3 Securing Network Traffic
This chapter explains how to protect the traffic between Oracle Communications Services Gatekeeper and the web-based users and applications that it communicates with. This chapter starts by explaining how to protect all Services Gatekeeper implementations from malware and denial of service (DOS) attacks, and then provides information specific to API management features.
Understanding How to Secure Network Traffic
Securing network traffic between your Services Gatekeeper and the users and applications that connect to it over the Internet involves these general categories:
In addition, there are special considerations for API management users, and communication services. See these sections for details:
Configuring Network Traffic Security with ApiFirewallMBean
You configure network security traffic by performing the following general tasks:
-
Deciding which error message to return when a SOAP or REST message is rejected. The default error message is 400 Bad Request, which is the most descriptive. You set the error message by using the getErrorStatus attribute of ApiFirewallMBean. See the ”All Classes” section of Services Gatekeeper OAM Java API Reference for details.
-
Deciding whether to direct Services Gatekeeper to create an EDR and alarm for each firewall violation by using the CreateViolationEdrs attribute to ApiFirewallMBean. The attribute is boolean and the default value is yes.
The EDR is created with one of these statuses:
-
Reject - no further status is available.
-
Reject: json - An exception was thrown while parsing JSON.
-
Reject: size - The message was too big.
-
Reject: scheme - Protocol scheme was not allowed (for example, HTTP was used to access a HTTPS only API).
The new alarm number is 390000. For details see "390000: Request Rejected by API Firewall” in Services Gatekeeper Alarms Handling Guide.
This is an example CreateViolationEdrs EDR:
ServiceName = null Timestamp = 1473942471250 ContainerTransactionId = null ServerName = servername Class = oracle.ocsg.api_firewall.filter.GenericAPIFirewallFilter Method = doFilter Source = Exception HttpStatusCode = 400 Status = Reject: size Position = after Method = doFilter TransactionId = 67e7ed6c-26cc-4c07-b59c-bb36f40e502d State = API-FW Class = oracle.ocsg.api_firewall.filter.GenericAPIFirewallFilter HttpMethod = POST Timestamp = 1473942471250 Source = Exception URL = /weather-soap/1/weather ErrCat = API-FW ServerName = servername
-
-
Setting the maximum limits for error messages, including:
-
The maximum total size of a single message entity, such as a comment, by using the MaxItemValueLength attribute of ApiFirewallMBean.
-
The maximum size of an error message, excluding attachments, by using the getMaxMessageSize attribute of ApiFirewallMBean.
-
The maximum number of nested message elements allowed in a message by using the getMaxChildElementDepth attribute of ApiFirewallMBean.
-
The maximum number of unbounded elements (elements and attributes listed in the API schema as unbounded) a message can contain, by using the getMaxUnboundedItems attribute of ApiFirewallMBean.
Note:
The maximum size supported for any single message is 200 MB. -
-
(Optional) Creating a list of trusted APIs. Most of the ApiFirewall MBean security attributes filter messages that are potential security risks. This filtering process degrades performance slightly. To avoid this performance penalty, create a list of trusted APIs that are exempt from the filtering process by using the setApiConfigXml attribute of ApiFirewallMBean. See ”Creating a List of Trusted APIs Using ApiConfigXml” for details.
-
(Optional) creating a list of trusted IP addresses for REST-based communication. See "Protecting REST APIs with a White List of IP Addresses" for instructions.
You can change ApiFirewallMBean attributes from the Administration Console or by editing the MBean directly. For a description of the attributes and operations of the ApiFirewallMBean MBean, see the ”All Classes” section of Services Gatekeeper OAM Java API Reference.
Creating a List of Trusted APIs Using ApiConfigXml
You use the ApiConfigXml element of ApiFirewallMBean to create a ”white list” of well-known API URLs. Once created, traffic from those URLs passes into Services Gatekeeper without the standard network traffic security checks. This is more efficient but less secure. So be sure that the URLs you exempt from security checks really are trusted.
