57 Managing Shared Folders
This chapter describes the tasks that you use to administer Oracle Communications Messaging Server shared folders.
Shared Folders Overview
A shared folder is like any other mail folder except that users other than its owner can read, delete, or add messages to it, depending on the access rights they are granted. Messages can be added to shared folders by normal drag and drop, by Sieve filters, or by sending messages directly using the form: uid+folder@domain.
The following example shows the address for sending email to a private shared folder owned by carol.fanning@example.com called crafts_club:
carol.fanning+crafts_club@example.com
This example shows the address for sending email to a public shared folder called tennis:
public+tennis@example.com
Shared folders are useful for starting, sharing, and archiving an ongoing email conversation on a particular topic. For example, a group of software developers can create a shared folder for discussing development of a particular project called mosaic_voices. When a message is sent or dropped into the folder mosaic_voices, anyone who has permissions to access the shared folder (permissions can granted to individuals or groups) can open this mailbox and read the message.
Shared folders are displayed in user's mailbox tree under a folder called Shared Folders, as shown in Figure 57-1.
Figure 57-1 Example of Shared Mail Folder List as Seen from a Mail Client
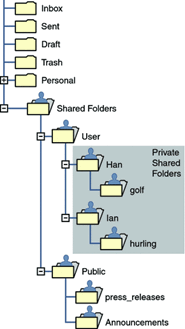
Description of ''Figure 57-1 Example of Shared Mail Folder List as Seen from a Mail Client''
There are two kinds of shared folders:
-
Private Shared Folder - A shared folder created and owned by a specific user with access rights granted to other users or groups. The owner can grant access rights using Convergence or other mail clients that support shared folder creation. The mail administrator can also grant access rights using the readership command. Private shared folders appear in the Shared Folders/User mail folder directory.
-
Public Shared Folder - A shared folder created by the mail administrator and not owned by a specific user. The mail administrator can grant access rights using the readership command. Public shared folders appear in the Shared Folders/Public mail folder directory.
For example, you might want a folder, such as public+software_dev@example.com for posting information about a special interest group inside the company. Interested employees would be granted access to this public folder.
Messaging Server allows folders to be shared among users of different backend message stores. See "Setting Up Distributed Shared Folders" for details.
See "Managing Shared Folders" for examples of creating shared folders and granting access rights.
Specifying Sharing Attributes for Private Shared Folders
A private shared folder is a normal folder, created by users in the same way that they create other folders. A folder becomes "shared" when its owner grants access rights to other users or groups. Methods to manage folder access include:
-
Many IMAP clients
-
Convergence web client
-
Oracle Communications Messaging Server "readership" command, for mail administrators
Table 57-1 explains the msconfig options that pertain to private shared folders.
Table 57-1 Disabling Quota Enforcement
| msconfig Option | Description | Default |
|---|---|---|
|
store.privatesharedfolders.restrictanyone |
If enabled (1), disallows regular users from setting the permission on private shared folders to anyone. |
0 |
|
store.privatesharedfolders.restrictdomain |
If enabled (1), disallows regular users sharing private folders to users outside of their domain. |
0 |
|
store.privatesharedfolders.shareflags |
If disabled (0), users of a shared folder have their own set of flags (for example, seen, deleted, and so on) for messages in that folder. If enabled (1), a single set of flags is shared between all users of each shared folder. |
0 |
To Create a Public Shared Folder
Public shared folders must be created by the mail administrator because they require access to the LDAP database as well as the "readership" and "mboxutil" commands.
To create a publich shared folder:
-
Set the userid for Public shared folders. The store.publicsharedfolders.user option specifies the userid to act as a container for all public shared folders (see "Shared Folders Overview"). Typically, this is simply public. The default is NULL (unset).
msconfig set store.publicsharedfolders.user public
-
Create an LDAP entry for that user. The uid must match that specified by store.publicsharedfolders.user, for example:
dn: cn=public,ou=people,o=example.com,o=ISP objectClass: person objectClass: organizationalPerson objectClass: inetOrgPerson objectClass: inetUser objectClass: ipUser objectClass: inetMailUser objectClass: inetLocalMailRecipient objectClass: nsManagedPerson objectClass: userPresenceProfile cn: public mail: public@example.com mailDeliveryOption: mailbox mailHost: manatee.example.org uid: public inetUserStatus: active mailUserStatus: active mailQuota: -1 mailMsgQuota: 100
-
Create folders within the public account by using the "mboxutil" command, for example:
mboxutil -c user/public/gardening
-
Use the "readership" command to grant rights to allow users to access the folder. For example, the following command gives everyone in the example.com domain lookup, read, and posting access to the public folder gardening:
readership -s user/public/gardening anyone@example.com lrp
The name anyone@domain is a special case to designate all users in the specified domain. It does not correspond to any user or group definition in LDAP. The name anyone without specifying a domain indicates anyone in any domain. The following command grants the user whose uid is kelly the same access rights as the owner of the folder:
readership -s user/public/gardening kelly@example.com lrswipcdan
For individual users, you only need to supply a domain name with hosted domains. Do not use a domain name if the user to whom access is being granted is in the default domain.
