Vulnerability Scanning Overview
Oracle Cloud Infrastructure Vulnerability Scanning Service helps improve your security posture by routinely checking hosts and container images for potential vulnerabilities. The service gives developers, operations, and security administrators comprehensive visibility into misconfigured or vulnerable resources, and generates reports with metrics and details about these vulnerabilities including remediation information.
All Vulnerability Scanning resources and reports are regional, but scan results are also visible as problems in your Cloud Guard global reporting region.
The Vulnerability Scanning service identifies vulnerabilities in the following resources:
- Compute instances (also known as hosts)
- Container Registry images
The Vulnerability Scanning service can identify several types of security issues:
- Ports that are unintentionally left open might be a potential attack vector to your cloud resources, or enable hackers to exploit other vulnerabilities.
- OS packages that require updates and patches to address vulnerabilities.
- OS configurations that hackers might exploit.
- Industry-standard benchmarks published by the Center
for Internet Security (CIS).
The Vulnerability Scanning service checks hosts for compliance with the section 5 (Access, Authentication, and Authorization) benchmarks defined for Distribution Independent Linux.
- Vulnerabilities in third-party applications such as
log4jandspring4shell.
Oracle Cloud Infrastructure Vulnerability Scanning Service can help you quickly correct vulnerabilities and exposures, but the service isn't a Payment Card Industry (PCI) compliant scanner. Don't use the Vulnerability Scanning service to meet PCI compliance requirements.
The Vulnerability Scanning service only supports Compute instances, or container images, created from supported platform images. Scanning isn't available for any image with the label end of support.
To scan Compute instances for vulnerabilities, the instance must use an image that supports Oracle Cloud Agent . Port scanning on an instance's public IP address doesn't require an agent.
Vulnerability Scanning host and container image scans might pick up CVE results from other unsupported operating systems. The results are only covered by NVD data, and can be missing CVEs, or have other false positives. We don't support these other operating systems so use these results with caution.
The Vulnerability Scanning service detects vulnerabilities in the following platforms and using the following vulnerability sources.
| Platform | National Vulnerability Database (NVD) | Open Vulnerability and Assessment Language (OVAL) | Center for Internet Security (CIS) |
|---|---|---|---|
| Oracle Linux | Yes | Yes | Yes |
| CentOS | Yes | Yes | Yes |
| Ubuntu | Yes | Yes | Yes |
| Windows | Yes | No | No |
Because Windows scanning doesn't include OVAL data, we don't recommend you rely solely on Oracle Cloud Infrastructure Vulnerability Scanning Service to ensure that your Windows instances are up-to-date and secure.
We don't recommend using the Vulnerability Scanning service to identify issues in Virtual Machine DB Systems, and then modifying the OS to address each issue. Instead, follow the instructions at Updating a DB System to apply the latest security updates to the OS.
You can't use the Vulnerability Scanning service on hosts that weren't created directly with the Compute service, such as Exadata Database Service on Dedicated Infrastructure or the Database service. Use the features provided with those services to ensure that hosts have the latest security updates.
The Vulnerability Scanning service supports the following target options:
- Individual Compute instances
- All Compute instances within a compartment and its
subcompartments.
If you configure the Vulnerability Scanning service at the root compartment, then all Compute instances in the entire tenancy are scanned.
- Images within a Container Registry repository
Concepts
Understand key concepts and components related to the Vulnerability Scanning service.
The following diagram provides a high-level overview of the service.
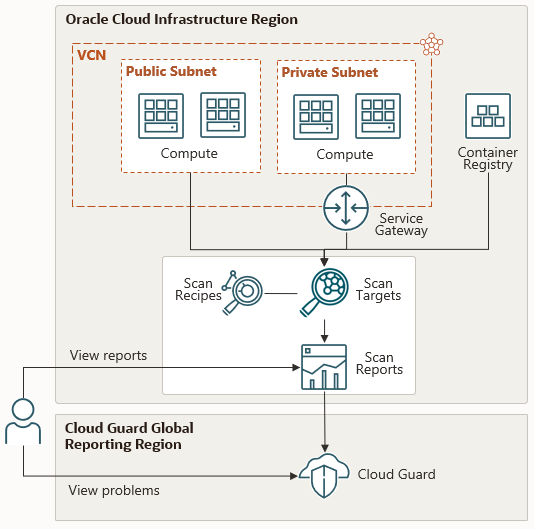
- Scan Recipe
- Scanning parameters for a type of cloud resource, including what information to examine and how often.