Example 3-1 shows the ApiConfigXml syntax:
Example 3-1 ApiConfigXml Schema Syntax
<?xml version="1.0" encoding="UTF-8"?>
<schema xmlns="http://www.w3.org/2001/XMLSchema"
targetNamespace="http://oracle/ocsg/api_firewall/management/xml"
xmlns:tns="http://oracle/ocsg/api_firewall/management/xml"
elementFormDefault="qualified">
<element name="baseApis">
<complexType>
<complexContent>
<extension base="tns:Apis">
</extension>
</complexContent>
</complexType>
</element>
<complexType name="Apis">
<sequence>
<element name="apis" type="tns:Api" minOccurs="0" maxOccurs="unbounded"></element>
</sequence>
</complexType>
<complexType name="Api">
<sequence>
<choice>
<element name="requestUrl" type="string"></element>
<element name="requestUrl_regex" type="string"></element>
</choice>
<element name="method" type="string" minOccurs="0" maxOccurs="unbounded"></element>
</sequence>
</complexType>
</schema>
Example 3-2 shows how to exclude URLs for OneAPI SMS sendSms and Px21 SMS sendSmsLogo from security checks:
Example 3-2 Exempting OneAPI SMS and Parlay x21 SMS
<?xml version="1.0" encoding="UTF-8"?>
<baseApis xmlns="http://oracle/ocsg/api_firewall/management/xml" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<apis>
<requestUrl>/parlayx21/sms/SendSms</requestUrl>
<method>sendSmsLogo</method>
</apis>
<apis>
<requestUrl_regex>/oneapi/1/smsmessaging/outbound/(.*)/requests</requestUrl_regex>
<method>POST</method>
</apis>
</baseApis>
Implementing Denial-of-Service Attack Protection with ApiFirewall
Your network implementation can be vulnerable to denial of service (DOS) attacks, which generally try to interfere with legitimate communication inside the Services Gatekeeper Access Tier. To prevent these messages from reaching your network, Services Gatekeeper offers configurable SOAP and RESTful message filtering. You configure this filtering behavior by using the ApiFirewall configuration MBean. ApiFirewall determines how Services Gatekeeper filters messages attempting to enter the Services Gatekeeper application tier.
Table 3-1 lists network attacks that Services Gatekeeper protects against, and lists where you can find information about configuring those protections.
Table 3-1 Message-Based Attacks and How to Protect Against Them
| Attack Strategy | Protection Strategy | Default Result |
|---|---|---|
|
Malicious Content Attack, including: SOAP message attacks:
RESTful message attacks:
|
The ApiFirewall MBean settings (application tier) limit the acceptance of oversize message entities. See the ”All Classes” section of Services Gatekeeper OAM Java API Reference for details. |
Rejects the message and returns the error message specified with the ErrorStatus attribute of ApiFirewallMBean. |
|
Continuous wrong password attack. |
The default WebLogic Security Provider setting (application tier) locks a subscriber out for 30 minutes after 5 wrong password attempts. This behavior is configurable. See the section on ”Protecting user Accounts” in Administering Security for Oracle WebLogic Server for more information. |
Rejects the message and returns a 500 Internal Server Error message. |
|
Malformed SOAP Message (does not match the SOAP schema), including:
|
You can direct the WebLogic SOAP message processor (application tier) to validate the SOAP schema and reject malformed messages. See ”Validating the XML Schema” in Oracle Fusion Middleware Getting Started with JAX-WS Web Services for Oracle Weblogic Server for more information. Also, the WebLogic Server SOAP engine ignores any attempt to change the DTD definition in a SOAP message. |
Rejects the message and returns a 500 Internal Server Error message. |
|
Malformed RESTful messages (do not match the REST schema). |
The Jersey parsing engine (network tier) rejects these types of messages. |
Rejects the message and returns a 500 Internal Server Error message. |
|
External Entity Reference |
The Services Gatekeeper ApiFirewall (application tier) prohibits all references to external entities. It is possible to remove this protection. See "Removing External Entity Reference Security" for details. |
Rejects the message and returns a 500 Internal Server Error message. |
Protecting REST APIs with a White List of IP Addresses
This feature allows you to protect your REST-based APIs by limiting access to them to a specific list of trusted IP addresses. You specify the trusted IP addresses using a special key/value pair in a call to the Services Gatekeeper application tier (AT) using the updateAllSysConfig system configurations operation. The prmIPAddressWhitelist key in this operation matches a value that specifies the white list of IP addresses. The key value accepts alpha-numeric characters, dots, and asterisk (*) wildcard character to specify IP addresses, and commas to separate IP address items. Table 3-2 lists some example values to go with the prmIPAddressWhitelist key.