See the "readership" command for a list of the "ACL Rights Characters" and their meanings.
To Grant Folder Access Rights Based on Group Membership
In the previous examples, "ACL Rights Characters" have been granted to individual users or to the special case names anyone or anyone@<domain>. You can also grant rights based on group membership. Members of such a group are identified by having the aclGroupAddr attribute. For more information on the aclGroupAddr, see Schema Reference.
For example, a group called tennis@example.com has 25 members and the members have decided that they would like to create a shared folder to store all email going to this group address and to allow members of the group to access that shared folder.
The mail administrator uses the "readership" command to grant group access rights. A group name is distinguished from individual user names by the prefix "group=".
To grant folder access rights based on group membership:
-
Create the folder. In this example, the team decided to use a private shared folder. The user gregk could have created the folder by using a mail client, or the mail administrator could have created it by using the "mboxutil" command, for example:
mboxutil -c user/gregk/gardening
If the team were using a public shared folder, the mail administrator would have had to create it:
mboxutil -c user/public/gardening
-
Use the "readership" command to grant lookup, read, and posting access privileges to the group:
readership -s user/gregk/gardening group=tennis@example.com lrp
-
Assign group membership to the individual users. For the purpose of folder access control, group membership is determined by the aclGroupAddr attribute on the LDAP entry of the individual users. Add the attribute-value pair aclGroupAddr=<group-name> to the user entry of every member of the group, for example:
aclGroupAddr: tennis@example.com
To create group objects in LDAP, you could use the aclGroupAddr attribute as the basis for a dynamic group, for example:
memberURL: ldap:///o=example.com??sub?(&(aclGroupAddr=tennis@example.com)(objectclass=inetmailuser))
However, note that the LDAP group object with mail address tennis@example.com is not used for determining group membership for the purpose of shared folder access. What matters is that the "xxx" value in group=xxx on the readership command matches the value of the aclGroupAddr attribute on the user's LDAP object.
Also note that if you use the aclGroupAddr attribute as the criteria for a dynamic group, you should check to make sure that attribute is indexed properly for such lookups.
To Set or Change a Shared Folder's Access Control Rights
Users can set or change the access control for a shared folder by using Convergence. Administrators can set or change the access control for a shared folder using the "readership" command line utility. The command has the following form:
readership -s foldername identifier rights_chars
where foldername is the name of the folder for which you are setting rights, identifier is the person or group to whom you are assigning the rights, and rights_chars are the rights you are assigning. For the meaning of each character, see Table 57-3, "readership Options" for more information.
Note:
anyone is a special identifier. The access rights for anyone apply to all users. Similarly, the access rights for anyone@domain apply to all users in the same domain. For the identifier, only supply a domain name with hosted domains. Do not use a domain name if the folder is in the default domain.Shared Folder Examples
-
To assign everyone in the example domain to have lookup, read, and email marking (but not posting) access to the public folder called golftournament, type the following command:
readership -s user/public/golftournament anyone@example lwr
-
To assign the same access to everyone on the message store type the following command:
readership -s user/public/golftournament anyone lwr
-
To assign lookup, read, email marking, and posting rights to a group, type the following command:
readership -s user/public/golftournament group=golf@example.com lwrp
-
If you want to assign administrator and posting rights for this folder to an individual, jdoe, type the following command:
readership -s user/public/golftournament jdoe@example.com lwrpa
-
To deny an individual or group access to a public folder, prefix the userid with a dash. For example, to deny lookup, read, and write rights to jsmith, type the following command:
readership -s user/public/golftournament -jsmith@example.com lwr
-
To deny an individual or group an access right, prefix the ACL rights character with a dash. For example, to deny posting rights to jsmith, type the following command:
readership -s user/public/golftournament jsmith@example.com -p
-
To remove an individual or group access right setting from a folder, set it to an empty set. This is different from an ACL to deny access:
readership -s user/public/golftournament jsmith@example.com ""
Note:
Posting messages to a shared folder by using the uid+folder@domain address requires that the p (post) access right be used with the readership command. See "To Set or Change a Shared Folder's Access Control Rights" for more information.
Enabling or Disabling Listing of Shared Folders
Use the store.sharedfolders option to enable to disable listing of shared folders when responding to an IMAP LIST command. Setting the option to 0 disables it. The setting is enabled by default (set to 1). SELECT and LSUB commands are not affected by this option. The LSUB command returns every subscribed folder, including shared folders. Users can SELECT the shared folders they own or are subscribed to.
