Recommended Network Topology
This topic describes the recommended topology for Siebel CRM deployments. The following figure shows the recommended placement of firewalls and related Siebel Enterprise Server components in a Siebel CRM deployment with internal and external users.
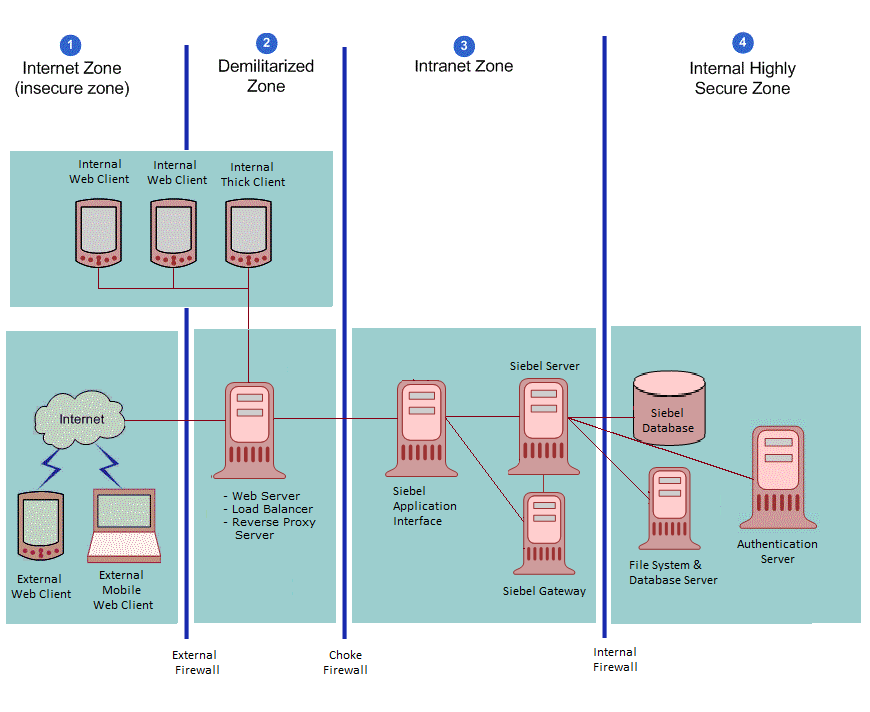
The Siebel network configuration for a secure deployment, as shown in this figure, is as follows:
Internet zone. External Siebel Web clients residing in the Internet zone access the Web server placed in the demilitarized zone through the external firewall.
Demilitarized zone. The Web server in this zone hosts a proxy server. The firewall keeps unauthorized users out of the protected network and the proxy server provides protection from various kinds of IP spoofing and routing attacks.
Intranet zone. The Application Interface is installed in the intranet zone. The Siebel Gateway and Siebel Servers are also placed in the intranet zone. Depending on the requirements and configured security adapter, the authentication mode can be one of the following: SSO/SAML, Database, LDAP, or Custom.
Note: The Application Interface accesses the migration database when it is deployed for migration.Internal highly secure zone. This zone contains the Siebel Database and File System, and the authentication server (a Lightweight Directory Access Protocol (LDAP) server). Limit access to this zone to authorized system administrators and database administrators.
The network configuration approach illustrated in this figure follows a defense-in-depth strategy by placing firewalls between the zones of control with only appropriate ports open. A secure channel is implemented using Transport Layer Security (TLS) between the external Web clients and the Web server to take care of security in the insecure Internet.