Administering Encryption Profiles
Access the Administer Encryption Profile page ().
The fields and controls on the page vary depending upon whether you are creating a new profile or modifying an existing profile, and depending upon the requirements of the profile components.
Access the Administer Encryption Profile page and select an existing profile and algorithm chain from the search page.
This example illustrates the fields and controls on the Administer Encryption Profile page for an existing profile (1 of 3). You can find definitions for the fields and controls later on this page.
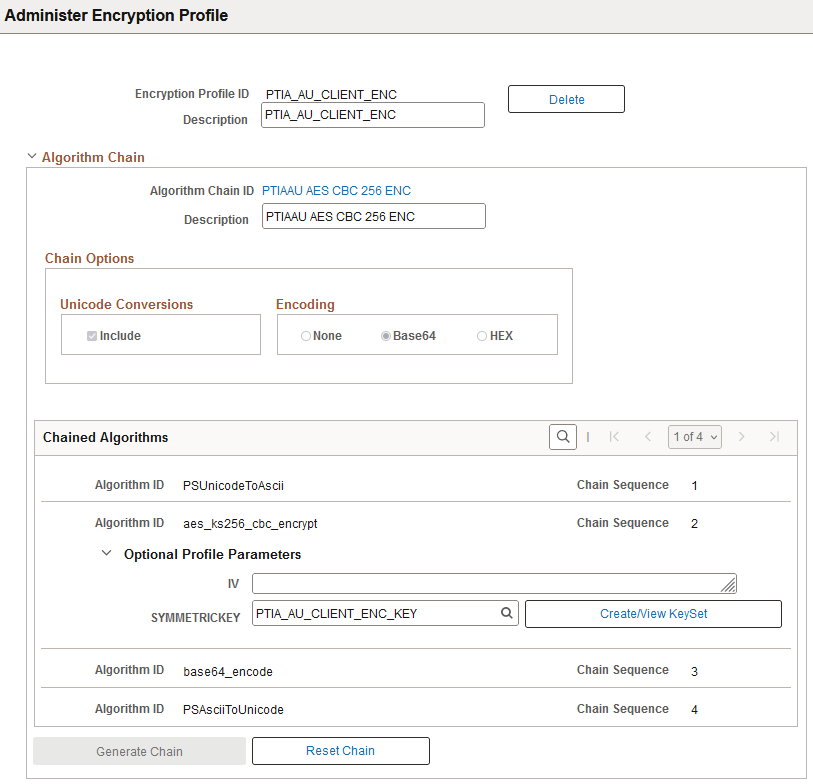
This example illustrates the fields and controls on the Administer Encryption Profile page for an existing profile (2 of 3). You can find definitions for the fields and controls later on this page.
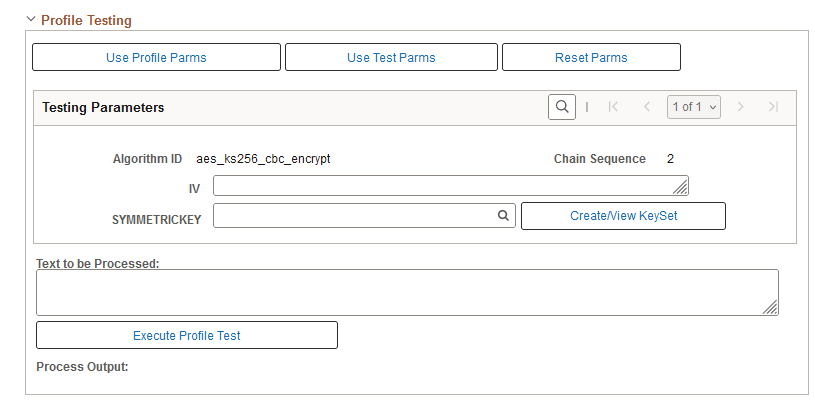
This example illustrates the fields and controls on the Administer Encryption Profile page for an existing profile (3 of 3). You can find definitions for the fields and controls later on this page.
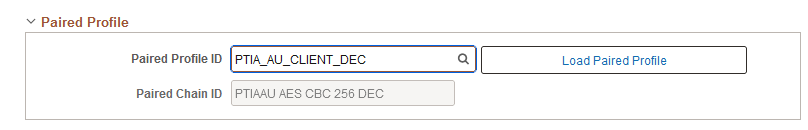
Configuring Algorithm Chains
When you access the Administer Encryption Profile page for an existing profile, the page displays information about the selected profile and algorithm chain.
|
Field or Control |
Description |
|---|---|
|
Encryption Profile ID |
If the profile is locked, it is labeled Profile Locked. To view or change the locked status, see Managing Encryption Profile Locks. |
|
Algorithm Chain ID |
Select the link to go to the Algorithm Chain page. See Defining Algorithm Chains. If the algorithm chain is being used only by other unlocked profiles, it is labeled Chain in Use. If the algorithm chain is being used by at least one locked profile, it is labeled Chain Locked. |
|
The Unicode Conversions and Encoding options are not enabled for existing profiles. The descriptions are included later in this section. See Defining a New Encryption Profile and New Algorithm Chain. |
|
Delete |
Click to delete the profile and any profile parameters. The Delete button is not available if the profile is locked. Profiles are
automatically locked when they are opened through the
PeopleCode Crypt Object Open API (without optional testing
parameter set to "True"). See Open.
