1 MSS Security Overview
This chapter provides an overview of Oracle Communications MetaSolv Solution (MSS) security.
Basic Security Considerations
The following principles are fundamental to using any application securely:
-
Keep software up to date. This includes the latest product release and any patches that apply to it.
-
Limit privileges as much as possible. Users should be given only the access necessary to perform their work. User privileges should be reviewed periodically to determine relevance to current work requirements.
-
Monitor system activity. Establish who should access which system components, how often they should be accessed, and who should monitor those components.
-
Install software securely. For example, use firewalls, secure protocols (such as SSL), and secure passwords. See "Performing a Secure MSS Installation" for more information.
-
Learn about and use MSS security features. See "Implementing MSS Security" for more information.
-
Use secure development practices. For example, take advantage of existing database security functionality instead of creating your own application security. See "Security Considerations for Developers" for more information.
-
Keep up to date on security information. Oracle regularly issues security-related patch updates and security alerts. You must install all security patches as soon as possible. See ”Critical Patch Updates and Security Alerts” on the Oracle website:
http://www.oracle.com/technetwork/topics/security/alerts-086861.html
Overview of MSS Security
Security for MSS focuses on a few key areas:
-
Limiting use of MSS and accessory applications to authorized users
-
Controlling access to functionality in the application with security windows and checkpoints
-
Protecting access to CORBA APIs, EJB APIs, and Web Service APIs
Understanding the MSS Environment
When planning your MSS implementation, consider the following:
-
Which resources need to be protected?
-
You must protect customer data.
-
You must protect internal data, such as proprietary source code.
-
You must protect system components from being disabled by external attacks or intentional system overloads.
-
-
Who are you protecting data from?
For example, you need to protect your subscribers' data from other subscribers, but someone in your organization might need to access that data to manage it. You can analyze your workflows to determine who needs access to the data; for example, possibly a system administrator can manage your system components without needing to access the system data.
-
What will happen if protections on a strategic resources fail?
In some cases, a fault in your security scheme is nothing more than an inconvenience. In other cases, a fault might cause great damage to you or your customers. Understanding the security ramifications of each resource will help you protect it properly.
Recommended Deployment Configurations
Oracle recommends installing MSS in a clustered redundant environment with the application tier isolated by firewalls, as shown in Figure 1-1.
Figure 1-1 Recommended MSS Deployment with Redundancy and Isolated Application Tier
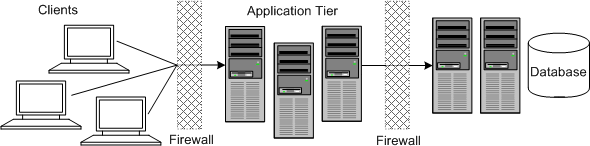
Description of ''Figure 1-1 Recommended MSS Deployment with Redundancy and Isolated Application Tier''
The database and application servers are protected from potential attacks by two layers of firewall. Both firewalls can be configured to block known illegal traffic types. The two layers of firewall provide intrusion containment. Although there are a greater number of components to secure, and more ports have to be opened to allow secure communication between the tiers, the attack surface is spread out.
Operating System Security
See the following documents for information about securing your operating system:
-
Windows Security Checklist on the Microsoft website
-
Guide to the Secure Configuration of Red Hat Enterprise Linux
-
Hardening Tips for the Red Hat Enterprise Linux
-
Oracle Solaris Security for System Administrators
Oracle Database Security
This section lists the MSS-specific security configurations for the Oracle Database.
For more information about securing Oracle Database, see Oracle Database Security Guide and Oracle Database Advanced Security Administrator's Guide.
Data Encryption
If your database connection is not configured to use data encryption, data is sent across the network in a format that is designed for fast transmission. Given some time and effort, unencrypted data can be intercepted and decoded.
It is also possible (but not recommended) to encrypt the MSS tablespace and schemas at the expense of system performance. Encrypting the schema and tablespace is not necessary, because the database is sufficiently secure without the encryption.
See Oracle Database Advanced Security Administrator's Guide for more information.
Secure Database Connections
Encrypting network data is a critical security measure that ensures that data traveling over the network is difficult to intercept and access. Secure network connections to the Oracle Database using the Oracle Advanced Security feature. You can configure the Oracle Database with either Network Data Encryption or SSL authentication, as both ensure that the data is secure while traveling over the network.
The Oracle Advanced Security feature also provides security against the following types of attacks:
-
Data modification attack, where an unauthorized party intercepts data in transit over the network, alters it, and transmits the altered data to the database.
-
Replay attack, where an unauthorized party repeatedly transmits entire sets of valid data.
Oracle WebLogic Server Security
See the discussion about securing WebLogic Server in Oracle Fusion Middleware Securing a Production Environment for Oracle WebLogic Server.
Specifically, consider the following security features:
-
SSL cipher suites and performance: Oracle strongly recommends not allow any NULL ciphers and to disable all anonymous ciphers and to also disable weak RC4 ciphers. Due to stronger cipher and MAC algorithms, in terms of performance AES (used for encryption) + SHA 1 (for hashes) is slower than RC4 + MD5. In an already secure environment, it might be acceptable to enable RC4 + MD5.
-
Enable Secure Auditing: This optional feature can collect, store, and distribute information about operating requests and the outcome of those requests.
-
Enable Host name verification: This feature helps to avoid man-in-the-middle attacks.
-
Enable FIPS-compliant (FIPS 140-2) crypto module for SSL implementation on the WebLogic Server instance: This feature complies with US Federal Government requirements.