Configuring the Environment Management Hub
Before you can run the Environment Management hub, you must ensure that it's properly configured.
The hub issues automatic recrawl and revalidate commands to the agents, and it can be configured to accept automatic updates from Change Assistant. You configure the hub by setting appropriate parameters in its configuration file, which is located in PIA_HOME\webserv\domain\applications\peoplesoft\PSEMHUB\envmetadata\config\configuration.properties.
The following table describes the primary configuration.properties parameters for the hub:
|
Configuration Parameter |
Description |
Default Value |
|---|---|---|
|
recrawlinterval |
The interval, in hours, between two successive recrawl commands that have been issued to a peer. The server issues recrawl commands only to agents that are connected to the hub and have no pending messages in the queue. This configuration parameter is ignored by the agent. |
24 hours Note: A 0 value means that it will not recrawl. Recrawling includes a revalidating. |
|
revalidateinterval |
The maximum time, in hours, between two successive automatic revalidates that the hub issues. |
6 hours Note: A 0 value means that it will not revalidate. |
Hub Security Considerations
Environment Management framework supports HTTP and HTTPS connection.
If the EM Hub server uses the connection type HTTP or one-way SSL, then the client hostname or IP address need to be added to the allowedhost.properties file so that the client host is allowed to make a connection request.
The allowedhost.properties file is available in /webserv/peoplesoft/applications/peoplesoft/PSEMHUB.war/envmetadata/config/.
This example illustrates the sample allowedhost.properties file.
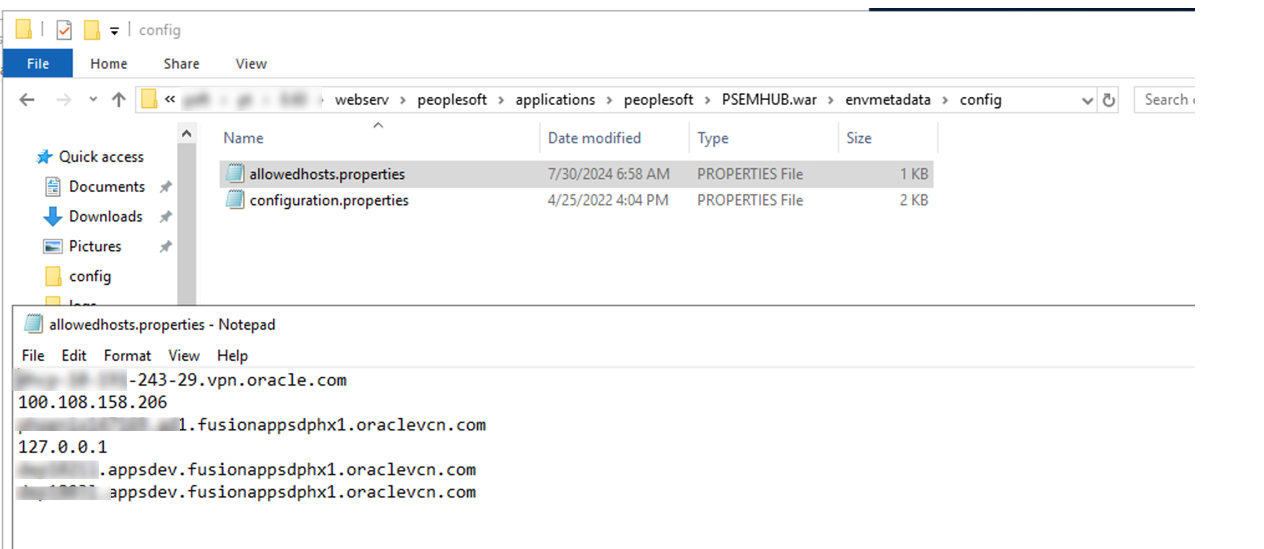
Note that the local host IP 127.0.0.1 is added by default to enable local PSEMAgent to ping EM Hub running on the same server. You can remove this IP if not required.
In the application log file, you will find logs that shows rejected connection requests from clients that are not added in the allowedhost.properties file. Use the information in the log file to resolve the connection issue.
Keystores and Truststores
A Keystore consists of a database containing a private key and an associated certificate, or an associated certificate chain. The certificate chain consists of the client certificate and one or more certification authority (CA) certificates.
A Truststore contains only the certificates trusted by the client (a “trust” store). These certificates are CA root certificates, that is, self-signed certificates.
For details on configuring keystore and truststore, refer Implementing WebLogic SSL Keys and Certificates.
For details on generating encrypted passwords, refer Generating a Unique Encryption Key