SSL for Essbase 21c
Overview
This section explains the procedures for replacing the default certificates that are used to secure communication between an Oracle Essbase instance and components such as MaxL, Oracle Essbase Administration Services Server, Oracle Hyperion Provider Services, Oracle Hyperion Foundation Services, Oracle Hyperion Planning, Oracle Hyperion Financial Management, and Oracle Hyperion Shared Services Registry.
Note:
-
Essbase Administration Services (EAS) Lite does not use the HTTP Server SSL port (for example, 443) configured using the EPM Configurator. The secure URL in the
easconsole.jnlpfile defaults to the non-SSL port (80).Workaround: Replace the default non-SSL port in the secure URL identified in
easconsole.jnlpwith the updated secure URL:Default Secure URL:
https://myserver:SECURE_PORT/easconsole/console.html. Example,https://myserver:80/easconsole/console.htmlUpdated Secure URL:
https://myserver:SECURE_PORT/easconsole/console.html. Example,https://myserver:443/easconsole/console.htmlSee My Oracle Support (MOS) article - Doc ID 1926558.1 - SSL Port Not Included In easconsole.jnlp of the EAS Web Console for more information.
-
Planning's connection to Essbase might not function if SSL is set up for EPM in a Windows environment.
Workaround: Add the following folder path to the
PATHsystem environment variable on the server where Planning is installed.EPM_ORACLE_HOME\bin21C
Default Deployment
Essbase can be deployed to work in SSL and non-SSL modes. Essbase Agent listens on a non-secure port; it also can be configured to listen on a secure port. All connections accessing the secure port are treated as SSL connections. If a client connects to the Essbase Agent on the non-SSL port, the connection is treated as a non-SSL connection. Components can establish concurrent non-SSL and SSL connections to an Essbase Agent.
You can control SSL on a per-session basis by specifying the secure protocol and port when you log in. See Establishing a Per-Session SSL Connection.
If SSL is enabled, all communication within an Essbase instance is encrypted to ensure data security.
Default deployments of Essbase components in secure mode uses self-signed certificates to enable SSL communication, mainly for testing purposes. Oracle recommends that you use certificates from well-known third-party CAs to SSL-enable Essbase in production environments.
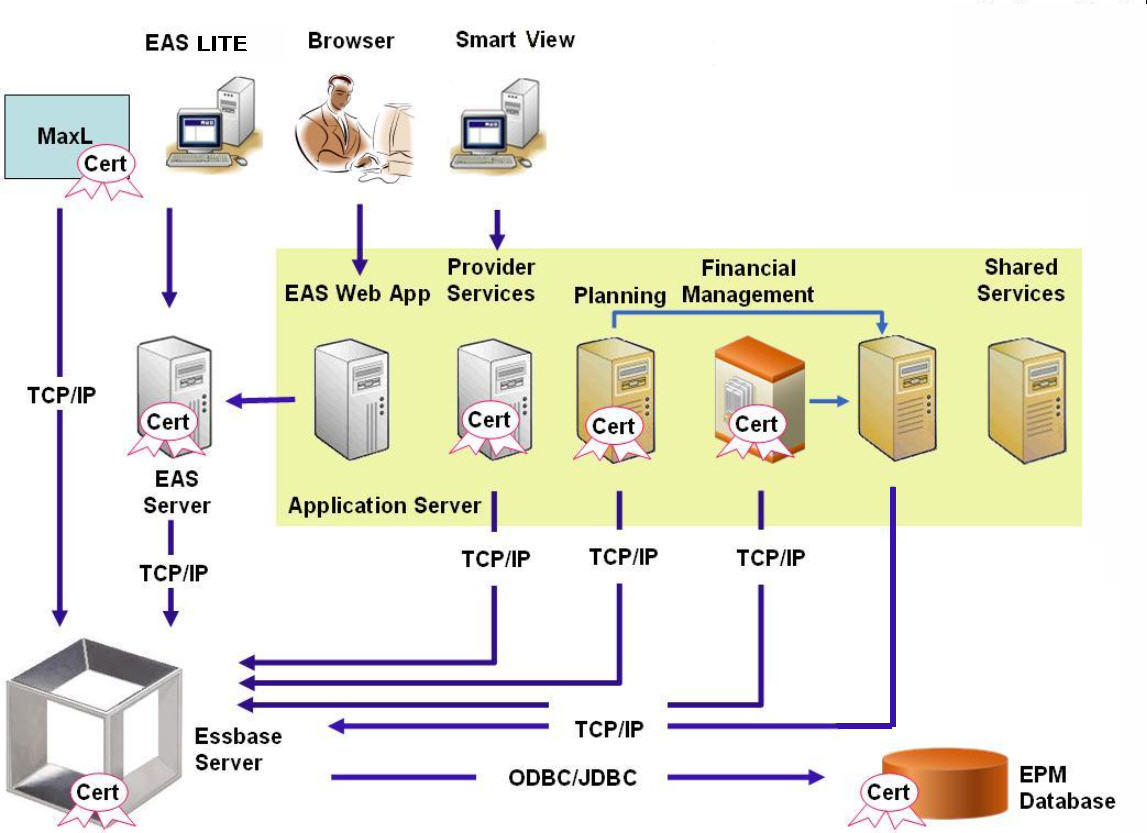
Typically, an Oracle Wallet stores the certificate that enables SSL communication with clients that use Essbase RTC and a Java keystore stores the certificate that enables SSL communication with components that utilize JAPI for communication. To establish SSL communication, Essbase clients and tools store the root certificate of the CA that signed the Essbase Server and Agent certificates.
Required Certificates and Their Location
Oracle recommends the use of certificates from well-known third-party CAs to SSL-enable Essbase in a production environment. You may use the default self-signed certificates for test purposes.
Note:
Essbasesupports certificates that are supported by OpenSSL.
You require the following certificates:
- A root CA certificate.
Components that use Essbase RTC to establish a connection to Essbase require that the root CA certificate be stored in an Oracle Wallet. Components that use JAPI to establish a connection require that the root CA certificate be stored in a Java keystore. The required certificates and their locations are indicated in the following table.
Note:
You may not need to install root CA certificate if you are using certificates from a well-known third-party CA whose root certificate is already installed in Oracle Wallet.
- Signed certificate for Essbase Server and Essbase Agent.
Table 2-4 Required Certificates and Their Locations
| Component1 | Keystore | Certificate 2 |
|---|---|---|
| MaxL | Oracle Wallet | Root CA certificate |
| Administration Services Server | Oracle Wallet | Root CA certificate |
| Provider Services | Oracle Wallet | Root CA certificate |
| Oracle Enterprise Performance Management System Database | Oracle Wallet | Root CA certificate |
| Planning |
|
Root CA certificate |
| Financial Management | Java Keystore | Root CA certificate |
| Essbase (Server and Agent) 3 |
|
|
| Oracle Hyperion Shared Services Repository | ||
|
1 You need only one instance of the keystore to support multiple components that use a similar keystore. 2 Multiple components can use a root certificate installed in a keystore. 3 Certificates must be installed in the default Oracle Wallet and in the Java keystore. |
||