Siebel CRM 2018 integration with IDCS
The following figure describes the architecture for Siebel CRM 2018 integration with IDCS.
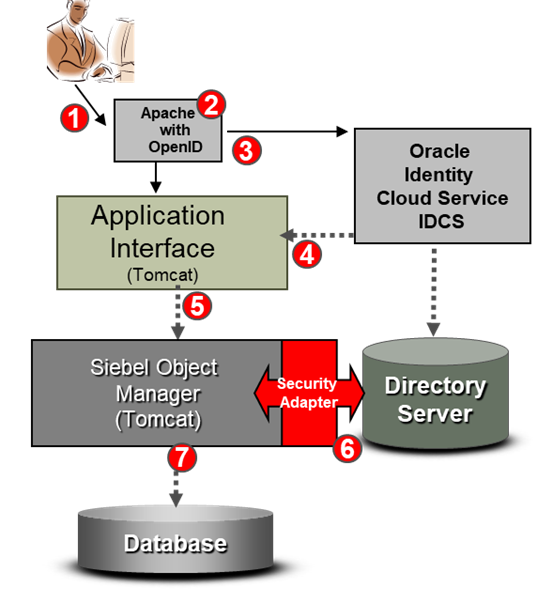
The Siebel CRM 2018 integration with IDCS architecture has this workflow:
- User tries to access Siebel URL protected by Apache HTTP Server 2.x.
- The Apache reverse proxy with Open ID module intercepts the request (HTTPS / HTTP).
- OpenID checks for the existence of a session cookie on the user’s computer. If a valid cookie exists, then the OpenID populates the header variable and the UserID is passed to Siebel.
- If no cookie exists, then the user is prompted for credentials using the IDCS form. The user enters the credentials which are passed to the Identity Cloud Service.
- If the credentials are authenticated, then the IDCS session cookie is set and the OpenID sets the header variable and redirects the request to Siebel.
- Siebel security adapter retrieves the database account and role information from the directory server.
- Siebel session is started with the appropriate responsibilities and shows the information based on user’s position.
Setting up the Apache Server
See 2364938.1 (Article ID) on My Oracle Support and follow all the instructions listed in the document. At the end of this setup make sure that navigating to the protected directory prompts the user to enter credentials from IDCS. After providing valid credentials in IDCS, the user can access the protected URL.
Siebel Object Manager and User Requirements
Two object managers, one with database authentication and one for configuring single sign-on (IDCS in our example) are needed for the setup process. As an example, enable Siebel CME Component Group and use ecommunications/enu for database authentication and eCommunicationsWireless/enu as IDCS authentication. Please note, URLs are case sensitive.
To enable single sign-on for an object manager, the object manager must be configured for LDAP authentication. See LDAP Configuration for Siebel for high level configuration for LDAP. Siebel uses LDAP client that is shipped with Oracle 12c database to talk to LDAP server.
Make sure that you have Siebel Administrator SADMIN privilege to access server administration screens. The environment should have GUESTCST configured with appropriate responsibility to give minimum number of views. GUESTCST should be configured in LDAP along with a database user account that can fetch information from user before the actual user logs into Siebel.
To Configure Apache HTTP Server Version 2.x as Reverse Proxy
- Modify apache24\conf\httpd.conf file for below changes. Configure Apache to
listen on SSL port 16660. Siebel server and Apache are configured on two
separate machines.
Listen 10.248.120.16:16660 - Enable reverse proxy by uncommenting below lines in httpd.conf
file.
LoadModule proxy_module modules/mod_proxy.so LoadModule proxy_html_module modules/mod_proxy_html.so LoadModule proxy_http_module modules/mod_proxy_http.so LoadModule proxy_http2_module modules/mod_proxy_http2.so - Enable
LoadModule xml2enc_module modules/mod_xml2enc.so - Add the following lines before the protected
directory.
ProxyPass "/siebel" "http://slc10yqi.us.oracle.com:16660/siebel" ProxyPassReverse "/siebel" "http://slc10yqi.us.oracle.com:16660/siebel" - The protected URL should be eCommunicationsWireless/enu URL instead of the
protected URL.
#<Location /eCommunicationsWireless_enu> <Location /siebel> AuthType openid-connect Require valid-user </Location> Working httpd.conf with IP 2018
To Configure Application Interface from Siebel Management Console (SMC)
- Log on to https://Siebel_Server:HTTPS_Port/siebel/smc
- Go to Profiles > Application Interface.
- Select the active profile in Application Interface Profiles.
- Select Applications from the second tab in the Applications area.
- Expand the eCommunicationsWireless (enu) tab.
- Expand the Enhanced Authentication tab.
- Select the Configure Web Single Sign-On (Web SSO)
check box and enter these values:
- TrustToken: IDCSSIEBEL (This value must match the value in the Security adapter of the Siebel Enterprise Profile).
- UserSpec: OIDC_CLAIM_sub (This is the HTTP header variable in which the OIDC passes the user name to Siebel).
To Configure Object Manager to Enable LDAP Security Adapter
-
Go to Administration > Server Configuration > Enterprises > Component Definition using eCommunications_enu object manager.
- Query for the Alias eCommWirelessObjMgr_enu.
-
Change the values of the following parameters in Component parameters.
- Security Adapter Mode (SecAdptMode): LDAP (old value DB)
- Security Adapter Name (LDAPSecAdpt): LDAPSecAdpt (old value DBSecAdpt)
- EnforceSSL: True
To Set up Security Adapter
- Go to Administration > Server Configuration > Enterprises > Profile Configuration using eCommunications_enu object manager.
- Query for the profile LDAP Security Adapter
- Set the following profile parameters:
-
Single Sign-On: True
- Trust Token: IDCSSIEBEL (this value must match the given value in the Application Interface file).
-
Effective with IP 17, Siebel ships with HTTPS enabled. You need to provide SSL certificates. For testing purpose, this configuration uses HTTP port for client to Apache to Siebel configuration. In a production environment, we recommend using the HTTPS protocol.
To Disable HTTPS
- See the topic Disabling HTTPS at this location: https://docs.oracle.com/cd/E88140_01/books/Secur/secur_dataencrypt001.htm#CIHDBIJF for testing purposes.
Modify swsm\applicationcontainer\webapps\siebel\WEB-INF\web.xml
<transport-guarantee>NONE</transport-guarantee> - Change the following object manager parameters for eCommunications Wireless
OM:
- SecureBrowse: False
- SecureLogin: False
- Stop and start the Tomcat server for Application Interface.
To Test the Configuration
Bounce the Siebel server, refresh application interface and start the httpd server whenever any changes are done to relevant components.