After clicking Delete and accepting the confirmation message, confirm whether to also delete the chain. The message asking you to delete the chain appears for chains that are not locked or in use by another profile. |
|
Chained Algorithms |
The grid displays the chain sequence for the selected Algorithm ID. Each algorithm in the chain appears in order, in its own row with its algorithm ID and chain sequence number. If there are associated parameters, you see an expandable Optional Profile Parameters section. |
|
Optional Profile Parameters |
Enter any optional parameters for the algorithm. You will only be allowed to enter parameters that are valid for the loaded algorithm. |
|
Generate Chain |
This option is enabled after you reset the chain. Click to display the chain sequence for the selected Algorithm ID. |
|
Reset Chain |
Click this option to remove the ASCII and UNICODE related algorithms and leave only the Algorithm that was originally entered before clicking Generate Chain. This option is not enabled if the algorithm chain has the Chain in Use or Chain Locked label. |
Testing Encryption Profiles
Use the Profile Testing section to:
Ensure that the encryption profiles produce the expected results.
Determine the character length of the encrypted value.
Important! When planning to store encrypted data in fields on a table, you must consider that the length of the encrypted value is often longer than the unencrypted value.
|
Field or Control |
Description |
|---|---|
|
Use Profile Parms |
This option is enabled if there are Optional Profile Parameters specified in the Chained Algorithm section. Click Use Profile Parms to load any profile parameters into this grid. If there are other parameters that were not specified in the Optional Profile Parameters section, you must add them manually. |
|
Use Test Parms |
This option is described in Using Test Parameters. |
|
Reset Parms |
Clear the Testing Parameter fields. |
|
Create/View Keyset |
This option is described in Using Create/View Keyset. |
|
Testing Parameters |
Enter the required and optional (if desired) parameters for the algorithm. |
|
Text to be Processed |
Enter sample text as clear text or encrypted value (depending on the Profile expected input). |
|
Execute Profile Test |
Click to run the test with the specified parameters. |
|
Process Output |
Displays the result of the test. |
You can use this page to test decryption as well. You can also test complementary pairs of profiles — one to encrypt, and the other to decrypt. By copying the result of the encryption profile test and pasting it as input to the decryption profile test, you can determine whether the text you get out is the same as the text you put in.
Using Test Parameters
Click the Use Test Parms option to load a test-only set of validated test values for all testing parameters. The system generates test parameters that meet all documented requirements and restrictions.
|
Parameter |
Parameter Value |
|---|---|
|
IV |
Generated correct length random HEX value prepended with 0x. |
|
SYMMETRICKEY SECRETKEY |
Generated correct length fixed HEX value prepended with 0x. |
|
SIGNERCERT SIGNERPRIVATEKEY RECIPIENTPRIVATEKEY RECIPEINTCERT RECIPIENT |
Pre-defined self-signed Key/Certs stored in PeopleCode variables within the Component. Signer and Recipient use different values. |
|
RECIPIENTPKPASSPHRASE SIGNERPKPASSPHRASE |
peoplesoft (this was the value used to generate the keys/certs) |
|
SYMMETRIC_ALGORITHM |
aes_ks256_cbc_encrypt |
|
AAD |
Additional Authentication Data (TESTING) |
|
SIGNATURE AUTHTAG |
Populated from result of testing Paired Profile. |
|
Test keyset entry names |
OPRID + Parameter Name + counter |
Using Create/View Keyset
The Create/View Keyset option is enabled for parameters that must be stored in the Keyset table, and for unknown parameters. Select this option to display the Algorithm Keyset page.
The Key Text field displays the value for existing Keysets.
If there is no existing Keyset, enter the value in the Key Text field. The algorithm in this example, aes_ks256_cbc_encrypt, only allows manually entered key text.
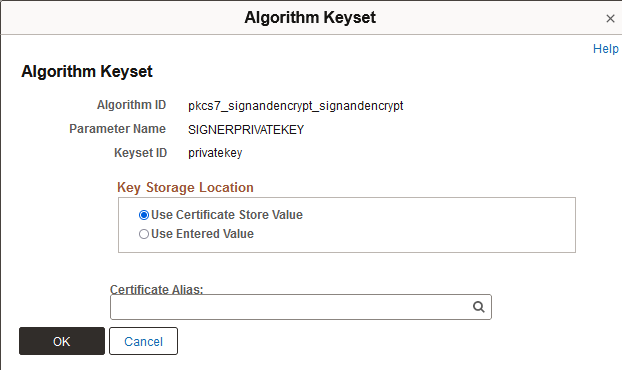
This example illustrates the fields and controls on the Algorithm Keyset page.
