Monitoring Key Usage
Learn how to monitor key usage in Oracle Cloud Infrastructure using log data.
Monitoring the use of keys for encrypt and decrypt operations can be valuable for several use cases, including the following:
- Lifecycle management: Understanding when a key was last used is critical for making informed retention decisions. Infrequently used keys, such as those supporting database workloads, might still be operationally important despite limited activity. Extending log retention through OCI Connector Hub enables deeper visibility into historical usage patterns, letting teams make risk-aware decisions about whether to retain, rotate, or retire keys.
- Security: Monitoring key usage can alert you to unusual activity.
- Monitoring or investigating application behavior: Correlating application behavior with key usage can give you useful information for resolving issues with your applications or improving their performance.
This topic details how you can use Oracle Cloud Infrastructure (OCI) logs to monitor key usage.
Available Logging Data
The OCI Logging Service provides several kinds of logs, including the following:
Audit Logs
Audit Logs: Use audit logs to monitor management operations such as:
- Create, update, and delete operations for managing keys and vaults
- Rotate operations for keys
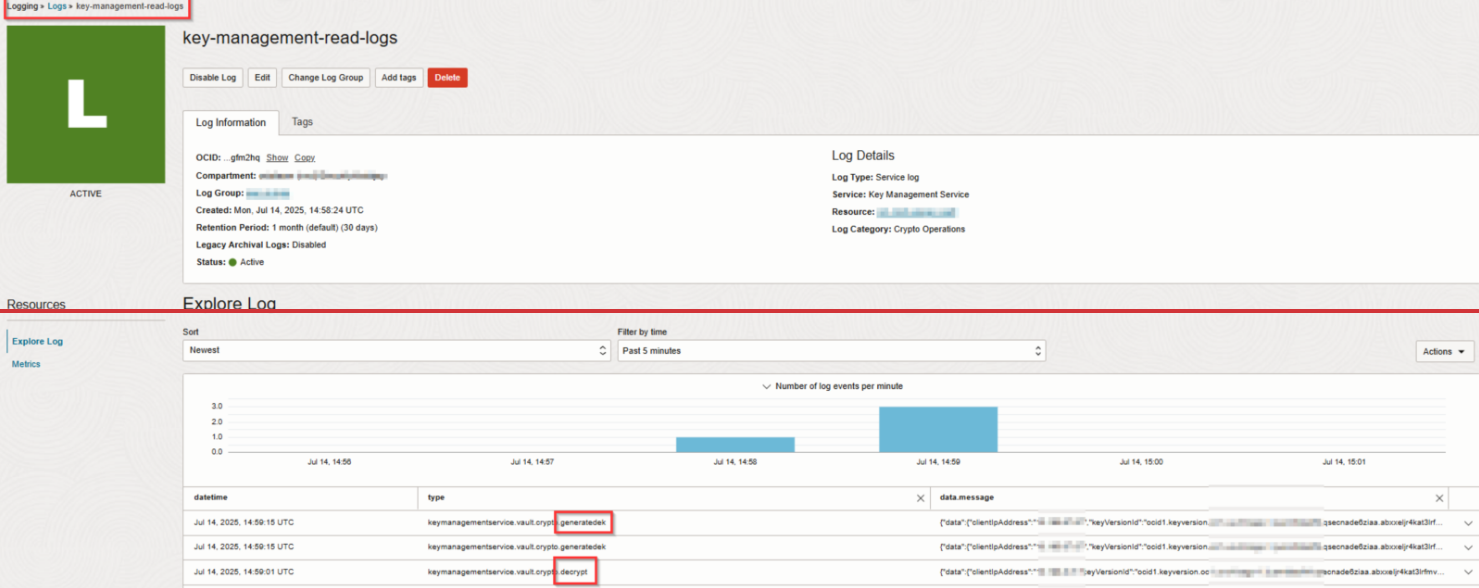
Audit logs do not record cryptographic operations such as Decrypt or GenerateDataEncryptionKey (data plane activity), which are instead optionally recorded in Service Logs.
Service Logs
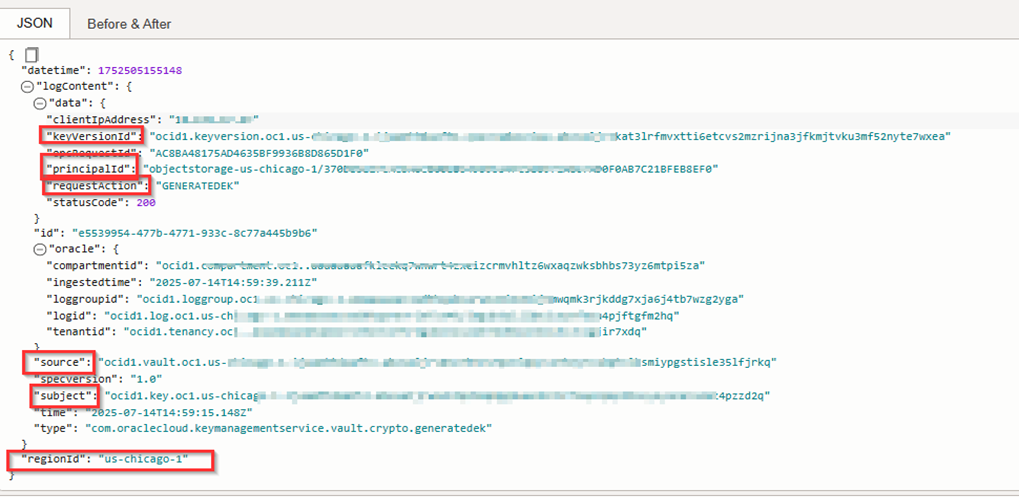
Service Logs must be enabled by the customer to be used. When enabled for Key Management, service logs capture metadata including:
- Calling principal (the user, function, or instance that instigates the key operation)
- Key OCID
- Key version
- Operation type (for example,
Decrypt) - Timestamp
- Vault and compartment details
Service logs don't record sensitive information that would compromise data security for your organization or your customers. See Details for Key Management for complete details on the data that service logs collect for Key Management.
Enabling Service Logs for a Vault
To enable service logs, you need the required IAM permissions. See Details for Logging in the IAM Service documentation for information.
Note that service logs are enabled at the vault level. Repeat the steps in this topic for each regional vault for which you want to enable logging.
See Enabling Logging for a Resource in the Logging Service documentation for more information.
View and Query KMS Logs
Sending Logs to Object Storage or External Platforms Such as SIEM
By default, service logs are stored for 30 days. For long-term retention or external analysis, use Connector Hub to forward logs to target destinations such:
- Object Storage
- Log Analytics
- External targets such as SIEM
See the following topics for more information: