Explore the OCI GoldenGate deployment console
The OCI GoldenGate deployment console is the interface you use to create, manage, and monitor GoldenGate processes.
You launch the OCI GoldenGate deployment console from a deployment's Actions (ellipsis icon) menu on the Deployments page, or from the deployment's details page. Log in with the Oracle Cloud Infrastructure GoldenGate username and password that you specified when you created the deployment.
After you log in successfully, you're brought to the OCI GoldenGate deployment console Administration Service Overview.
WARNING:
You must only create and edit connections in the Oracle Cloud console. Refrain from creating or editing connections in the Credentials screen of the deployment console. Updates are automatically synced to the deployment from the Oracle Cloud console.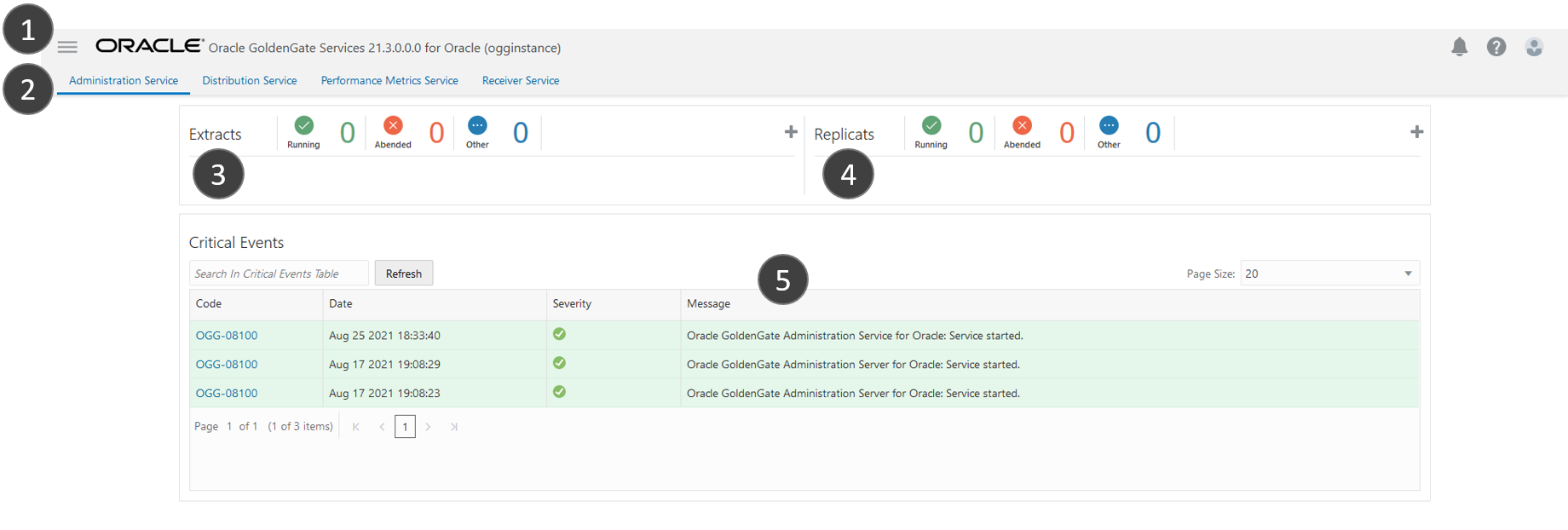
The main areas of the Administration Service Console are:
- Navigation menu: Click the navigation icon to show or hide the navigation menu.
- The navigation bar lets you switch between the following services:
- Administration Service: (currently shown) Administers, manages, and monitors Extract and Replicat processes within an Oracle GoldenGate deployment.
- Distribution Service: A networked data distribution agent that conveys and processes data and commands in a distributed deployment environment.
- Performance Metrics Service: Collects and stores deployment performance results.
- Receiver Service: Interoperates with the Distribution Server to handle all incoming trail files.
- Extracts: Displays the number of running, failed, or other Extracts. Click Add Extract (plus icon) to create a new Extract.
- Replicats: Displays the number of running, failed, or other Replicats. Click Add Replicat (plus icon) to create a new Replicat.
- Critical Events: Displays the severity of critical events.