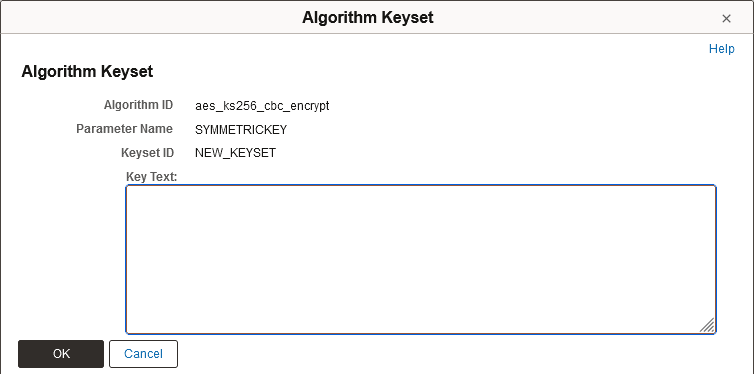
The algorithm in this example, pkcs7_signandencrypt_signandencrypt, allows you to select a digital certificate.
This example illustrates the fields and controls on the Algorithm Keyset page with the Key Storage Location group box.
Working With Paired Profiles
The Paired Profile section appears only for profiles of types encrypt, decrypt, sign, or verify. Select a profile to review or test with any current test parameters or results.
|
Field or Control |
Description |
|---|---|
|
Paired Profile ID |
Select an existing Profile ID that is known to be compatible with the profile currently loaded, or enter a non-existing profile name in order to create a paired profile. |
|
Paired Chain ID |
Select an algorithm chain or enter a name to create a new chain with values that are a correct inversion of the original Profile. |
|
Create Paired Profile |
This option appears after you select a Paired Profile ID and Paired Chain ID. Click this option to create the paired profile. |
|
Load Paired Profile |
Load the paired profile into the current page for review and testing. If the profile that was used to create the paired profile was tested the system transfers any parameters or test results to the Profile Testing group box. You can then test the compatibility of the paired profile with the original profile. |
Before defining a new encryption profile with a new algorithm chain, you should decide which algorithm you want to use.
To define a new encryption profile and new algorithm chain:
Select .
On the search page, enter a new Encryption Profile ID and new Algorithm Chain ID.
(Optional) Enter descriptions for the profile and chain.
Specify the chain options.
Enter desired algorithms.
Generate the chain.
Supply Optional Profile Parameters if desired.
When you click Save, the Testing and Paired Profile group boxes appear.
The page now functions the same as it does when you edit or update mode an existing encryption profile.
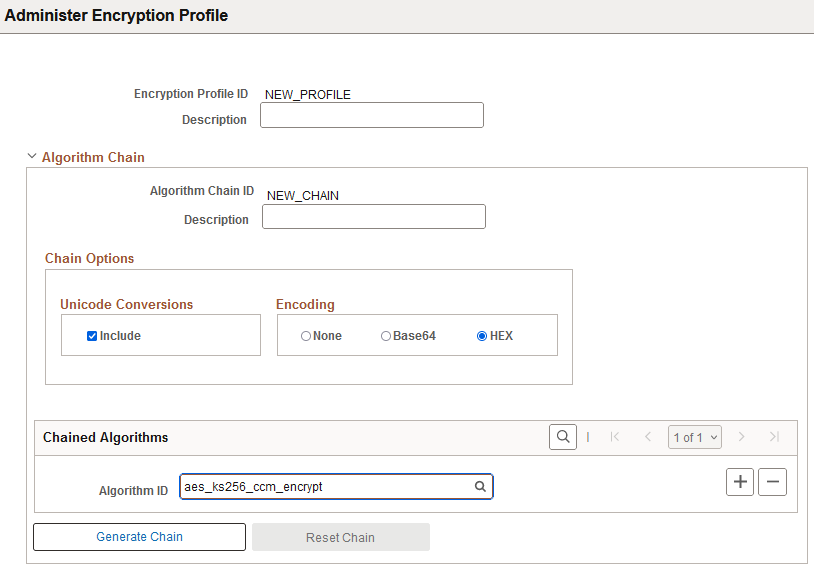
This example illustrates the fields and controls on the Administer Encryption Profile page when creating a new profile and new algorithm chain.
|
Field or Control |
Description |
|---|---|
|
Unicode Conversions |
Select Include to create a chain with PSUnicodeToAscii as the first algorithm in the chain sequence and PSAsciiToUnicde as the last algorithm in the chain sequence. |
|
Encoding |
Note: In some cases the Encoding settings will be automatically overridden based on the first algorithm specified in the chained algorithms grid. For example, smime and pkcs7 will be forced to have None as the Encoding option. |
|
Chained Algorithms |
Select an Algorithm ID from the available list. Click the plus button (+) to add additional algorithms. |
|
Generate Chain |
The Generate Chain option appears after you select an Algorithm ID. When you click this option the chain sequence for the selected Algorithm ID is displayed. Each algorithm in the chain appears in order, in its own row with its algorithm ID and chain sequence number. If there are associated parameters for an algorithm, you see an expandable Optional Profile Parameters section. |
|
Optional Profile Parameters |
Enter any required parameters for the algorithm. You will only be allowed to enter parameters that are valid for the loaded algorithm. |
|
Reset Chain |
The Reset Chain button appears after you generate the chain. Click this button to remove the list of algorithms and select a different Algorithm ID. |