4 Performing a Secure Session Monitor Installation
This chapter presents planning information for your Oracle Communications Session Monitor installation.
For information about installing Session Monitor, see Session Monitor Installation Guide.
Pre-Installation Configuration
Perform the following pre-installation tasks:
-
Ensure that the Session Monitor machine is reachable through the TCP port 443.
-
If the E-mail SMTP server supports authentication, create an account dedicated to Session Monitor.
-
Session Monitor acts as an SNMP device. Obtain the address and community string of the SNMP management system.
Installing Session Monitor Securely
Perform a custom installation to avoid installing options and products you do not need. If you perform a typical installation, remove or disable features that you do not need after the installation.
When installing Session Monitor, do the following:
-
Change the password when prompted.
-
On the Network Settings page, enable monitoring only on necessary interfaces.
-
On the SMTP Page:
-
If your SMTP server supports TLS, make sure to enable TLS.
-
If your SMTP server supports authentication, make sure to enable authentication and to use an account dedicated to Session Monitor.
-
-
On the Date & Time page, (if your organization runs an NTP server) make sure to provide the IP address of the local and redundant NTP servers.
Post-Installation Configuration
This section explains security configuration to complete after Session Monitor is installed.
Changing the Default Administrator Passwords
All Session Monitor products (Operations Monitor, Fraud Monitor, and Mediation Engine Connector) are installed with a default admin account. The admin account is used to access the product's Web interface. On first login, the administrator is prompted to choose a unique password for the admin account. Fraud Monitor currently does not prompt to choose a password; the administrator should change the password manually.
You can also connect to each product's Web interface and change the admin account password at any time.
The Platform Setup Application is installed with a default sysadmin account. On each Session Monitor machine, log into the Platform Setup Application, and change the sysadmin account password.
Encryption and Certificates
All Session Monitor interfaces can only be accessed through encrypted (secure) HTTPS connections. Each Session Monitor machine uses a unique certificate to establish secure connections and to guarantee its authenticity and protect users' data.
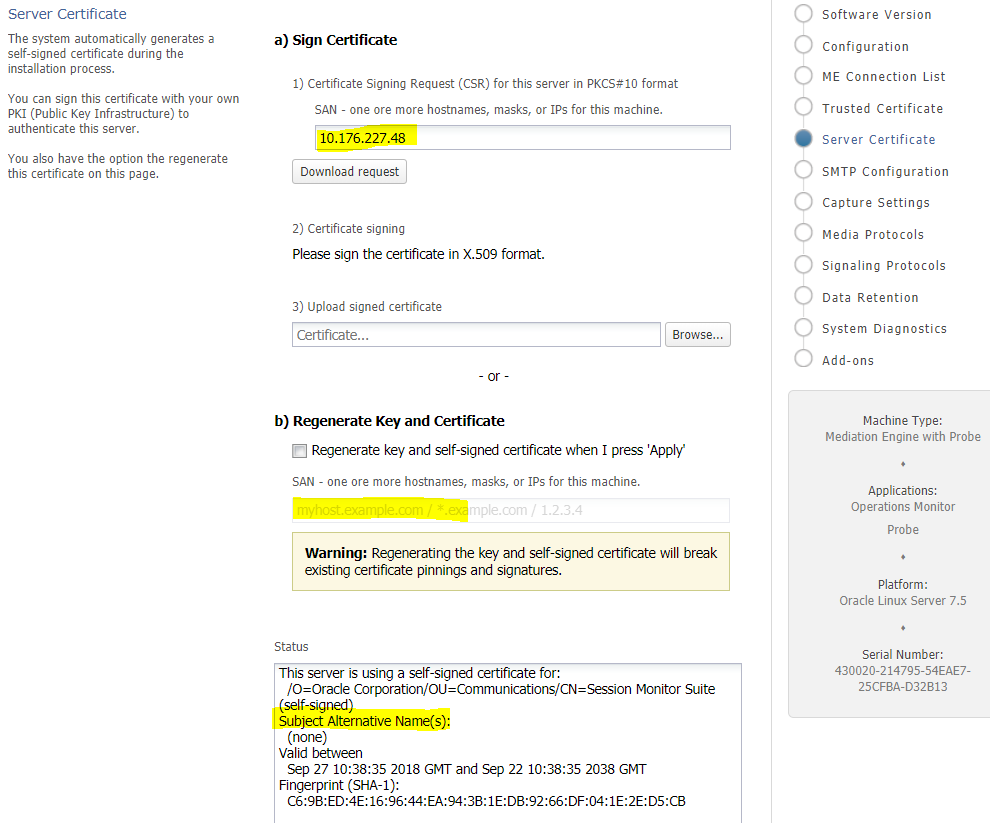
The certificates are automatically generated on the Session Monitor machines during the installation process. The certificates are initially self-signed, and when a user accesses the interface the first time, a This Connection is Untrusted warning message is shown. To improve security of the connections and to suppress the warning message, Oracle recommends that you sign the server certificate using your organization's Public Key Infrastructure (PKI).
Consult with your network administrator and follow the steps on the Server Certificate page in Platform Setup Application to sign the certificates of each Session Monitor machine.
Enable Skip hostname validation for HTTPS connection when using self-signed certificates that were generated during installation.
Figure 4-1 shows the Server Certificate page in Platform Setup Application.
The Status of the Server Certificate from Platform Setup Application, Subject Alternative Name(s): (none) indicates that SAN is not defined.
On the Trusted Certificate page, the list of trusted certificates also displays the SAN for each certificate.
Connection Between Mediation Engine and Aggregation Engine
The Aggregation Engine machines can only access the Mediation Engine machines using HTTPS. Make sure that the URLs entered in the Aggregation Engine to access the Mediation Engine machines start with https://.
For a successful secure connection between Mediation Engine and Mediation Engineer Connector each machine has to have a valid certificate for the other machine. This can be either the certificate found on the Server Certificate page of the other machine (self-signed) or the corresponding CA certificate (of the CA that signed the certificate).
For more information, see Session Monitor Mediation Engine Connector User's Guide.
Connection Between Mediation Engine and Interactive Session Recorder
Mediation engine requires a valid Interactive Session Recorder certificate to establish secure and validated connection. The supported certificate format is PEM.
For more information, see Oracle Communications Operations Monitor User's Guide.