Table 3-2 Example prmIpAddressWhiteList Values
| IP Address Value | IP Addresses in the White List |
|---|---|
|
192.0.2.2 |
Only the 192.0.2.2 address. |
|
192.0.2.* |
All IP addresses that match these first three bytes: 192.0.2. |
|
103.0.113.4,192.0.2.* |
The 103.0.113.4 IP address, and all IP addresses that match these first three bytes: 192.0.2. |
|
103.0.113.4,192.0.2.*,198.* |
The 103.0.113.4 IP address, all IP addresses that match these first three bytes: 192.0.2, and all IP addresses that match this first byte: 198. |
This example call to updateAllSysConfig creates a white list of IP addresses allowed to communicate with Services Gatekeeper. The list includes all IP addresses that use the first byte of 192:
curl
'http://localhost:8001/prm_pm_rest/services/prm_pm/services/partner_manager/sysconfig/updateAllSysConfig'\
-X PUT -H 'Pragma: no-cache' -H 'Origin: http://localhost:7005' -H 'Accept-Encoding: gzip, deflate,
sdch'\
-H 'Accept-Language: en-US,en;q=0.8' -H 'Authorization: Basic b3A6d2VibG9naWMxMjM='\
-H 'Content-Type: application/json' -H 'Accept: application/json, text/javascript, */*; q=0.01'\
-H 'Cache-Control: no-cache' -H 'X-Requested-With: XMLHttpRequest' -H 'Connection: keep-alive'\
-H 'Referer: http://localhost:7005/portal/partner-manager/index/main.html'\
--data-binary '{"updateAllSysConfig":{"sysConfig":[{"key":"obieServerAddress","value":""},
{"key":"obieServerUserName","value":""},{"key":"obieServerPassword","value":"
{AES}tAtwHZPedgVyZISQdjuYng=="},{"key":"mailServerAddress","value":""},
{"key":"mailServerPort","value":""},{"key":"isMailServerSSL","value":"false"},
{"key":"mailServerUsername","value":""},{"key":"mailServerPassword","value":"
{AES}tAtwHZPedgVyZISQdjuYng=="},{"key":"isMailHttpProxy","value":"false"},
{"key":"mailProxyHost","value":""},{"key":"mailProxyPort","value":""},
{"key":"isAutoApprovalReg","value":"true"},{"key":"isAutoApprovalApp","value":"true"},
{"key":"ocsgServerAddr","value":""},{"key":"ocsgServerPort","value":""},
{"key":"ocsgServerSslPort","value":""},{"key":"isOcsgMultiTier","value":"false"},
{"key":"ocsgNtServerAddr","value":""},{"key":"ocsgNtServerPort","value":""},
{"key":"ocsgNtServerSslPort","value":""},{"key":"prmIPAddressWhitelist","value":"192.*"}]}}' --compressed
See "updateAllSysConfig" for more information.
Removing External Entity Reference Security
WARNING:
The instructions in this section remove a key network security feature protecting Services Gatekeeper. Do NOT follow these instructions unless you fully understand the security vulnerabilities and are sure that your implementation is immune to them.
