application.yaml
The conf folder will have application.yaml file which consists of application-level properties and data source connection details. The properties should be changed accordingly.
Server Port:
The server port# should be unique and unused by any other process in the system.
Server port number
server:
port: 6060
Database Details
The default database type in the application.yaml is Oracle, the other data base types supported are MSSQL, DB2 and should be changed accordingly.
Do not change the driver class.
Oracle
database:
type: Oracle
driverClass: oracle.jdbc.driver.OracleDriver
javax:
sql:
DataSource:
OIPADataSource:
dataSourceClassName: oracle.jdbc.pool.OracleDataSource
dataSource:
URL: jdbc:oracle:thin:@//hostname:port:databasename
user: username
password: password
MS SQL server
database:
type: SQLServer
driverClass: com.microsoft.sqlserver.jdbc.SQLServerDriver
javax:
sql:
DataSource:
OIPADataSource:
dataSourceClassName: com.microsoft.sqlserver.jdbc.SQLServerDataSource
dataSource:
URL: jdbc:sqlserver://hostname:port;databasename=databasename
user: username
password: password
Cors Section
For allow-origins property, set the Upgrade Utility Web Application hostname and port number (http://hostname:portnumber).
Cors Configuration
cors:
enabled: true
paths:
- path-pattern: '*'
allow-origins: ["http://hostname:portNumber"]
allow-methods: ["*"]
allow-credentials: true
Security Configuration
Upgradeutility supports basic authentication. The username and clear/encrypted password will be configured in application.yaml file.
To generate the encrypted password:
Navigate to the upgradeutility folder and provide the values for masterPassword and secretToEncrypt
Encrypted Password
syntax: java -jar <path-to-app-libs-dir>/helidon-config-encryption-{helidon-version}.jar aes masterPassword secretToEncrypt
example: java -jar libs/helidon-config-encryption-2.6.5.jar aes myMasterPasswordForEncryption qatester4
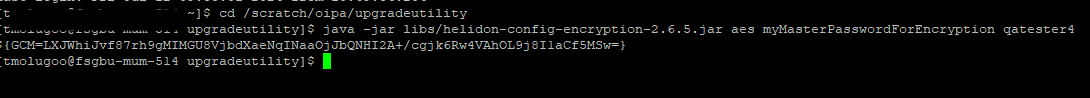
Add the username and encrypted password in the application.yaml as given below:
Security configuration
# Configuration of secured config
security.config:
# Set to true for production - if set to true, clear text passwords will cause failure require-encryption: true
username: qatester4
# The "master" password for AES decryption. For production, set this via system property or environment variable.
#aes.insecure-passphrase: "myMasterPasswordForEncryption"
aes-current:
#password in clear text - for non-prod environments, this is enough.
#password: "${CLEAR=qatester4}"
password: "${GCM=LXJWhiJvf87rh9gMIMGU8VjbdXaeNqINaaOjJbQNHI2A+/cgjk6Rw4VAhOL9j8I1aCf5MSw=}"
The username and original password that is qatester4/qatester4 should be used while login to the application.
