Overview
A custom authentication module is a Java module that customers develop and implement to authenticate Oracle Enterprise Performance Management System users. Generally, EPM System products use a logon screen to capture the user name and password, which are used to authenticate users. Instead of using EPM System authentication, you can use a custom authentication module to authenticate users and pass authenticated user credentials to EPM System for further processing. Implementing a custom authentication module does not involve modifying EPM System products.
You can use a custom authentication module with both the thick clients (for example, Oracle Smart View for Office, and Oracle Essbase Studio) and thin clients (for example, Oracle Hyperion Enterprise Performance Management Workspace).
The custom authentication module uses the information a user enters when logging in to an EPM System product. If enabled for a user directory, it authenticates users through the custom authentication module. On successfully authenticating the user, the custom authentication module returns the user name to EPM System.
The following illustration presents a sample custom authentication scenario:
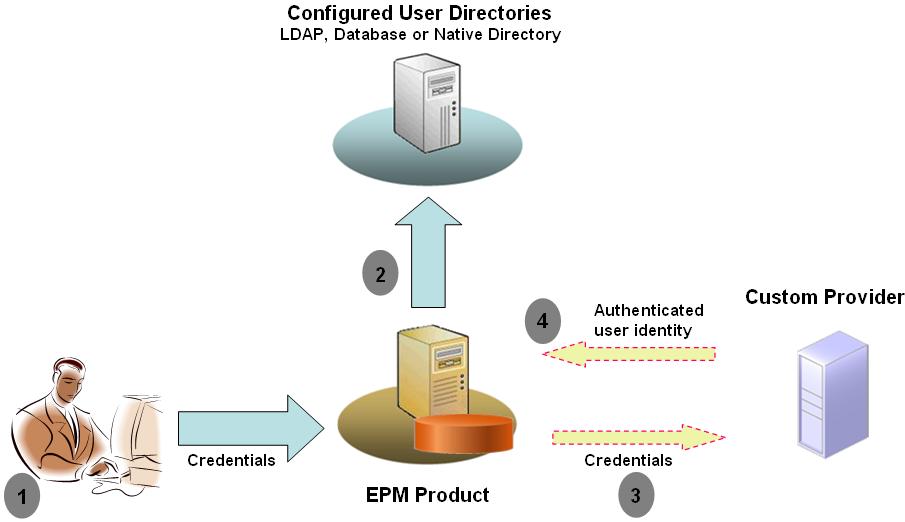
For example, you can use RSA SecurID infrastructure as the custom provider to ensure transparent strong authentication to the EPM System. An overview:
-
The user enters credentials (generally, user name and password) to access an EPM System product. These credentials should uniquely identify the user to the provider used by the custom authentication module. For example, if you are using an RSA SecurID infrastructure to authenticate users, the user enters an RSA user ID and PIN (not an EPM System user ID and password).
-
Using the search order (see Search Order), EPM System cycles through configured user directories to locate the user.
-
If the current user directory is not configured for custom authentication, EPM System tries to locate and authenticate the user through EPM System authentication.
-
If the user directory is configured for custom authentication, EPM System delegates the authentication process to the custom module.
-
-
If EPM System delegates authentication to the custom module, the custom authentication module accepts the credentials and uses its own logic to direct user authentication against a custom provider; for example, RSA SecurID infrastructure.
-
If the custom authentication module authenticates the user against its provider, it returns the user name to the EPM System, or it returns a Java exception.
The user name returned by the custom authentication module must be identical to a user name in a user directory that is enabled for custom authentication.
-
If the custom authentication module returns a user name, EPM System locates the user in a user directory that is enabled for custom authentication. At this stage, EPM System does not search the user directories that are not configured for custom authentication.
-
If the custom authentication module throws an exception or returns a null user, EPM System continues to search for the user in the remaining user directories in the search order that are not enabled for custom authentication. If a user who matches the credentials is not found, EPM System displays an error.
-