By default, Services Gatekeeper does not allow references to external entities. You can use this Java system property to remove this protection:
oracle.ocsg.api_firewall.isSupportingExternalEntities=true
Linux example:
JAVA_OPTIONS="${JAVA_OPTIONS} -Doracle.ocsg.api_firewall.isSupportingExternalEntities=true"
Windows example:
set JAVA_OPTIONS=%JAVA_OPTIONS% -Doracle.ocsg.api_firewall.isSupportingExternalEntities=true
Implementing Network Traffic Security for APIs
Securing network traffic between your Services Gatekeeper API management system and the users and applications that connect to it involves these general categories:
Authenticating Users and Applications
This section explains how to authenticate the users and applications that connect Services Gatekeeper to access your APIs.
Authenticating Applications
To authenticate applications, you select a security method when you create the API. The choices depend on the type of API you creating, and include:
-
None - In some cases you can create an API that does not require authentication.
-
Text - Authenticates using a username and password.
-
OAuth - Protects third-party resources using security tokens.
-
Appkey - Authenticates using an application key.
See ”Securing Services Gatekeeper Methods and API Services” in Services Gatekeeper API Management Guide for more information on these options.
Authenticating Users
For authenticating users you configure one or more of the WebLogic server security providers by using the Administration Console. Follow these general steps to configure a WebLogic security provider:
-
Start the Administration Console.
See ”Starting and Using the Administration Console” in Services Gatekeeper System Administrator's Guide for details
-
In the Domain Structure pane, navigate to Security Realms, then realm_name (myrealm by default), and click Providers.
The Authentication tab displays the list of Authentication Providers (security providers).
-
Configure one or more provider to authenticate users.
Note:
If the provider has a Control Flag setting (JAAS flag), choose the Optional option, so Services Gatekeeper will also use the API application authorization setting (text, OAuth, or Appkey). That is, simply authorizing the user is insufficient protection; you also need to authorize the application using the API authorization method. -
Save your changes and release the configuration.
For more information on WebLogic security providers and instructions on how to configure them in ”Configuring WebLogic Security Providers” in Fusion Middleware Securing Oracle WebLogic Server.
Using Threat Protection OAM Interfaces
Threat protection works over multiple requests, reacting to repeated violations of some sort.
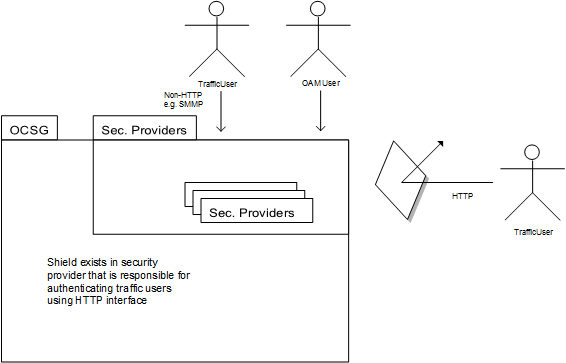
A shield is an entity that blocks requests. It operates on TrafficUser-protected resources that are accessed by HTTP or HTTPS, as illustrated in Figure 3-1. Threat protection puts reporters and shields in place for DAF traffic, and for some other HTTP based traffic, but not in native SMPP.
In code a shield is an implementation of the Shield interface and keeps track of blocked entities. The following example illustrates Shield implementations:
//Check if account is blocked; if so, do not authenticate this account.
if (instance != null) {
if (GenericShield.INSTANCE.isBlocked(TrackedEntities.APP_INST_ACCOUNT.name(),
instance.getName())) {
throw new HttpProcessorViolationException(
DenyCodes.BLOCKED_THREAT.getErrorCode());
}
}
//Another example
if (GenericShield.INSTANCE.isBlocked(TrackedEntities.IP.name(),
GenericReporter.resolveIp(request))) {
throw new HttpProcessorViolationException(
DenyCodes.BLOCKED_THREAT.getErrorCode());
} else {
return null;
}
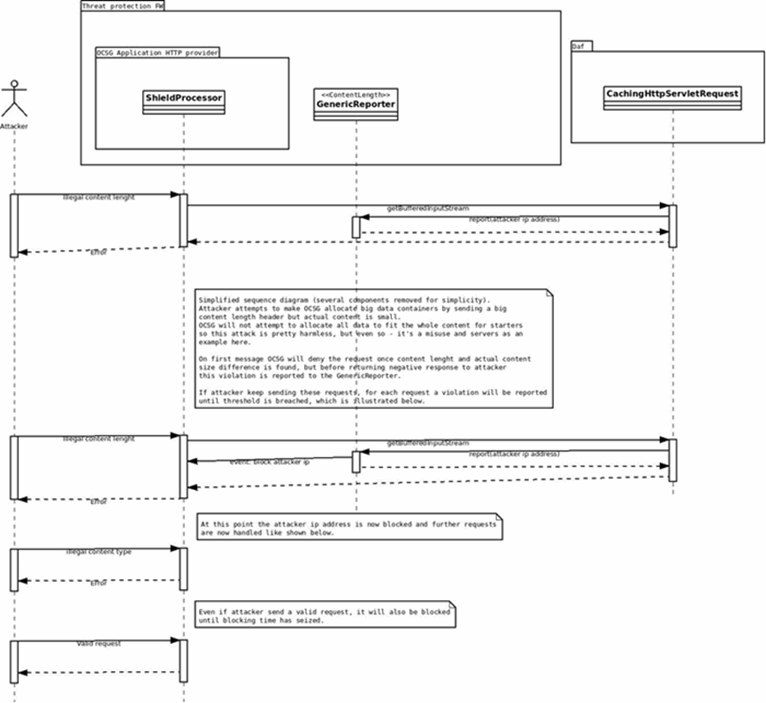
Figure 3-2 shows how a reporter and shield work together to identify and block a potential threat.
Note:
In the web services case (e.g. ParlayX), call flow is to first arrive at API FW, then security providers. In DAF, it's first security providers and then API FWTable 3-3 lists reporters and their locations:
| Location | Reporter / Threat | Tracked Entity |
|---|---|---|
|
SLAEnforcementAction (NT level) |
SlaViolation |
Application instance account |
|
CachingHttpServletRequest (AT level) |
ContentLength & MaxMessageSize |
IP |
|
AppKeyHttpProcessor (AT level) |
AppKeyLoginFail |
IP |
|
LoginFail |
IP |
|
|
ApiFwFail |
IP Application instance account |
Table 3-4 lists shields and their locations:
| Shield | Tracked Entity |
|---|---|
|
ShieldHttpProcessor (AT level) |
IP |
|
AbstractHttpProcessor (AT level) |
Application instance account |
Event Channel Usage
There are two types of threat protection events: configuration events and shield events.
Configuration Events
The reporter and shield MBeans publish configuration to the reporter and shield actuators upon startup. On update, the MBeans publish changes from attribute or operation invocations. The actuators request a configuration push on startup so that it does not matter whether AT or NT is started first. The actuators get the configuration in either case.
Note:
Configuration is stored in the database configuration store.Caches
Both reporters and shields use volatile caches, using the class com.tangosol.net.cache.LocalCache. The following example constructs a cache in which cUnits is the number of units that the cache manager will cache before pruning and cExpiryMillis is the number of milliseconds that each cache entry lives before being expired.
LocalCache public LocalCache(int cUnits, int cExpiryMillis)
The caches used by reporters track the number of violations that an entity performs; the caches used by shields hold the blocked entities.
Note:
The cache is not persistent or recoverable when the server restarts.OAM Interfaces
There are two operation and maintenance (OAM) interfaces for threat protection - a Reporter interface and a Shield interface.
Reporter Interface
Services Gatekeeper sets FullThreadsConfiguration by default which supports the following operations:
-
GetFullThreatConfiguration: Returns the full JSON configuration for s threat definition.
-
UpdateThreatConfiguration: Update the configuration for a threat (in JSON format).
The Reporter interface allows you to define the following per threat type:
-
How to define a threat - for example, x violations of type y over time z.
-
What entity to track, for example IP or user account
-
If IP, from where to pull IP
-
-
How to report the threat violation - that is, alarm, block or both
The following example shows the Reporter interface:
/* Copyright (c) 2018, Oracle and/or its affiliates. All rights reserved. */
package oracle.ocsg.threat_protection;
import com.bea.wlcp.wlng.api.storage.configuration.ConfigurationException;
/**
* MBean for reporter.
*/
public interface ReporterMBean {
String INSTANCE_NAME = "ThreatProtection";
String SHARED_STORE = "shared_config";
String SERVICE_NAME = "Reporter";
String MBEAN_CONFIG_CHANNEL = "reportermbean";
String MBEAN_CONFIG_EVENT = "reporterconfig";
String MBEAN_CONFIG_EVENT_REQUEST = "reporterconfigreq";
String KEY_IP_HTTP_HEADER = "KEY_IP_HTTP_HEADER";
void setIpHttpHeader(String header) throws ConfigurationException;
/**
* Read only CSV list of available actions that can be taken on threat
* violations.
*/
String availableActions = "";
String getAvailableActions();
/**
* Read only CSV list of available entities that can be tracked on threat
* violations.
*/
String availableEntities = "";
String getAvailableEntities();
/**
* Brief description of all threats (Name, Action, Description)
*/
String briefThreatsConfiguration = "";
String getBriefThreatsConfiguration();
/**
* Full Reporter configuration in JSON format.
*/
String fullThreatsConfiguration = "";
String getFullThreatsConfiguration();
/**
* When tracking violations based on originating IP the IP address will be taken
* from this HTTP header.If empty string is configured the ip address will be
* taken from HttpServletRequest.getRemoteAddr()
*
* Using a HTTP header can be suitable if there is a load balancer between
* applications and OCSG.
*
* Note! OCSG makes no processing of the supplied value in the HTTP header.
* eg, if we have X-Forwarded-For configured here and we get a request
* containing this
*
* X-Forwarded-For: 203.0.113.195, 70.41.3.18, 150.172.238.178
* the full string (203...178) will be considered to be the offending "ip".
* This will be fine as long as subsequent messages travel the same route.
*/
String ipHttpHeader = "";
String getIpHttpHeader() throws ConfigurationException;
/**
* Update the configuration for one threat in JSON format.
*
*
* <ul>
* <li><strong>Scope</strong>: Cluster</li>
* </ul>
* Example JSON content:
* {
* "name":"AppKeyLoginFail",
* "actions":[
* "ALARM",
* "BLOCK"
* ],
* "trackedEntities":[
* "IP"
* ],
* "maxTrackedEntities":10000,
* "maxViolations":10,
* "violationClearTime":30,
* "description":"APPKEY login failure, only applicable for IP entity."
* }
*
* Attributes explained:
*
* name - The name of the threat, see getBriefThreatsConfiguration() to see
* which are available.
*
* actions - Empty array if no action should be taken.
* see getAvailableActions() to see which actions are available.
*
* trackedEntities - Empty array if no entities should be tracked (ie same
* effect as haveing no actions enabled)
* see getAvailableEntities() to see which entities are
* available
*
* maxTrackedEntities - Per tracked entity type, the maximum number of entities
* to track violations for.
* Each tracked entity reside in volatile memory on each AT server and is
* cleared on restart.
* If more violations are coming from more entities than we can track, the
* entity that has the oldest violation will be removed from tracked entity.
*
* maxViolations - The maximum allowed violations (eg failed APPKEY logins).
* If maximum allowed violations is reached, the next violation
* will trigger configured actions.
*
* violationClearTime - The number of seconds that need to elapse before an
* entity violations are cleared.
* This timer is reset each time a violation happens.
*
* description - Textual description of this configuration, eg explains what
* would cause this protection to trigger.
*
* Note! Violations can be cleared by time (violationClearTime), or other threat
* specific situation, for example APPKEY violations are cleared if a successful
* login is performed.
* Note! Once a block action has been triggered violations cannot be cleared by
* violationClearTime. Block will be in effect for as long as the shield is
* configured.
* Note! Violations are tracked separately on each server, but once shield is
* raised it is raised on all nodes.
* Note! The maxTrackedEntities isn't an exact value, real value can be bigger
* depending on internal purge algorithm.
* Note! All entities might not be supported for all threats, ie protections
* prior to authentication can not track APP_INST_ACCOUNT for example, as no
* account has been authenticated yet.
*
* @param json configuration in JSON format.
* @throws ConfigurationException if there is an issue when storing.
*/
void updateThreatConfiguration(String json) throws ConfigurationException;
}
Shield Interface
The following example shows the Shield interface:
/* Copyright (c) 2018, Oracle and/or its affiliates. All rights reserved. */
package oracle.ocsg.threat_protection;
import com.bea.wlcp.wlng.api.storage.configuration.ConfigurationException;
/**
* Shield MBean interface.
* A shield is raised in order to block a specific entity, eg. IP:130.243.31.1.
* The MBean keeps the common configuration shared by all Shields.
*/
public interface ShieldMBean {
String SERVICE_NAME = "Shield";
String MBEAN_CONFIG_CHANNEL = "shieldmbean";
String MBEAN_CONFIG_EVENT = "shieldconfig";
String MBEAN_CONFIG_EVENT_REQUEST = "shieldconfigreq";
/**
* The time to keep the shield up in minutes.
* <ul>
* <li><strong>Scope</strong>: Cluster</li>
* <li><strong>Default value</strong>: Integer: 30 minutes</li>
* </ul>
*/
int shieldUpTime = 30;
int getShieldUpTime() throws ConfigurationException;
void setShieldUpTime(int minutes) throws ConfigurationException;
/**
* The maximum number of endpoints that can be blocked at the same time.
* Note! This isn't an exact value, real value can be bigger depending on purge
* timers.
*
* <ul>
* <li><strong>Scope</strong>: Cluster</li>
* <li><strong>Default value</strong>: Integer: 100 endpoints</li>
* </ul>
*/
int maximumEntitiesToBlock = 100;
int getMaximumEntitiesToBlock() throws ConfigurationException;
void setMaximumEntitiesToBlock(int entities) throws ConfigurationException;
/**
* Unblock a blocked entity.
* @param entity the entity type, see ReporterMBean for available types.
* @param name The entity to unblock.
*/
void unBlock(String entity, String name);
}
Alarms
The following three alarms have been added:
<alarm-group id="921" name="threatProtection" description="Alarms emitted by threat protection framework"> <alarm id="921001" severity="warning" description="Threat protection violation, will block violator"> <filter> <attribute key="Shielded" value="true"/> </filter> </alarm> <alarm id="921002" severity="warning" description="Threat protection violation, will not block violator"> <filter> <attribute key="Shielded" value="false"/> </filter> </alarm> <alarm id="921004" severity="warning" description="Request blocked by threat protection"> <filter> <attribute key="DenyCode" value="200"/> </filter> </alarm> </alarm-group>
Usage
Alarm 921004 occurs when a request is blocked. In the following example, a request from application instance account appkey_Password1 was blocked as indicated by the APP_INST_ACCOUNT attribute.
{
"DenyCode":"200",
"Position":"after",
"Method":"",
"TransactionId":"b1aa38c7-67a3-497a-8a75-feb350a6d81c",
"Class":"ErrorServlet",
"Processors":"\"seq=0, name=TrafficThrottler, status=Success, new_principals=0\", \"seq=1, name=ShieldHttpProcessor, status=Success, new_principals=0\", \"seq=2, name=CORSProcessor, status=Success, new_principals=0\", \"seq=3, name=AppKeyHttpProcessor, status=Deny, code=200\"",
"APP_INST_ACCOUNT":"appkey_Password1",
"Timestamp":"1507977661843",
"URL":"",
"Source":"Exception",
"TagAlarm":"921004",
"ServerName":"Server1"
}
In this example, a request from IP address 130.243.31.1 was blocked as indicated by the IP attribute.
