About Master Encryption Key Management on Autonomous AI Database
Autonomous AI Database provides two options for Transparent Data Encryption (TDE) to encrypt your database: Oracle-managed encryption keys and Customer-managed encryption keys.
Autonomous AI Database uses Transparent Data Encryption, including a TDE master key and TDE tablespace keys to encrypt data in the database. As shown in the following figure, the TDE master key generates and encrypts/decrypts the TDE tablespace keys, and the TDE tablespace keys encrypt the data files.
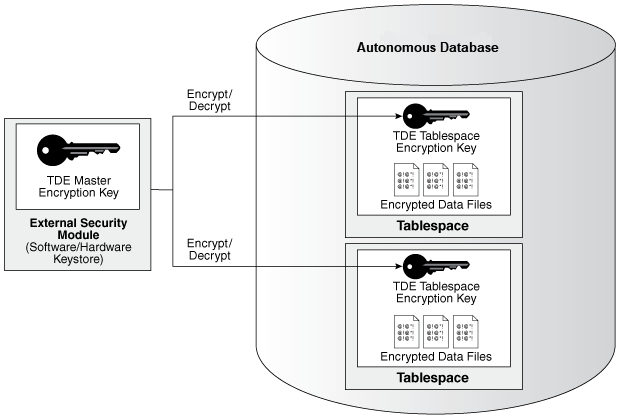
Description of the illustration adb_kms_keys.png
Oracle-Managed Master Encryption Keys on Autonomous AI Database
By default, Autonomous AI Database uses Oracle-managed encryption keys.
Using Oracle-managed keys, Autonomous AI Database creates and manages the encryption keys that protect your data and Oracle handles rotation of the TDE master key.
Customer-Managed Master Encryption Keys on Autonomous AI Database
- Oracle Cloud Infrastructure (OCI) Vault
See Manage Master Encryption Keys in OCI Vault for more information.
- Microsoft Azure Key Vault
See Manage Master Encryption Keys in Azure Key Vault for more information.
- Amazon Web Services (AWS) Key Management Service (KMS)
See Manage Master Encryption Keys in AWS Key Management Service for more information.
- Oracle Key Vault (OKV)
See Manage Master Encryption Keys in Oracle Key Vault for more information.
Parent topic: Manage Encryption Keys on Autonomous AI Database