Process Scheduler Service Operation Security
This section provides an overview of Process Scheduler web service security.
The service operations for PROCESSREQUEST service follow the same user-based security as an online user. All Process Scheduler service operations require a user ID and password that must be digitally encrypted. Based on the user ID, the request is validated based on the request type.
Process Request
Security is defined for a process in the process definition. Security can be controlled by access to the component containing the run control and by process security group. The user who is requesting this web service operation can schedule the processes only if the user is authorized to submit the request.
This diagram shows the security process flow to schedule a process request:
This example illustrates the fields and controls on the Schedule process request security flow.
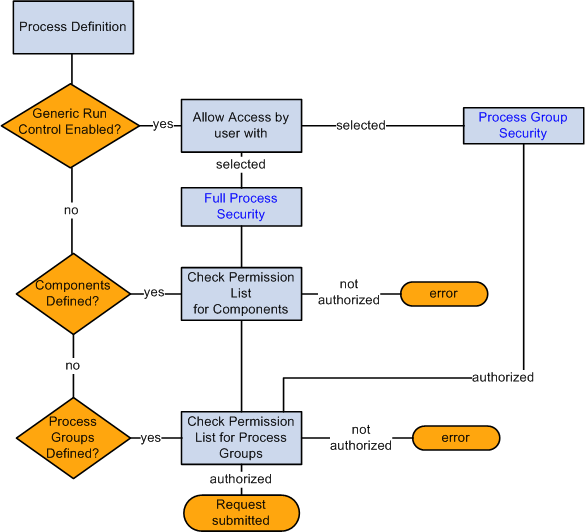
In the preceding diagram, the user submits the PRCS_SCHEDULE service operation, which includes a SOAP header identifying the user. The process scheduler validates the user by checking the security defined in the process definition:
If the process definition has Enable Generic Prompting on the Run Control Parameters page, the value forAllow Access by user with is used to validate permissions. If the generic run control is not enabled, the process scheduler will use the process security defined on the Process Definition Options page.
Full Process Security: The user must have permission for both component and process group.
Process Group Security: The user must have access to the process security group.
On the Process Definition Options page, the process may contain both components and process groups. If components are included, the user must have security access to at least one of the components.
The user must have security access to the process group.
Monitor Request
User’s access to process request via process monitor is determined by the process profile permission assigned to the person who submitted the request. In the process profile, options are available to restrict other users from viewing and updating process requests run by the owner (current user).
The options available are:
Owner: Only the user who submits the process can see or update the process request from process monitor.
All: All users can see or update the process request from the process monitor.
None: No user, including the owner, can view or update the process request from process monitor.
Note: User IDs that contain the role ProcessSchedulerAdmin can monitor all processes.
See Setting Up PeopleSoft Process Scheduler Privileges and Profiles.
Retrieve Reports
User’s access to retrieve reports is determined by the distribution in the report request. When a report request is submitted, you can specify the report distribution by users or roles. If the request does not contain distribution informations, the distribution defined in the Process definition is used.
Note: User IDs that contain the role ProcessSchedulerAdmin or ReportDistAdmin can retrieve all reports.