DNS
Learn about Domain Name System (DNS) configuration and management for Oracle Database@Google Cloud.
DNS is the system that translates human-readable domain names (such as Oracle.com) into machine-readable IP addresses, which computers use to identify one another on a network. Instead of remembering complex numerical IP addresses, users can enter a domain name and DNS handles the lookup behind the scenes. DNS enables seamless access to websites and services, ensures the scalability of the Internet, and allows traffic to be routed efficiently. Without DNS, we would need to memorize IP addresses for every online resource we want to access.
To support domain name resolution, Oracle Database@Google Cloud utilizes Cloud DNS forwarding, allowing Google Cloud workloads to resolve fully qualified domain names (FQDNs) of databases hosted in OCI private subnets.
During the deployment, a Google Cloud Cloud DNS Zone is created to map the Oracle Database@Google Cloud resources FQDN:
*.oraclevcn.comfor Exadata and BaseDB*.oraclecloud.comand*.oraclecloudapps.comfor ADB
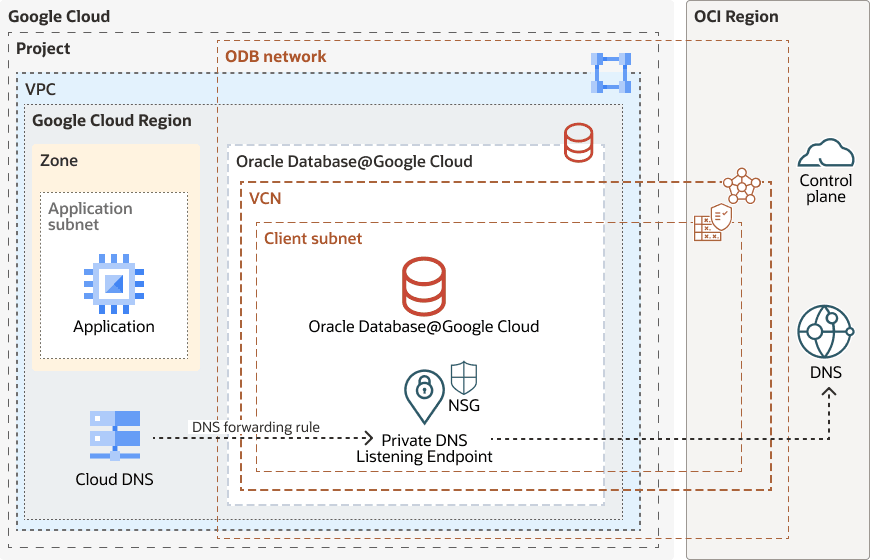
Google Cloud-Side DNS Forwarding
On the Google Cloud side, DNS resolution is enabled using Cloud DNS:
-
A Google Cloud private DNS Zone is deployed in the Google Cloud project and associated with the VPC of the selected ODB network.
-
Forwarding rules are configured in Google Cloud Cloud DNS, directing queries for Oracle-managed domains to the OCI DNS Listener IP received during provisioning.
-
This setup ensures that any DNS query originating from the Google Cloud VPC for a database FQDN is forwarded securely and resolved within the OCI VCN.
OCI-Side DNS Provisioning
When an Oracle Database@Google Cloud resource is created in OCI as part of a database deployment, the following DNS components are automatically provisioned:
-
DNS Resolver: Created per VCN to enable internal DNS resolution.
-
Private DNS View: A default view is automatically created and managed by the resolver.
-
Private DNS Zones:
-
Each subnet (primary and backup) in the VCN receives an associated private DNS zone.
-
-
DNS Listener Endpoint:
-
Provisioned per VCN, the listener IP is allocated in the primary subnet.
-
Each listener is governed by an independent Network Security Group (NSG) rule, allowing precise control over ingress IPs and ports automatically created during provisioning.
-
While it's technically possible to share a single listener across all DB attachments in a VCN, this would prevent deletion or reallocation of the originating subnet until all associated resources are removed.
-
In the following diagram, the Google Cloud Cloud DNS Zone is forwarded to the OCI Private DNS Listening endpoint created during the Oracle Database@Google Cloud deployment and associated with the Private resolver, default Private view, and Private zone to the OCI VCN to resolve the name and IP in the OCI DNS service.
To learn more, see Configure.
- To create a Google Cloud DNS peering zone. DNS zone peering allows managed zones in one project/VPC to be shared with others.
- To forward DNS resolution from OCI to Google Cloud to resolve a non-OCI domain name.