{
"DenyCode":"200",
"Position":"after",
"IP":"130.243.31.1",
"Method":"",
"TransactionId":"d4e018af-acd9-4c36-b0d0-0a581561d818",
"Class":"ErrorServlet",
"Processors":"\"seq=0, name=TrafficThrottler, status=Success, new_principals=0\", \"seq=1, name=ShieldHttpProcessor, status=Deny, code=200\"",
"Timestamp":"1507977772755",
"URL":"",
"Source":"Exception",
"TagAlarm":"921004",
"ServerName":"Server1"
}
Alarm 921001 occurs when the number of violations has reached maxViolations + 1 and as a result the violator is blocked. The time between two violations never exceeded violationClearTime. The following example shows the alarm where attribute Threat holds the violation AppKeyLoginFail.
{
"Shielded":"true",
"IP":"130.243.31.1",
"Class":"ViolationHelper",
"Timestamp":"1507977772393",
"TagAlarm":"921001",
"ServerName":"Server1",
"Threat":"AppKeyLoginFail"
}
Alarm 921002 occurs when the number of violations has reached maxViolations + 1 and the time between two violations never exceeded violationClearTime but the violator is not blocked. alarm where we can see that attribute Threat holds the violation AppKeyLoginFail.
Note:
This alarm is emitted from the NT layer so you need to have EDR typepublish_enabler_edr set to true in order to see these. The default value of publish_enabler_edr is false.
{
"Shielded":"false",
"DenyCode":"44",
"ReqAction":"[\"seq=1, name=OAuth2Validator, status=Success\"]",
"Position":"before",
"ServiceProviderId":"partner",
"TransactionId":"e09ecf72-0610-4154-829d-658a4f580b0f_IDX_3",
"ServiceName":"/ECHOServer/1",
"State":"ENTER_NT",
"Class":"ViolationHelper",
"ApplicationId":"weather",
"Processors":"\"seq=0, name=TrafficThrottler, status=Success, new_principals=0\", \"seq=1, name=ShieldHttpProcessor, status=Success, new_principals=0\", \"seq=2, name=CORSProcessor, status=Success, new_principals=0\", \"seq=3, name=AppKeyHttpProcessor, status=Success, new_principals=2\"",
"TsBeAT":"1508158225153",
"HttpMethod":"POST",
"APP_INST_ACCOUNT":"appkey_Password1",
"TsBeNT":"1508158225153",
"Timestamp":"1508158225153",
"Direction":"south",
"Source":"method",
"URL":"/ECHOServer/1/echo",
"ServiceProviderGroup":"gold",
"AppInstanceId":"appkey_Password1",
"TagAlarm":"921002",
"APPEnforcers":"\"seq=0, name=RequestContextParamsEnforcer, status=Success\", \"seq=1, name=BlacklistedMethodsEnforcer, status=Success\", \"seq=2, name=MethodParametersEnforcer, status=Success\", \"seq=3, name=FilterResultEnforcer, status=Success\", \"seq=4, name=MethodEnforcer, status=Success\", \"seq=5, name=BudgetEnforcer, status=Deny, code=44\"",
"ServerName":"Server1",
"ApiId":"ECHOServer",
"ReqMsgSize":"36",
"Threat":"SlaViolation"
}
Extending Threat Protection
As a developer, you need to think about how a feature you are developing can be abused and protect against it. You can follow these steps to add a reporter:
-
Define the threat
Add an
enumtooracle.ocsg.threat_protection.Threats. -
Add a reporter that uses this Threat; you can track based on IP or application instance account:
-
IP:
GenericReporter.getInstance(Threats.THE_NEW_THREAT).report(TrackedEntities.IP, GenericReporter.resolveIp(httpReq)); -
Account:
GenericReporter.getInstance(Threats.THE_NEW_THREAT).report(TrackedEntities.APP_INST_ACCOUNT, RequestContextManager.getCurrent().getCurrentAppInstanceGroupId());
-
You can also add new shields. The shield needs to use the following three event channels. See the implementation of GenericShield implementation if you want to create another shield.
-
Request configuration push
-
Receive configuration push
-
Receive block and unblock events