for that person. |
SJT_PERSON |
|
PPLUSF |
People with Jobs for United States Federal Government Includes the data of any person who has a GVT_JOB record and all the associated data for that person. |
SJT_PERSON_USF |
|
PPLPOI |
People of interest without jobs Includes the data of any person who does not have a JOB record and all the associated data for that person. |
SJT_PERSON |
|
DEPT |
Departments Includes department budgets and positions. |
SJT_DEPT |
|
RSOPN |
Job Openings Includes the data of job openings, including the data of applicants associated with a job opening. |
HRS_SJT_JO |
|
GPSPOST |
German Public Sector Post Management |
GPS_PM_CFG_SJT |
|
TBHTMPL |
Template Based Hire |
HR_TBH_CFG_SJT |
Note: PeopleSoft has delivered all the security sets you are likely to need. If you add new sets, it is considered a customization.
Security access types are ways of securing the data within a security set. Each security set has a number of security access types that you can choose to enable. Among other things, security access types determine:
The security transaction data.
If there is data security for future-dated rows.
If the access type uses a department security tree.
Note: You can only set up department hierarchies on security trees and you can only grant security access by department tree to row security permission lists.
Security access types that don't use a department security tree do not have a hierarchical structure and require that you list each field value individually for each permission list.
The following table lists the security access types by security set:
|
Security Set |
Security Access Types |
|---|---|
|
PPLJOB |
|
|
PPLUSF |
|
|
PPLPOI |
|
|
DEPT |
|
|
RSOPN |
|
|
GPSPOST |
GPS Post Management (037) |
|
TBHTMPL |
|
Note: PeopleSoft has delivered all the security access types you are likely to need. You can add new types but it requires a very good knowledge of the application and of SQL.
Security administrators can only assign data permission using the security access types that you enable.
Enabling and Using Multiple Security Access Types
When you grant a permission list access to data in a security set using more than one security access type the security access creates a union, not a join or an intersect, with the two types. For example, if you enable the Job Company and Job Business Unit security access types for the PPLJOB security set and grant a permission list access to people in company A and people in business unit B, users with the permission list can access people in company A or people in business unit B; their access is not restricted to people in both business unit B and company C.
Note: See the security technical brief posted on My Oracle Support for information about creating security access types that join transaction fields to secure data.
When you set up HCM data permission security you will follow this process flow, which is detailed below:
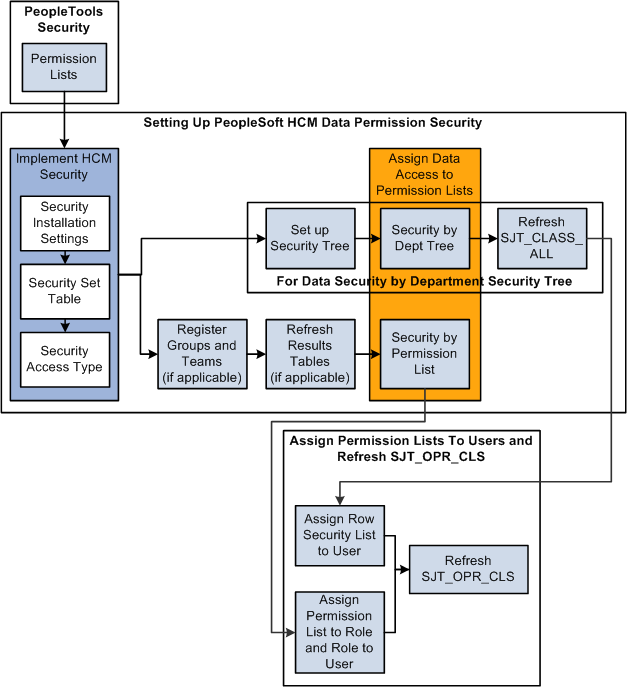
To set up HCM data permission:
Set up permission lists in the PeopleTools pages.
Set the security installation settings on the Security Installation Settings component.
Review security sets on the Security Set Table component.
Enable security access types on the Security Access Type component.
Assign data permission to permission lists:
If you are using security tree-based security access types, set up a security tree, assign data permission on the Security by Dept Tree component, and refresh SJT_CLASS_ALL.
If you are using non-tree based security access types, register any group IDs or matrix teams, if any, refresh the Results tables for the group IDs and teams, if applicable, then assign data permission on the Security by Permission List component.
Assign permission lists to users (by way of roles if you are using role-based permission lists or directly to the user profile if you are using row security permission lists).
Refresh SJT_OPR_CLS.
Grant the following security to these permission lists:
|
Permission List |
Page |
Security Access Type |
Security Value |
|---|---|---|---|
|
JobByDept |
Security by Dept Tree page |
Job Department Tree (001) |
Department 10100 (You must select set ID SHARE as the first key) |
|
JobByLoc |
Security by Permission List page |
Job Location (002) |
Location UK1 (You must select business unit GBR01 as the first key) |
|
MyJobs |
Security by Dept Tree page |
Job Department Tree (001) |
Department 11000 (set ID SHARE ) |
|
Security by Permission List page |
Job Location (002) |
Location USA (Business unit GBL01) |
Grant the permission lists to the following roles:
|
Role |
Permission List |
Outcome |
|---|---|---|
|
Role 1 |
JobByDept |
Role 1 has no access because tree–based department security (security access type 001) does not work with roles. |
|
Role 2 |
JobByLoc |
Has access to people with jobs in location UK1. |
|
Role 3 |
MyJobs |
Has access to people with jobs in location USA. Does not have security access to department 11000. |
Grant the following row security permission lists and roles to users:
|
User ID |
Row Security Permission List |
Role |
Has Access to People with Jobs In: |
|---|---|---|---|
|
User A |
JobByDept |
Department 10100. |
|
|
User B |
JobByDept |
Role 2 |
Department 10100 Location UK1. |
|
User C |
Role 2 |
Location UK1. |
|
|
User D |
Role 3 |
Location USA |
|
|
User E |
MyJobs |
Department 11000 Location USA. |
|
|
User F |
Role 1 |
Has no access. |
|
|
User G |
JobByDept |
Role 2 Role 3 |
Department 10100 Location UK1 Location USA. |