- Target
- One or more cloud resources that you want to scan using a specific recipe. Resources in a target are of the same type, such as Compute instances.
- Host Scan
- Metrics about a specific Compute instance that was scanned, including the vulnerabilities that were found, their risk levels, and CIS benchmark compliance.
The Vulnerability Scanning service uses a host agent to detect these vulnerabilities.
- Port Scan
- Open ports that were detected on a specific Compute instance that was scanned.
The Vulnerability Scanning service can detect open ports using a host agent, or using a network mapper that searches your public IP addresses .
- Container Image Scan
- Metrics about a specific Container Registry image that was scanned, including the vulnerabilities that were found and their risk levels.
- Vulnerabilities Report
- Information about a specific type of vulnerability that was detected in one or more targets, like a missing update for an OS package.
Integration with Cloud Guard
You can view security vulnerabilities identified by the Vulnerability Scanning service in Oracle Cloud Guard.
Cloud Guard is an Oracle Cloud Infrastructure service that provides a central dashboard to monitor all of your cloud resources for security weakness in configuration, metrics, and logs. When it detects a problem, it can suggest, assist, or take corrective actions, based on your Cloud Guard configuration.
Like the Vulnerability Scanning service, Cloud Guard uses recipes and targets.
- A recipe defines the types of problems that you want Cloud Guard to report
- A target defines the compartments that you want Cloud Guard to monitor, and is associated with a recipe.
A configuration detector recipe consists of detector rules. The default Cloud Guard configuration detector recipe includes rules that check for vulnerabilities and open ports found by the Vulnerability Scanning service.
For more information, see Scanning with Cloud Guard.
Resource Identifiers
Vulnerability Scanning resources, like most types of resources in Oracle Cloud Infrastructure, have a unique, Oracle-assigned identifier called an Oracle Cloud ID (OCID).
For information about the OCID format and other ways to identify your resources, see Resource Identifiers.
Ways to Access Vulnerability Scanning
You can access Vulnerability Scanning using the Console (a browser-based interface), the command line interface (CLI), or the REST API. Instructions for the Console, CLI, and API are included in topics throughout this guide.
To access the Console, you must use a supported browser. To go to the sign-in page, open the navigation menu at the top of this page and select Infrastructure . You're prompted to enter your cloud tenant, your user name, and your password.
For a list of available SDKs, see SDKs and the CLI. For general information about using the APIs, see REST API documentation.
Authentication and Authorization
Each service in Oracle Cloud Infrastructure integrates with IAM for authentication and authorization, for all interfaces (the Console, SDK or CLI, and REST API).
An administrator in your organization needs to set up groups, compartments , and policies that control which users can access which services, which resources, and the type of access. For example, policies control who can create users, create and manage a VCN (virtual cloud network) , launch instances, and create buckets .
- If you're a new administrator, see Getting Started with Policies.
- For specific details about writing policies for this service, see Vulnerability Scanning IAM Policies.
- For specific details about writing policies for other services, see Policy Reference.
Security
In addition to creating IAM policies, there are other tasks related to the security of Vulnerability Scanning.
For example:
- Configure a service gateway so you can scan hosts without public IP addresses
- Perform a security audit of scanning operations
Monitoring
To monitor scanning activity, Vulnerability Scanning integrates with these other services in Oracle Cloud Infrastructure.
- The Audit service automatically records calls to all public Vulnerability Scanning API endpoints as log entries. See Overview of Audit.
- The Monitoring service enables you to monitor your Vulnerability Scanning resources using metrics and alarms. See Scanning Metrics.
- The Events service allows your development teams to automatically respond when a Vulnerability Scanning resource changes its state. See Scanning Events.
Limits and Quotas
Oracle Cloud Infrastructure limits the maximum number of Vulnerability Scanning resources in your tenancy. You can also use quotas to set limits on specific compartments.
See Vulnerability Scanning Limits and Vulnerability Scanning Quotas.
To request a service limit increase, see Limits by Service.
Getting Started
Use the Vulnerability Scanning service to check for security vulnerabilities in the Compute instances for a single compartment.
If you run into problems, see Troubleshooting the Vulnerability Scanning service.