2 Session Monitor Secure Configuration
This document covers the necessary configuration of the Oracle Communications Operations Monitor system and of its environment to ensure secure operations. To follow these recommendations, you need access to Platform Setup Application (PSA) and to all the installed products, their manual, and possibly the administration tools for your networks.
Administrative Password
PSA must be protected by a password of your choice on all Operations Monitor machines. All the session products come with an administrator account to access their respective interface. To restrict access to these products, connect to their interface, and change the administrator account password on each. For administrator user credentials, contact your Oracle Sales Representative.
User Accounts
Operations Monitor features fine-grained multi-user capabilities which allows the administrator to create restricted accounts for day-to-day usage. Referring to each product manual, create one account for each person who uses the product, and set their permissions to allow their necessary tasks. You need to set a temporary password and communicate it with the end users, who should then change it. It is possible to force a user to do so by expiring its password. It is recommended to enforce a strict passwords policy by enabling the features and regularly expire passwords.
Encryption and Certificates
Each Operations Monitor server uses a unique certificate to guarantee its authenticity and protect users data. The certificates are initially self-signed, and a warning will be shown to users on their first access. To improve security of the connection and suppress these warnings, it is recommended that you sign the server certificate using your organization's Public Key Infrastructure (PKI). Follow the steps on the Server Certificate screen, and consult with your network administrator to sign the certificates of each Operations Monitor server. Plain HTTP access is not allowed.
Connections with Oracle SBCs
In Operation Monitor connections from Oracle SBCs to ME machines are encrypted. These connections use TLS on port 4740. Unsecure connections are not allowed by default, unless the system has been upgraded from an earlier release that did not support it. Authentication is achieved by means of certificates. In a stand- alone scenario, you can register the SBC certificate in Platform Setup Application as a trusted certificate, and register Operations Monitor certificate in the SBC. If you prefer to manage certificates within a PKI, you can instead sign these certificates, and register the trusted Certificate Authority (CA) in each machine.
On the SBC
Follow instructions in the Oracle Support note to:
-
Configure the connection to Operations Monitor
-
Create a certificate for the SBC
-
Register the certificate of Operations Monitor, which can be downloaded from PSA on the panel Server Certificate. Alternatively, register the CA used to sign it.
-
Enable TLS
In PSA
In PSA, go to the panel, Trusted Certificates. Use the form to upload the certificate(s) of the SBC(s), which then appear in the list of trusted certificates. Alternatively, upload the CA that is used to sign SBCs certificates. The certificate format is X.509 / PEM. X.509 extensions are not supported, only the validity of signatures is verified.
Unsecure Option
If you do not wish to use encrypted connections, for instance for testing, you can allow unsecure connections from SBCs on the Trusted Certificate panel. You can then disable the TLS option in the SBC. These connections will use port 4739. However, this setup is not recommended in production.
Connection between ME and MEC
The MEC machines can access the ME machines using HTTPS. Make sure that the urls entered in the AE to reach the ME machines start with https://.
Email Notifications
Session Monitor products can send notification emails. For this, it require access to an SMTP server, configurable with PSA. If the server requires authentication, an account needs to be created for Oracle Communications Operations Monitor. This account should not grant any other privileges that the product does not require. Session Monitor also supports TLS connections to the SMTP server.
Connections with ISR
Connection with ISR is performed using HTTPS protocol. Operations Monitor interacts with the external system and the complete security feature depends on both parties configurations. Hence, it is recommended to use FACE server hostname only with HTTPS protocol scheme.
Connection with Fraud Monitor (FDP)
Connections from Oracle Communications Operations Monitor to the Oracle Communication Fraud Monitor are encrypted. These encrypted (secure) connections use TLS on port 12000 on Fraud Monitor. The secure connections between the Operations Monitor and the Fraud Monitor are established using SSL Certificates.
The connection between ME and Fraud Monitor is secured for which the certificates need to be exchanged. See Connection with Fraud Monitor (FDP) related to Fraud Monitor Configuration to download certificate.
-
Ensure that Fraud Monitor certificate has been downloaded from Fraud Monitor PSA Server Certificate page. The certificate can either be a self-signed certificate or CA certificate.
-
In ME PSA, navigate to Trusted Certificates, upload the certificate downloaded from Fraud Monitor PSA Server Certificate page.
-
In ME PSA, navigate to Server Certificate, download the Server Certificate.
-
In Fraud Monitor PSA, navigate to Trusted Certificate, upload the certificate downloaded from ME PSA Server Certificate page.
Note:
The supported format of the server certificate is PEM. -
After the successful certificate exchange configure the FDP URL at admin >Setting >General Settings >Fraud Monitor.