Setting Up Distributed Shared Folders
Normally, shared folders are only available to users on a particular message store. Messaging Server, however, enables you to create distributed shared folders that can be accessed across multiple message stores. That is, access rights to distributed shared folders can be granted to any users within the group of message stores. However, web mail clients do not support remote shared folders access. Users can list and subscribe to the folders, but they cannot view or alter the contents.
Distributed shared folders require the following:
-
Every message store userid must be unique across the group of message stores.
-
The directory data across the deployment must be identical.
The remote message stores (that is the message stores that do not hold the shared folder) must be configured as proxy servers by setting the configuration variables listed in Table 57-2.
Table 57-2 Variables for Configuring Distributed Shared Folders
| Name | Value | Data Format |
|---|---|---|
|
base.proxyserverlist |
Message store server list to list shared folders from |
space-separated strings |
|
base.proxyadmin |
Default store admin login name |
string |
|
base.proxyadminpass |
Default store admin password |
string |
|
proxy:hostname.imapadmin |
Store admin login name for a specific host if different from base.proxyadmin |
string |
|
proxy:hostname.imapadminpass |
Store admin password for a specific host if different from base.proxyadminpass |
string |
Setting Up Distributed Shared Folders-Example
Figure 57-2 shows a distributed folder example of three message store servers called StoreServer1, StoreServer2, and StoreServer3.
Figure 57-2 Distributed Shared Folders-Example
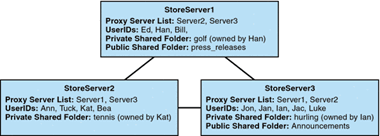
Description of ''Figure 57-2 Distributed Shared Folders-Example''
These servers are connected to each other as peer proxy message stores by setting the appropriate msconfig options. Each server has a private shared folder: golf (owned by Han), tennis (owned by Kat), and hurling (owned by Luke). In addition, there are two public shared folders called press_releases and Announcements. Users on any of the three servers can access any of these three shared folders.
The following example shows the ACLs for each server in this configuration.
Note:
The imcheck -d command is only valid for classic message store.$ StoreServer1 :> imcheck -d lright.db Ed: user/Han/golf Ian: user/Han/golf anyone: user/public/press_releases
$ StoreServer2 :> imcheck -d lright.db Jan: user/Kat/tennis Ann: user/Kat/tennis anyone: user/public+Announcements user/public+press_releases
$ StoreServer3 :> imcheck -d lright.db Tuck: user/Ian/hurling Ed: user/Ian/hurling Jac: user/Ian/hurling anyone: user/public/Announcements
Monitoring and Maintaining Shared Folder Data
The readership command-line utility enables you to monitor and maintain shared folder data which is held in the folder.db, peruser.db, and lright.db files. folder.db has a record for each folder that holds a copy of the ACLs. The peruser.db has an entry per user and mailbox that lists the various flags settings and the last date the user accessed any folders. The lright.db has a list of all the users and the shared folders for which they have lookup rights.
Table 57-3 shows the options for the readership command-line utility.
| Options | Description |
|---|---|
|
-d days |
Returns a report, per shared folder, of the number of users who have selected the folder within the specified days. |
|
-p months |
Removes data from the peruser.db for those users who have not selected their shared folders within the specified months. |
|
-l |
List the data in lright.db. |
|
-sfolder_identifier_rights |
Sets access rights for the specified folder. This updates the lright.db as well as the folder.db. |
Using the various options, you can perform the following functions:
To Monitor Shared Folder Usage
To find out how many users are actively accessing shared folders, use the following command:
readership -d days
where days is the number of days to check. Note that this option returns the number of active users, not a list of the active users.
Example: To find out the number of users who have selected shared folders within the last 30 days:
readership -d 30
To List Users and Their Shared Folders
To list users and the shared folders to which they have access, use the following command.
Note:
The imcheck -d command is only valid for classic message store.imcheck -d lright.db
Example output:
imcheck -d lright.db group=lee-staff@example.org: user/user2/lee-staff richb: user/golf user/user10/Drafts user/user2/lee-staff user/user10/Trash han1: user/public+hurling@example.org user/golf gregk: user/public+hurling@example.org user/heaving user/tennis
To Remove Inactive Users
If you want to remove inactive users (those who have not accessed shared and other folders in a specified time period), use the following commands:
-
This command writes the inactive mailboxes to a file:
mboxutil -o [-w file] [-t number_of_days]
-
This command removes the mailboxes in a given file:
mboxutil -d -f file
Example: Remove users who have not accessed folders for the past six months (180 days) using a file named inactive_users:
mboxutil -o -w inactive_users -t 180 mboxutil -d -f inactive_users
To Set Access Rights
You can assign access rights to a new public folder, or change access rights on a current public folder.
See "To Set or Change a Shared Folder's Access Control Rights" for an example of how to set access rights with this command