Setting Up MCF Email Using Azure
You can set up MCF inbound and outbound emails using OAuth2 authentication through Azure using the Create OAuth2 Service Apps page.
To create your own OAuth2 service application or open an existing application, open the Create OAuth2 Service Apps page using this navigation path:
Navigation:
.
This example illustrates the fields and controls on the Example to set up MCF Emails using OAuth2 Authentication with Azure.
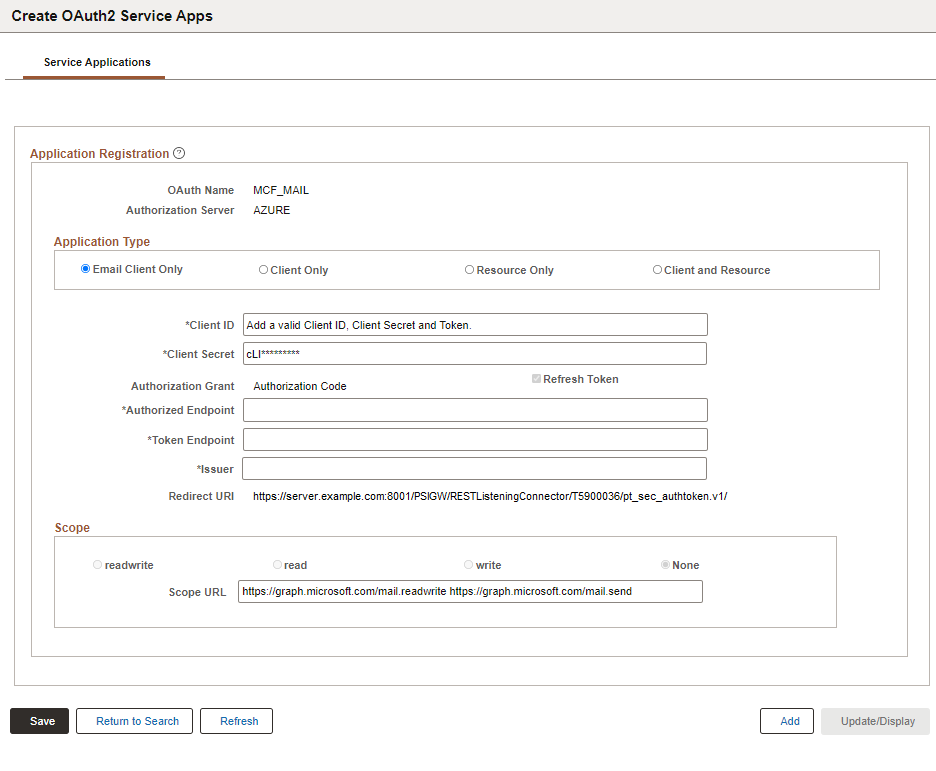
Example
This example shows the suggested values to be used for MCF emails:
Field or Control |
Description |
|---|---|
Application Type |
Select Email Client. |
Client ID |
Enter Azure application client ID. |
Client Secret |
Enter Azure application secret. |
Authorized Endpoint |
https://login.microsoftonline.com/<tenant ID>/oauth2/v2.0/authorize |
Token Endpoint |
https://login.microsoftonline.com/<tenant ID>/oauth2/v2.0/token |
Issuer |
https://login.microsoftonline.com |
Scope |
For email configurations, scope is set to None and grayed-out. |
Scope URL |
For email configurations, this defaults to https://graph.microsoft.com/mail.readwrite. |
Refresh Token |
This option is selected and grayed-out for email configurations. |
For more information on OAuth2 support for non-IDCS service providers, see Understanding OAuth 2.0.
There are several SMTP parameters that you must modify for OAuth configuration. See SMTP Settings.
For more information on certificates for SSL communication, see How To Configure SMTP SSL on Application Servers and Process Schedulers on My Oracle Support (Doc ID 1612188.1). For more information on setting up client certificate authentication, see How to Setup SMTP Client Certificate Authentication in PeopleSoft (Doc ID 2876697.1).