Note:
The username and Password must be same as the FDP Username and Password used for login to Fraud Monitor.Figure 2-1 Fraud Monitor configuration Page
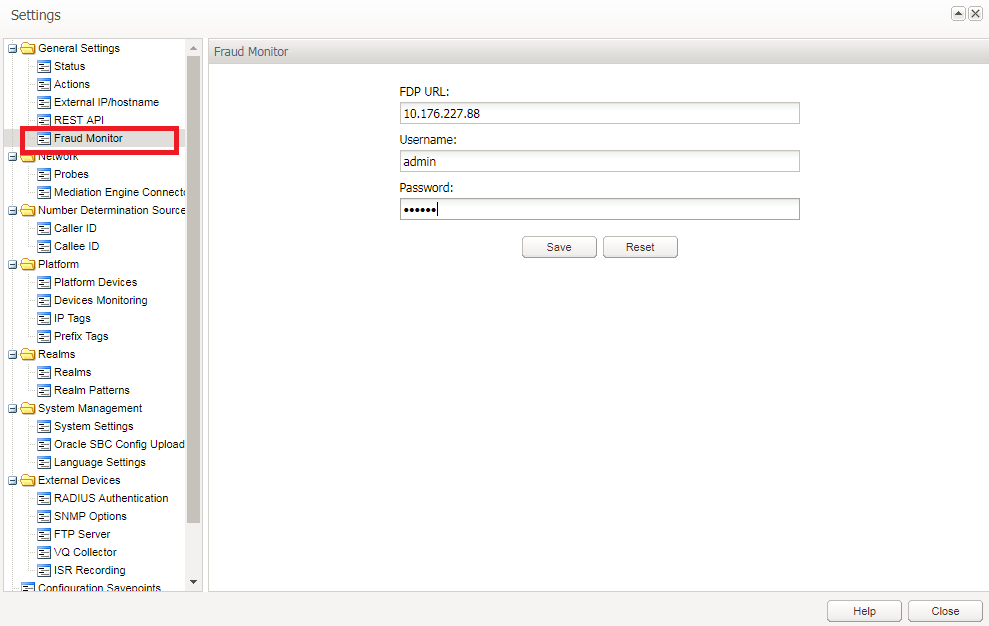
Description of ''Figure 2-1 Fraud Monitor configuration Page''
-
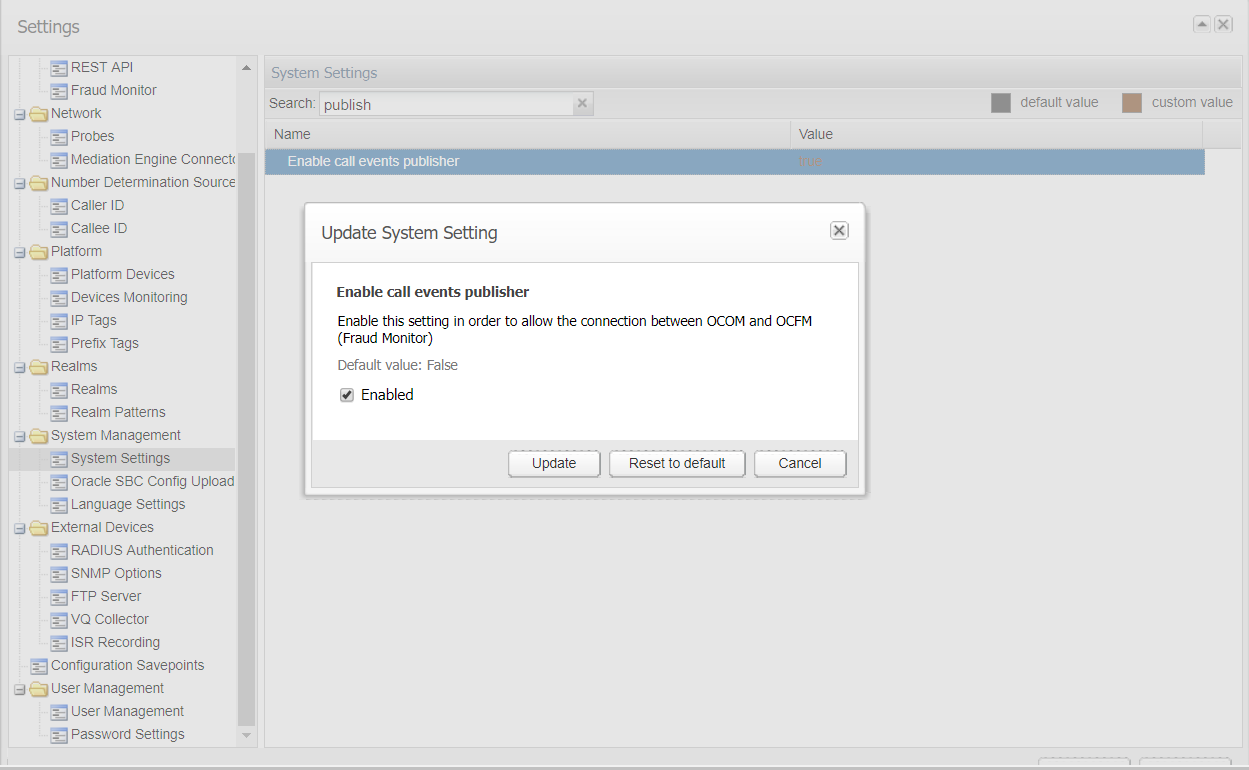
The Operations Monitor initiates secured (TLS) connection to Fraud Monitor, if Fraud Detection is enabled from the below path admin >Settings >System Settings >Enable call Events publisher